What is Suricata?
Suricata is an open-source network intrusion detection and prevention system (IDS/IPS). It is intended to monitor network traffic and detect a variety of threats, including malware, intrusion attempts, and network anomalies. Using a rule-based language, Suricata analyzes network packets in real time, allowing it to identify and respond to suspicious or malicious activities. The non-profit organization OISF (Open Information Security Foundation) owns and develops Suricata.
Suricata can also be deployed as an IPS in order to detect and block malicious traffic to the organization. Although IPS deployment might sound like the obvious option, unfortunately, it isn’t that friendly; it often blocks legitimate traffic as well if they aren’t configured properly. And yes, this is why the detection approach is sometimes better than the prevention approach.
You can download Suricata from the following link: https://suricata.io/download/.
There are multiple use cases of Suricata IDS; some of the important use cases are as follows:
- Network traffic monitoring: Suricata analyzes real-time network traffic for threats and anomalies. Organizations need to smartly deploy Suricata at various points in the network to analyze both incoming and outgoing traffic. This use case can help us detect malware, Distributed Denial of Service (DDoS) attacks, port scans, reconnaissance data exfiltration, and so on.
- Signature and anomaly detection: Suricata detects known attack patterns or signatures by checking network traffic against a library of rules and patterns that have already been set up. In this chapter, we will use the Suricata ruleset created by the Emerging Threats (ET) community. This ruleset can help us detect known malware, viruses, web-based attacks (SQL Injection, cross-site scripting attacks, etc.), known network attack signatures, and so on.
- Protocol analysis: Suricata can deeply examine many different network technologies, such as HTTP, DNS, and TLS. This helps us to discover anomalous behaviors of protocols, such as unusual HTTP requests, DNS tunneling, and unexpected SSL/TLS handshakes.
