Modern access management
The Covid-19 pandemic has heightened our sense of uncertainty as humans over physical and mental health, economy, family, society, and work. Most of us have experienced long-lasting effects on our lives that we never envisioned. Some of these profound effects may drag our lives backward or forward by years. A paradigm shift hastened by the pandemic is the accelerated digital transformation of society. The lockdown rules and increased demand for secure remote work has pushed some "offline" businesses and industries into the "online" realm sooner than we thought. My nine-year-old daughter is having her piano lessons via Zoom meetings now. I never thought it was practical to learn an instrument "online" but I was proven wrong. At the beginning of the pandemic, the financial sector wasn't ready to embrace the working from home culture. But a recent survey carried out by Deloitte confirms almost three quarters (70%) of employees working in financial services rate their working from home experience as positive. (Source: https://bit.ly/3CSjC08) Twilio is a leading cloud communications and customer engagement platform. They recently surveyed over 2,500 enterprise decision makers in the United States, the United Kingdom, Germany, Australia, France, Spain, Italy, Japan, and Singapore to evaluate their views on digital transformation as a result of Covid-19. According to the survey results, "97% of enterprise decision makers believe the pandemic sped up their company's digital transformation." (Source: https://bit.ly/2ZSnTlK.) McKinsey & Company is an American worldwide management consulting firm and they recently did a survey using 900 C-level executives and senior managers representing the full range of regions, industries, company sizes, and functional specialties. According to the study, respondents confirmed their companies acted 20 to 25 times faster than expected in implementing digital transformation strategies. When it comes to remote working, companies moved 40 times faster.
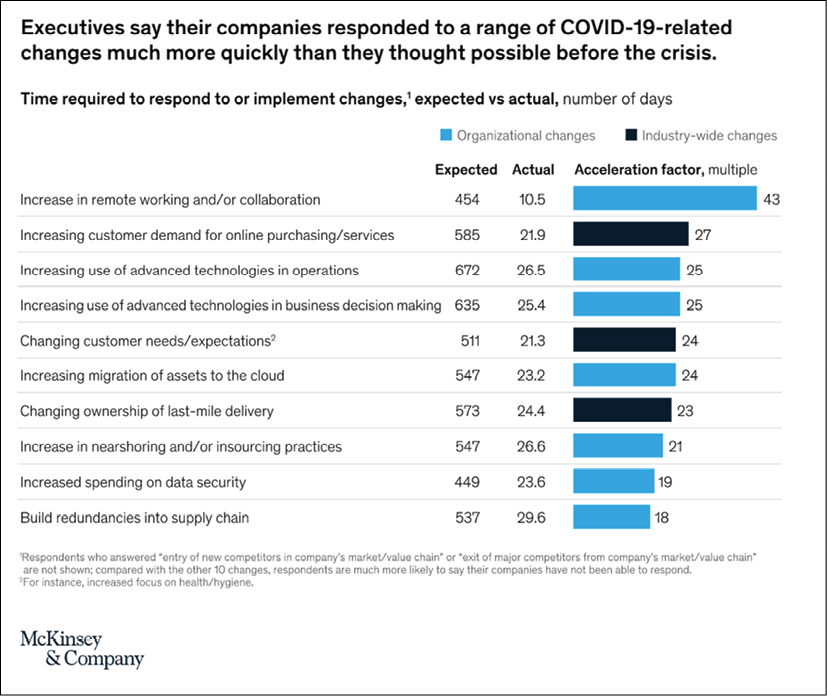
Figure 1.1: Speed of responses to pandemic challenges
Source: https://mck.co/2Ykj9Fd
With the rise of digital transformation, working from home has become the new normal. Businesses have had to implement applications, services, and collaboration tools that allow remote workers to carry out their day-to-day tasks seamlessly. On this journey, the hurdle wasn't the investment or the technology.
It was the "time." This was the same for many businesses when adopting this ubiquitous nature of operations. When "time" starts to cost us money or when "time" starts to affect sales, the manufacturing process, supplies, or workforce productivity, we do not have time to evaluate all the pros and cons. We do not have time to do all the ground work. We will have to take risks. We will have to bend the rules. When we rush things, as humans, we tend to make mistakes. Some of these mistakes opened up opportunities for cyber criminals throughout 2020:
- According to iomart, large-scale data breaches increased 273% in the first quarter of 2020. (Source: https://bit.ly/3mNckFB)
- Data from the UK's Information Commissioner's Office (ICO) confirms 90% of cyber data breaches were caused by user errors. (Source: https://bit.ly/3whpgGV)
- According to RiskBased Security's 2020 Q3 report (Source: https://bit.ly/3mMxjbu), healthcare (11.5%) and IT (10.3%) are the two industries that reported the most data breaches. Also, we know these industries have been the most active industries during the pandemic.
