Scenario 1 – warming Adobe ColdFusion
Adobe ColdFusion is the Adobe framework for hosting web applications. It's available for a 30-day evaluation trial, is easy to set up, and creates remotely accessible web pages—perfect for our purposes.
Setup
First, take your freshly installed or sanitized Windows installation and download Adobe ColdFusion 9. There are newer versions available from adobe.com, but we will be working with version 9, which you can download from http://download.macromedia.com/pub/coldfusion/updates/901/ColdFusion_update_901_WWEJ_win64.exe. Now, perform the following steps:
- Run the
.exefile to install the program, and use the defaults as you go along. - Make sure you perform the following steps:
- Set Adobe ColdFusion 9 to host as a self-contained application as the following screenshot shows:

- Set the application to run a built-in server, as shown in the following screenshot:

- Set default credentials throughout as shown in the following screenshot, and make a note of them:

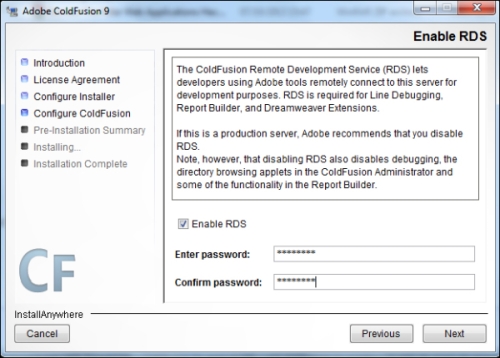
- Check the Enable RDS option as shown in the following screenshot:
- Set Adobe ColdFusion 9 to host as a self-contained application as the following screenshot shows:
- Go through with the final stages of the setup by logging on to the application through your browser. Make a note of the port that you're accessing it through; this will be the port that should be accessible remotely if the software is correctly set up.
- To test the installation, browse to the server. The default will be port 8500, so
http://127.0.0.1:8500should provide the installation directory, as the following screenshot shows: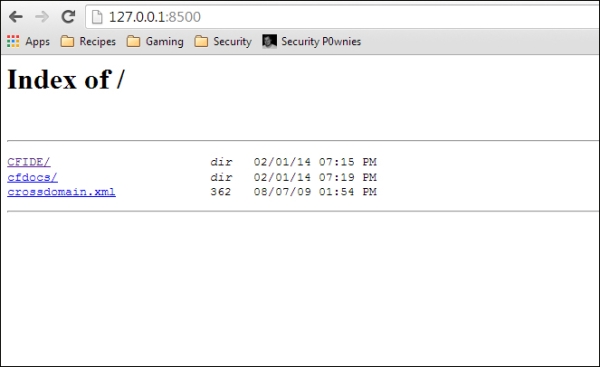
Variations
There are a few vulnerabilities that can work here. First, the RDS login method can be attacked through a Metasploit module to gain an administrative login. This can be used to get a remote shell. Alternatively, default credentials can be used as the vulnerability, and a directory traversal can be used to gain the key.
To place a .flag file for the directory traversal, create a .txt file, or a file in any other format based on what you want it to be, and place it in a directory. As the directory traversal can only call specific files and not print directories, you will have to provide the attackers with the path in brief.
First, work out the scenario you want. It can simply be: find John's PC and exploit the common web weakness to find his bank details. I hear he keeps them in C:/BankDetails.txt.
Then, name the computer such that it has something to do with John. John-PC works for me over JohnBoy or LittleJohn, which make it easy for the attacker to identify it. Create the BankDetails.txt file, and place the file in the correct folder.
Once everything is set up, you have to test it and prepare the brief for the attackers. To test, please see the exploitation guide further along in this chapter.
































































