Kali on Android (non-rooted phones)
With the support of ARM images, it is possible to directly download the Nethunter images from the Kali website; however, in this section we will try a different approach, running Kali on any Android device that is configured to a high enough standard.
We will utilize two applications from the trusted Google Play Store:
- UserLAnd: This is an open-source app that allows you to run several Linux operating systems on Android devices. This can be downloaded to the device through the Play Store by visiting https://play.google.com/store/apps/details?id=tech.ula&hl=en_GB&gl=US.
- ConnectBot: A powerful open-source SSH client, it can manage simultaneous SSH sessions, create secure tunnels, and copy/paste between other applications. This application can also be downloaded directly through the Play Store or by visiting https://play.google.com/store/apps/details?id=org.connectbot&hl=en_GB&gl=US.
Once you have downloaded UserLAnd, you should see the same as that shown in Figure 1.25; select Kali:
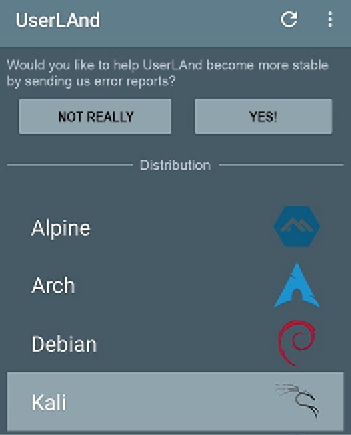
Figure 1.25: Selecting Kali Linux in the UserLAnd mobile application
The application should ask for your username, password, and VNC password for Kali to log in. Once the action is completed, there should be a pop-up asking you to select a connection bot, as shown in Figure 1.26:
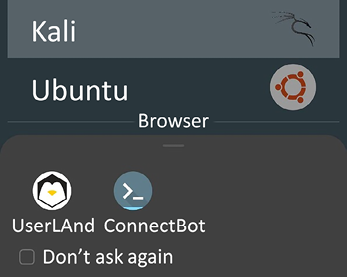
Figure 1.26: After the Kali Linux image is downloaded, you will be provided with the two options; select ConnectBot
We now have a lightweight version of Kali Linux (you may have to install the tools as and when required; as an example, you may install routersploit by running sudo apt-get update && apt install routersploit to gather information about the router that the mobile device is connected to) on our handheld Android device; part of the interface is shown in Figure 1.27:

Figure 1.27: Successful installation of Kali Linux on an Android device
We have now seen how Kali Linux is installed and run on an Android device without having to root the device. The version of Kali Linux on the device operates in its own sandbox; therefore, there will be no restrictions on us performing penetration testing from the device.
































