- The report also says, when we consider all of the breaches in 2020, that 29% of those exposed passwords, 36% exposed email addresses, and 45% exposed names.
If we summarize the above findings, we can see there was a massive increase in data breaches in 2020 and the majority of those breaches were due to human error. The healthcare and IT industries have been the top targets financially motivating cyber criminals in 2020. The above data also confirms cyber criminals are mainly after identities.
Identity is the new perimeter. The perimeter defense model is no longer valid against modern identity threats. Identity and access management is the cornerstone of digital transformation. A study done by Ping Identity says 90% of IT decision makers believe identity and access management is the key enabler of digital transformation (Source: https://bit.ly/3BNw0gS). Identity and access management solutions depend on directory services such as Windows Active Directory to store/retrieve data relating to user identities. Windows Active Directory was first released on February 17, 2000, and for 21 years it has been helping organizations to manage identities. But now we have a new set of challenges.
According to FireEye's Cyber Security Predictions 2021 report (https://bit.ly/3nZBpfQ), about 95% of companies have some type of cloud presence.
So the questions are:
- How can we allow users to use the same Active Directory user accounts to access cloud resources?
- How can we enable a single sign-on (SSO) experience for cloud-based applications?
- How can we protect identities when they start to appear in cloud and unsecured networks?
- How can we maintain compliance when we start using cloud resources?
- How can we detect/handle a potential breach?
To address the above questions, we need a distributed, highly available identity and access management solution such as Azure Active Directory. It doesn't mean Azure Active Directory is a replacement for Windows Active Directory. These are two different products with many different characteristics. But these two solutions can work together to address access and security challenges in both worlds (On-prem and the cloud). In this edition, you will find many topics and a lot of content related to hybrid identity. Also, throughout the book, content will be positioned to accentuate the importance of identity protection.
What is an Identity?
Elephants are truly fascinating creatures. Female elephants stay in their herd for life. When a baby elephant is born, young female elephants in the herd will help the mother to take care of the baby. A baby elephant usually weighs about 250 pounds and is three feet tall. In the beginning, a baby elephant can't see clearly. But it can identify its mother among the other young female elephants by touch, smell, and sound. Social insects such as ants recognize various castes in their colony based on "ant body odor." The same method is also used to recognize ants from other colonies.
When it comes to humans, we use many different ways to uniquely identify a person. In day-to-day life, we recognize people based on their name, face, voice, smell, body language, uniforms, and so on. The uniqueness of individuals describes an "identity." However, if we need to prove our identity, we need to use formal methods of identification such as a passport, driving license, and residence card. These formal methods are well recognized by many authorities. So far, we have talked about physical identity. But how can we bring this to the digital world? To do that, we need our digital identity to represent our physical identity.
As an example, when I registered with my GP for the first time, they checked a form of identification and verified my identity. Then they issued me with a unique NHS number; this unique number is the way their computer system will recognize me. When I signed up for my broadband connection, the service provider asked me to set up a unique password. This password will be used to prove my identity when I call them for support next time. Different systems, applications, and services uses different methods to verify someone's digital identity. These systems use databases and directories to store the data related to digital identities.
It is also important to remember a digital identity does not always represent a human. It can represent other entities such as devices, applications, services, groups, and organizations. Digital identities are also becoming more and more dynamic. As an example, your Facebook profile represents a digital identity. It keeps updating based on pictures you upload, posts you share, and friends you make. It is a living identity. A digital identity can get frequently updated based on attributes and access privileges. Nowadays, we can see different systems allow users to use one form of digital identity to get access. As an example, a Microsoft account can be used to access on-prem applications as well as SaaS applications. These federated digital identities provide a better consumer experience. The Active Directory service is capable of managing digital identities as well as federated digital identities.
Before we go and look into Active Directory fundamentals, I think it is better to share some of the identity and access management trends that lie ahead of us in 2021 and see how Active Directory will fit in to the picture.
































