- Logging and alerting: Suricata keeps logs and sends out alerts when it detects possible threats. These alerts can be used to get security teams to act right away, or they can be added to security information and event management (SIEM) systems so that they can be analyzed further and linked to other security events. Wazuh, Splunk, Elastic, and all the popular SIEM solutions support integration with the Suricata IDS.
Let’s learn about the deployment methods of the Suricata IDS.
How organizations use Suricata as an IDS
There are several ways to deploy the Suricata IDS and some of the important and popular deployment methods are explained in the following:
- Inline deployment at network perimeter: Suricata sits between the external internet connection and the internal network, actively monitoring and scrutinizing network traffic in real time. It can be deployed as a physical appliance or as a virtual machine (VM). The network traffic passes through Suricata, which analyzes the packets and acts based on the criteria that have been defined.
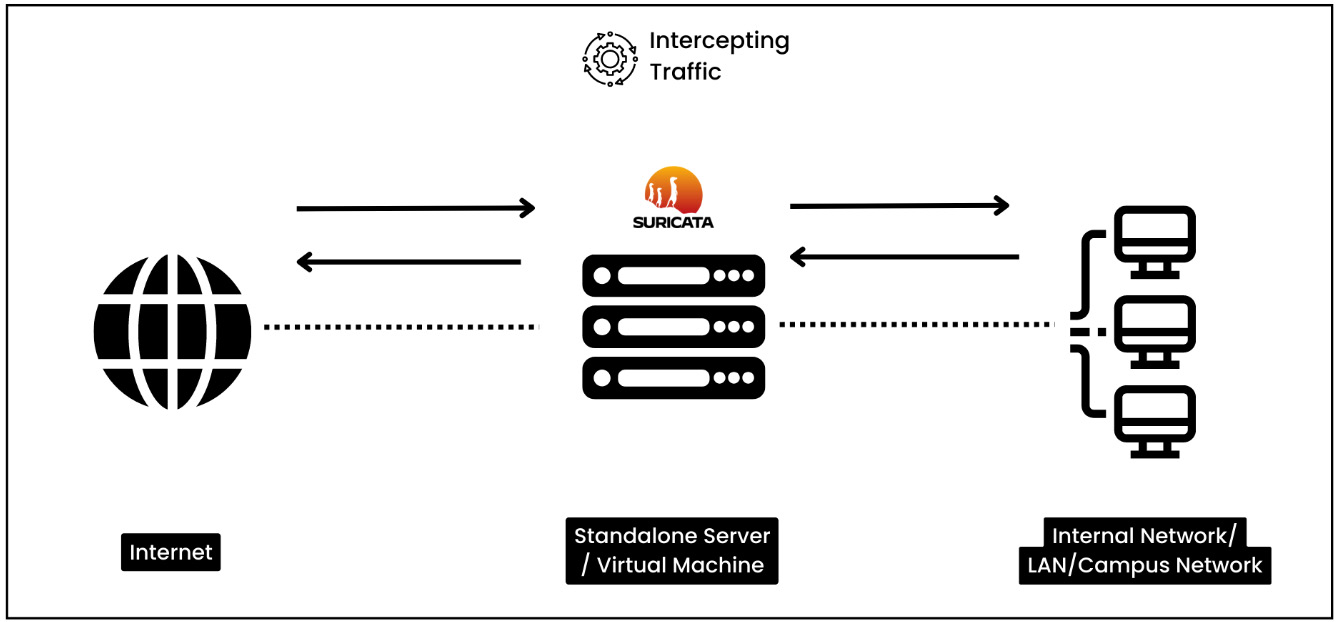
Figure 1.2 – Inline deployment at network perimeter
- Internal network monitoring: Suricata sensors are strategically located within the internal network in order to capture network traffic between segments or departments. These sensors could be physical or virtual devices. They analyze the captured traffic and transmit alerts or records to a centralized management system for additional analysis and response. As you can see in the following diagram, the sensors will export the data to a centralized server.
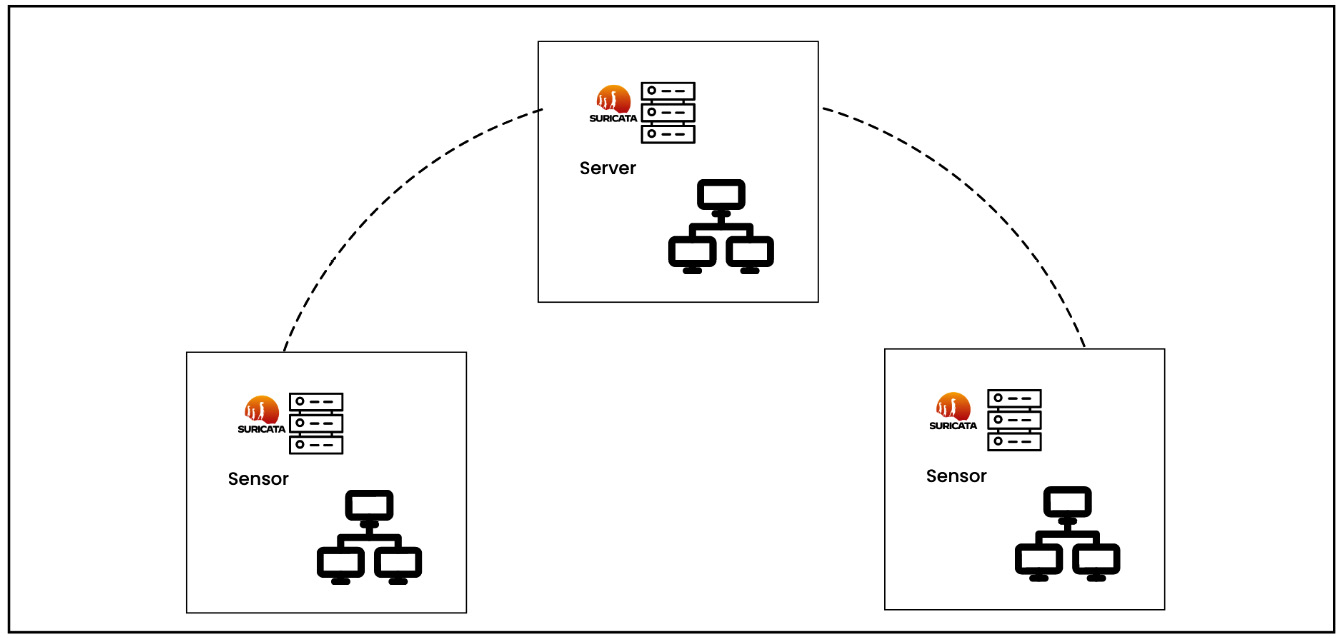
Figure 1.3 – Internal network monitoring
- Cloud environment monitoring: Suricata can be deployed as virtual appliances or containers in AWS and Azure cloud environments. It is installed within the cloud infrastructure and monitors network traffic within virtual networks and between cloud resources. The captured traffic is transmitted to a central analysis system for response detection.
