Creating Entra ID static groups
Now that our new user has been configured, we need a way to assign our policies to them and any machines they may use. For this, we need to configure Entra ID groups, which come in two flavors – static and dynamic.
If you are familiar with traditional Active Directory groups, these are very similar, except they include dynamic groups, where a group is populated automatically based on a particular query or filter that has been configured.
Getting ready
First, load the Entra portal, expand Groups, and click on All Groups (you can also access groups within the Intune portal, which loads the same window).
How to do it…
A static group is pretty straightforward to use – you manually add either users or devices to it:
- Click on New Group and enter the necessary details. Set Group type to Security and enter Group name and Group description values. If you want to be able to assign roles directly to the group instead of at the user level (for example, you want a group of Intune administrators), change the setting to Yes. Set Membership type to Assigned. Optionally, add any members and an owner to manage the group. Then, click Create.
- Once your group has been created, click on it to look at some of the other actions you can take against it. You can also get an overview of the group membership, as well as the group ID:
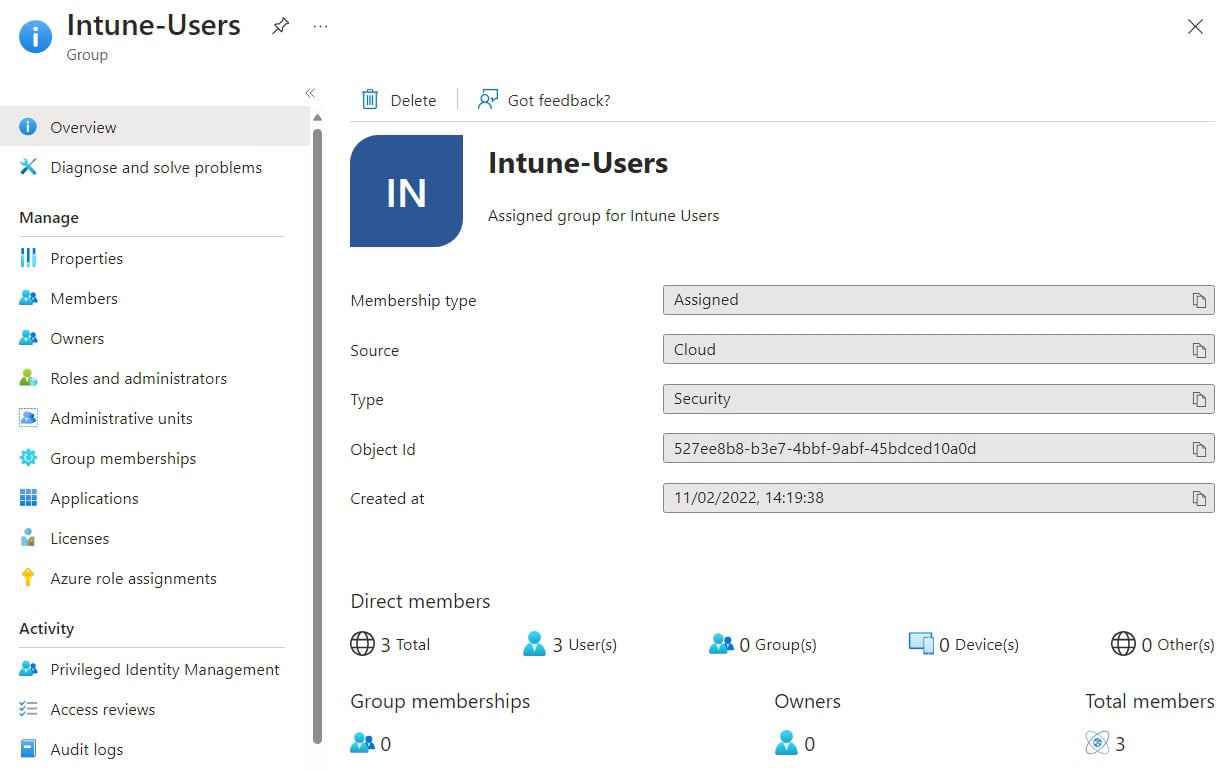
Figure 1.7– Entra ID group menu
Members and Owners are pretty self-explanatory. Administrative units is a useful feature if you want to delegate within your environment. Say, for example, you want your service desk to be able to perform tasks on a particular group of users – you can create an administrative unit and assign users and groups to it. You can then configure a custom Azure role with specific access only to that administrative unit. Group memberships is for nested groups. Clicking the Licenses option allows you to assign a license at a group level rather than directly to the users. If you selected Yes earlier, you can also assign Azure roles to the group in the Azure role assignments menu.
With that, you have created a static Microsoft Entra group.
Automating it
Creating this PowerShell script will automate your Entra group creation process, which will be useful when you need to bulk-create groups during your tenant management.
This is a fairly easy one to automate:
- As usual, we need to start with the variables:
$groupname = "TestGroup123" $groupdescription = "TestGroupDescription"
- Convert the group name into lowercase and remove any special characters so that we can use it as the mail nickname:
$groupnickname = ($groupname -replace '[^a-zA-Z0-9]', '').ToLower()
- Set the URL. Here, we are using the Groups subsection of Graph:
$uri = "https://graph.microsoft.com/beta/groups/"
- Populate the JSON. We do not need mail for this group as it is for Entra ID and Intune membership only and it is a security group, so we need to pass this through:
$json = @" { "description": "$groupdescription", "displayName": "$groupname", "mailEnabled": false, "mailNickname": "$groupnickname", "securityEnabled": true } "@ - Send the command to create the group:
Invoke-MgGraphRequest -Uri $uri -Method Post -Body $json -ContentType "application/json"
This can also be completed by using the
New-mgGroupmodule and passing variables through if required.
You now have a script to create your static Entra groups automatically.
































































