We are going to implement oauth2_proxy from bitly (https://github.com/bitly/oauth2_proxy). We will be following the steps indicated in the documentation for Azure AD (https://docs.microsoft.com/en-us/azure/active-directory/).
First, register an app with Azure AD as shown in the following screenshot:

Next, create a client ID secret by performing the following steps:
- Select Certificates & secrets and go to New client secret:
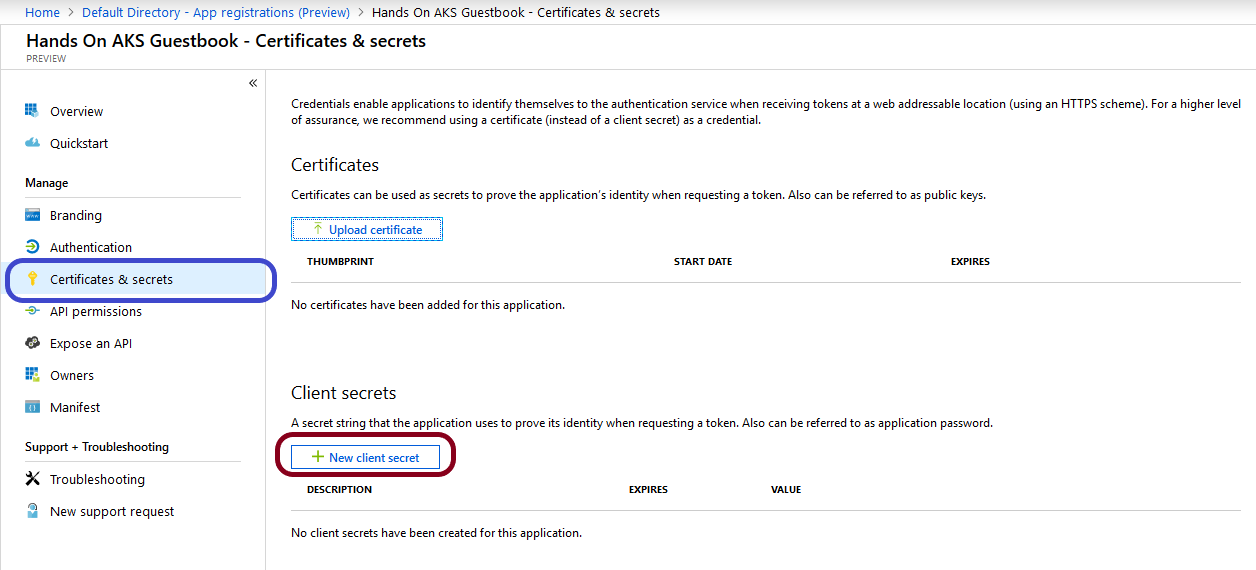
- Add the secret:

- Click on the Copy icon and save the secret in a safe place:
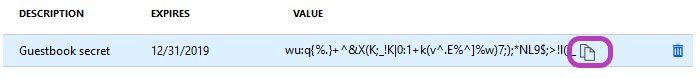
- Save the client and the tenant ID:

After creating the client ID secret, we will now launch oauth2_proxy with the following YAML file:
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: oauth2-proxy
namespace: kube-system
spec:
replicas: 1
selector:
matchLabels:
app: oauth2-proxy
template:
metadata:
labels...











































