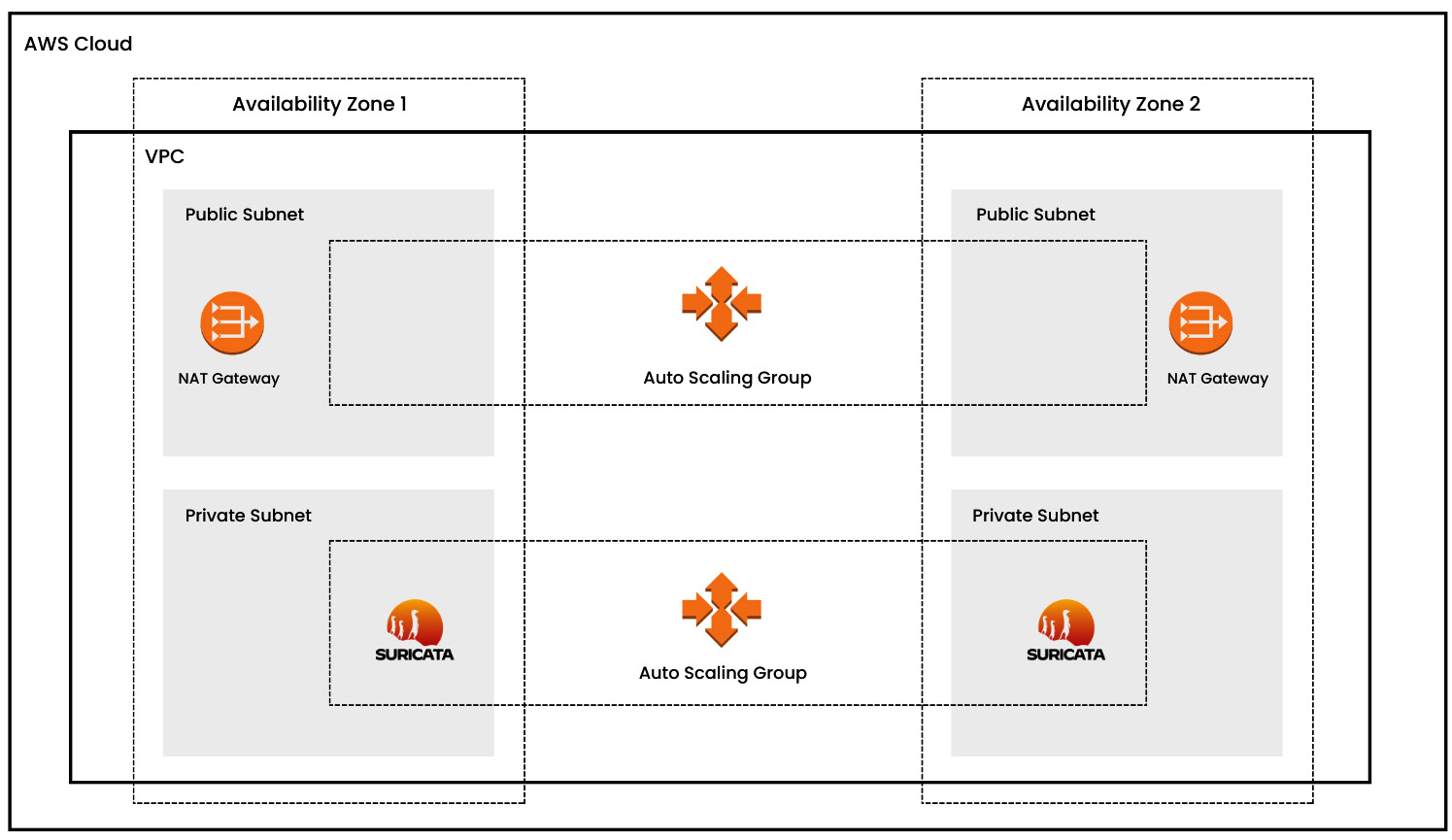
Figure 1.4 – Cloud security monitoring (AWS)
- Network tap deployment: Suricata is used in conjunction with network taps or port mirroring. Taps are strategically located at key network nodes to capture a copy of network traffic, which is then sent to Suricata for analysis. This deployment ensures accurate and comprehensive network activity visibility.
