Using the time picker
Now that we've looked through all of the widgets, let's use them to modify our search. First we will change our time. The default setting of All time is fine when there are few events, but when Splunk has been gathering events for weeks or months, this is less than optimal. Let's change our search time to one hour.
The search will run again, and now we only see results for the last hour. Let's try a custom time. Date is the first option.
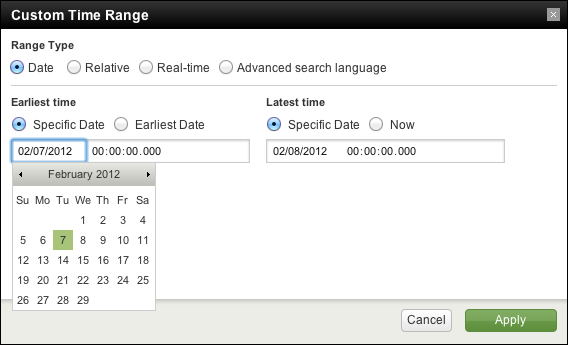
If you know specifically when an event happened, you can drill down to whatever time range you want here. We will examine the other options in Chapter 2, Understanding Search.
Note
The time zone used in Custom Time Range is the time zone selected in the user's preferences, which is by default the time zone of the Splunk server.
























































