Reviewing packet analysis
Packet analysis examines packets to understand the characteristics and structure of the traffic flow, either during a live capture or by using a previously captured file. The analyst can complete packet analysis by either studying one packet at a time or as a complete capture.
When monitoring the network for analysis, we capture traffic using specialized software such as Wireshark or tshark. Once the data is captured and we save the file, the software stores the data in a file that is commonly called a packet capture or PCAP file.
Packet analysis benefits many groups, including the following:
- Network administrators: Use packet analysis to gain information about current network conditions.
- Security analysts: Use packet analysis to determine whether there is anything unusual or suspicious about the traffic when carrying out a forensic investigation.
- Students: Use packet analysis as a learning tool to better understand the workings of different protocols.
- Hackers: Use packet analysis to sniff network traffic while conducting footprinting and reconnaissance in order to gain valuable information about the network.
We use packet analysis in many places, including on a LAN, on a host, or in the real world. Additionally, we use packet analysis when troubleshooting latency issues, testing Internet of Things (IoT) devices, and as a tool when baselining the network.
Today, packet analysis using Wireshark is a valuable skill. However, analyzing packets has been around in the networking world for many years. As early as the 1990s, various tools enabled analysts to carry out packet analysis on the network to troubleshoot errors and to monitor server behavior. In the next section, we'll examine some of the early tools used to monitor network activity.
Exploring early packet sniffers
Packet analysis has been around in some form for over 20 years, as a diagnostic tool, to observe data and other information traveling across the network. Packet analysis is also referred to as sniffing. The term refers to early packet sniffers, which sniffed or captured traffic as it traveled across the network. In the 1990s, Novell, a software company, developed the Novell LANalyzer, which had a graphical UI and dashboard to examine network traffic. Concurrently, Microsoft introduced its Network Monitor.
Over the last 20 years, there have been many other packet analyzers and tools to sniff traffic, including the following:

Table 1.1 – Packet analyzers and tools
Most packet analyzers work in a similar manner. They capture data and then decode the raw bits in the field values according to the appropriate Request for Comment (RFC) or other specifications. Once done, the data is presented in a meaningful fashion.
Packet analysis tools range in appearance and functionality, as follows:
- They provide simple text-based analysis, such as terminal-based Wireshark (
tshark). - They deliver a rich graphical UI with advanced artificial intelligence (AI)-based expert systems that guide the analyst through a more targeted evaluation.
In the next section, we'll take a look at the various devices that use packet analysis today.
Evaluating devices that use packet analysis
Packet analysis and traffic sniffing are used by many devices on the network, including routers, switches, and firewall appliances. As data flows across the network, the devices gather and interpret the packet's raw bits and examine the field values in each packet to decide on what action should be taken.
Devices examine network traffic in the following manner:
- A router captures the traffic and examines the IP header to determine where to send the traffic, as part of the routing process.
- An IDS examines the traffic and alerts the network administrator if there is any unusual or suspicious behavior.
- A firewall monitors all traffic and will drop any packets that are not in line with the Access Control List (ACL).
For example, when data passes through a firewall, the device examines the traffic and determines whether to allow or deny the packets according to the ACL.
Using an ACL
When using a firewall, an ACL governs the type of traffic that is allowed on the network. For example, an ACL has the following entries:
- Allow outbound SYN packets. The destination port is
80. - Allow inbound SYN-ACK packets. The source port is
80.
To decide whether to allow or deny a packet, the firewall must check each header as it passes through the device. It will determine variables such as IP addresses, Transmission Control Protocol (TCP) flags, and port numbers that are in use. If the packet does not meet the ACL entry, the firewall will drop the packet. As shown in the following diagram, an inbound SYN packet with a destination port of 80 is blocked because it does not match the rule:
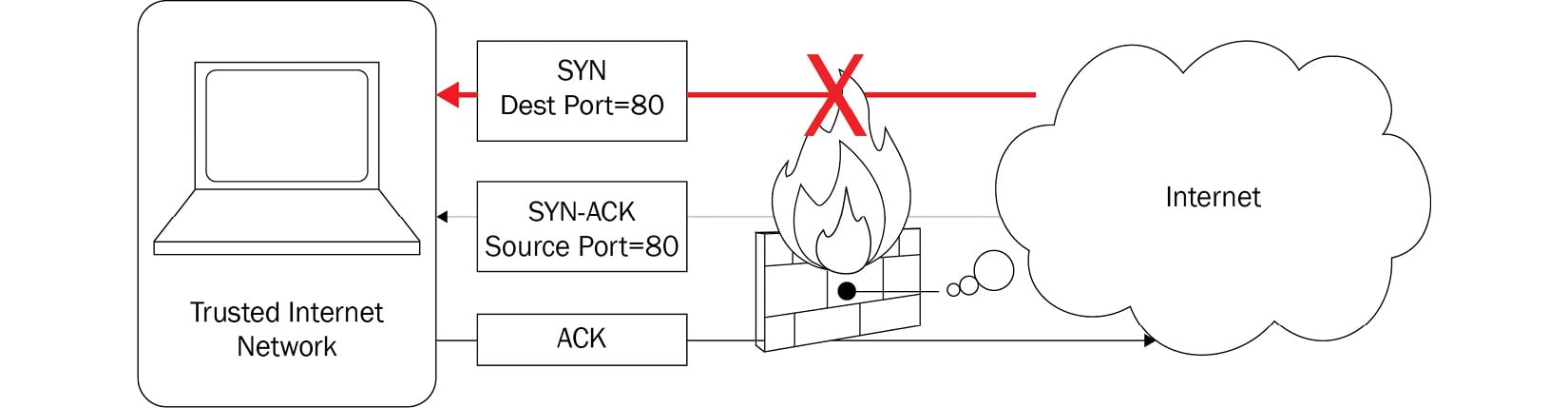
Figure 1.1 – A firewall with an ACL
It's important to note that a packet sniffer examines traffic but doesn't modify the contents in any way. It simply gathers the traffic for analysis as it travels across the network.
As you can see, packet sniffing and analysis have been influential for many years as elements of managing networks. However, the first step of analysis is to capture traffic, which we will explore next.
Capturing network traffic
On today's networks, a Network Interface Card (NIC) will only monitor traffic that is addressed to that host. However, we can put the card into a state called promiscuous mode, which will allow the adapter to gather all the traffic that is on the network. Therefore, to capture and monitor all network traffic, the NIC must be in promiscuous mode.
On a Windows machine, you can check to see whether the interface card is in promiscuous mode by running the following command in PowerShell:
Windows PowerShell Copyright (C) 2014 Microsoft Corporation. All rights reserved. PS C:\Users\Admin> Get-NetAdapter | Format-List -Property PromiscuousMode PromiscuousMode : False
We use packet analysis to understand the characteristics of the traffic flow. Although you can conduct packet analysis during a live capture, it's common to capture traffic and save it for further analysis. Common steps to capture packets for analysis include the following:
- Install Wireshark and the appropriate packet capture engine.
- Launch Wireshark and select the capture options.
- Start the capture and run until you capture 2,000–3,000 packets.
- Stop the capture and save the trace file in the appropriate format.
- Analyze the capture by studying one packet at a time, or as a complete capture.
In some cases, you might need to send a packet capture to the corporate or security analyst for further analysis.
Wireshark allows us to capture, display, and filter data live from a single or multiple network interface(s). In addition, you can examine pre-captured packets, search with granular details, and follow the data stream. As a result, packet analysis is advantageous as it helps you to understand the nature of the network. The following section outlines the many different individuals who can benefit from using Wireshark for packet analysis.























