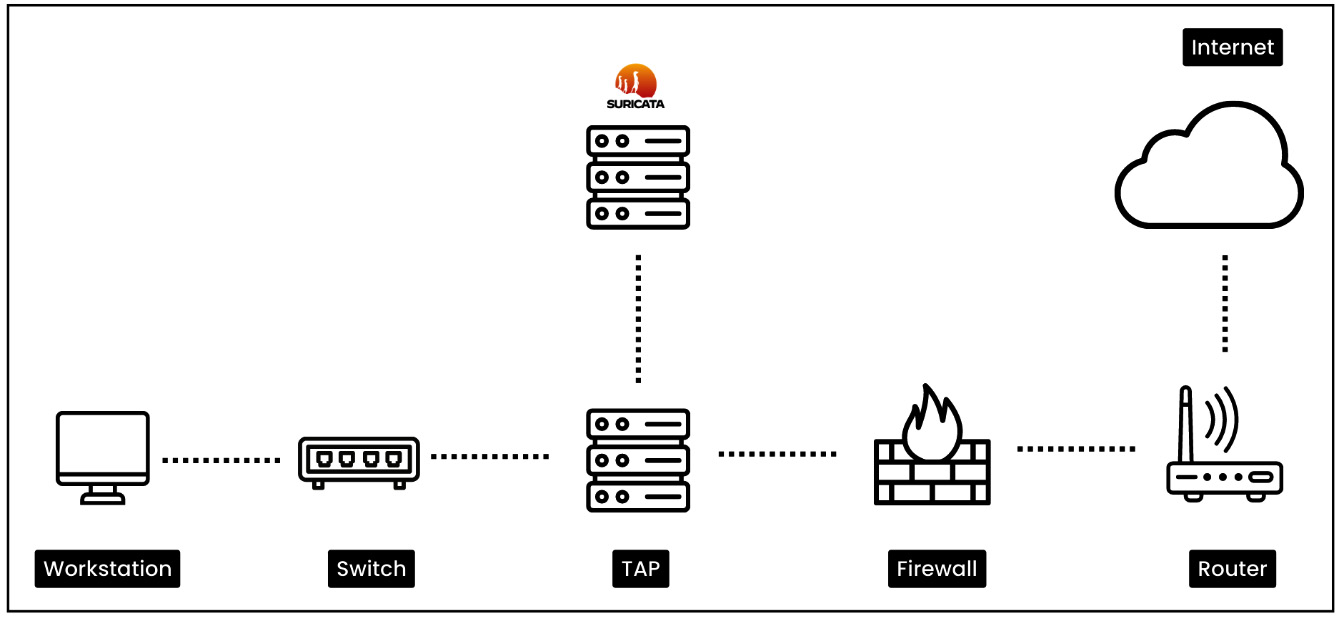
Figure 1.5 – Network tap deployment
We have learned about the different Suricata deployment methods. In the next section, we will learn about Wazuh, its core components and deployment methods, and then we will learn how to install Suricata IDS on Ubuntu Server.
































































