Chapter 2. Networking for Packet Analysts
Packet analysis is all about analyzing how applications transfer useful data from point A to point B over networks. So, an understanding of how networks function is essential.
In this chapter, we will cover the following topics:
- Why the seven-layer OSI model matters
- IP networks and subnets
- Switching and routing packets
- Ethernet frames and switches
- IP addresses and routers
- WAN links
- Wireless networking
The seven-layer OSI model will be mapped to the most common networking terms, and we'll review frames, switching, IP addressing, routing, and a few other networking topics of interest. The goal is to develop a mental model of networking that lends itself well to packet-level analysis.
The OSI model – why it matters
The Open Systems Interconnections (OSI) reference model is an industry recognized standard developed by the International Organization for Standardization (ISO) to divide networking functions into seven logical layers to support and encourage (relatively) independent development while providing (relatively) seamless interconnectivity between each layer from different hardware/software environments, platforms, and vendors. There's also a somewhat simpler four-layer Defense Advanced Research Projects Agency (DARPA) model that maps to the OSI model, but the OSI version is the most commonly referred to. I'll reference both models when discussing the various layers.
The following diagram compares the OSI and DARPA reference models:

Unless you're in the business of writing protocols, there's no need to study any of the seven layers in great depth, but it is helpful to understand them conceptually because these layers are referred to by the industry and your IT peers.
More importantly, it's essential that you know where and how these layers and their associated protocols are presented in Wireshark's Packet Details pane. We'll cover the layers from this aspect to help you remember them and get the most use from the discussion.
Understanding network protocols
Network protocols, like the OSI layers, are a set of industry standard rules and designs used to exchange messages and data between computers and applications. In any discussion about OSI layers, you are directly or indirectly referring to the protocols associated with a given layer—the most commonly known protocols are IP, UDP, TCP, HTTP, and so on—and the significant functions they perform.
For example, you'll often hear the terms network layer and IP layer used interchangeably, and it is assumed and understood that you are talking about the layer and the associated protocol that contains and uses IP addresses to route packets from point A to point B across the network. The discussions that follow will tie the OSI and DARPA layers to their associated protocols.
The seven OSI layers
As we cover the OSI layers starting from layer 1 and working up to layer 7, I'll outline how each layer's associated protocol(s) are displayed in Wireshark and/or used in networking hardware. The mental model you develop from this approach should be the most accurate and useful for packet analysis.
Layer 1 – the physical layer
The physical layer encompasses the electrical characteristics and mechanical standards to get data bits transmitted from a computer's Network Interface Card (NIC) to a switch port or between switch and router ports. The most common standards, terms, and devices you'll encounter at this layer include the following:
- Ethernet: This is a family of networking technologies for local area networks (LANs).
- RJ-45: These are 8-pin modular connectors found on both ends of a copper Ethernet cable that are plugged into the NIC on a computer and a wall jack or switch port
- Cat 5 (Cat 5e or Cat 6) cables: These are Ethernet cables that use twisted-pair copper wires. "Cat" stands for the category of cable and reflects its quality and data speed capabilities.
- 100Base-T, 1000Base-T, and 1000Base-LX: These represent a particular Ethernet standard. 100Base-T is 100 Mbps over twisted-pair cable using RJ-45 connectors, 1000Base-LX is 1000 Mbps over fiber, and so on.
- Single-mode and multimode fiber optic cables: These use pulses of light from solid-state LEDs or lasers to transmit data bits.
The Ethernet standards used to connect NICs to switches are also used to connect switches together and to connect switches to routers or other network devices, although the cables and connectors used may vary depending on cable type and speed.
There are other layer 1 standards in common use, including 802.11 Wireless, Frame Relay, and ATM; the last two are used in long distance wide area networks (WANs).
Layer 2 – the data-link layer
The data-link layer organizes raw bits from the physical layer (typically Ethernet) into frames, which is the first manifestation of what is generally called a packet that you'll see in Wireshark. This layer is a dividing line between physical networking, electrical/mechanical standards, and the logical structures (protocols) used to format and transmit, receive, and decode packets of data in the higher layers.
In the DARPA reference model, the physical and data-link OSI layers are combined and called the network interface layer. The significant features and functions of this layer (for Ethernet II frames) include:
- Media Access Control (MAC) addresses: These are the network addresses used in LANs. They are 6-byte network hardware addresses burned into memory chips on NICs, switches, routers, or other network device ports/interfaces:
- The first three bytes of a MAC address are assigned to and can be associated with a specific manufacturer. Wireshark has a list of these and can display MAC addresses as a combination of the manufacturer code and the last three bytes. The manufacturer creates a unique last-three-bytes address for every interface so that each MAC address is unique across the globe. (Although, an NIC might be programmed to use another arbitrary MAC address, which is done for MAC spoofing for malicious attacks. But this is a very bad idea as another card may be using the same address and can cause a loss of data and some very confusing packet switching problems.)
- Ethernet frames include a destination and source MAC address. MAC addresses are used to switch (not route—we'll make the distinction shortly) frames between computers on the same LAN or between computers and a router or other device port on a LAN.
- Type (or EtherType) field: This indicates the next higher protocol layer (typically IP (0800) or ARP (0806)). Wireshark uses this to determine the next protocol dissector to apply in packet decodes.
- Payload: This is the packet or datagram carried by the Ethernet frame.
- The frame check sequence: This is a 4-byte Cyclic Redundancy Check (CRC) error-detection code calculated from all the bits in a frame and added to the end of the frame. This is used to detect frames that have been corrupted usually because of faulty cables, noise induced on the wires in a cable from outside electrical signals, and so on. When a frame is received, this code is recalculated based on the bits received and compared to the FCS field. The bad frames are then discarded.
The following diagram illustrates the layout of the fields in an Ethernet frame:

A key point here—and this is important to understand—is that Ethernet frames and their MAC addresses are only able to transmit frames between devices on the local area network (LAN and IP subnet) they belong to.
Routers form the boundary between LANs by virtue of their IP subnet (subnetwork) addressing. All the devices belonging to the same IP subnet are part of the same LAN, and getting packets to or from a different subnet requires a router.
Once a frame enters a router port to get routed to a different/distant network, the Ethernet frame with its MAC addresses and FCS is stripped off and discarded. The payload inside the frame is routed to the port and it will leave on its way to the next device, and another frame with a different MAC address and recalculated FCS is created to encase the packet. This frame is then transmitted to the next destination.
The network devices that work at this layer—usually switches—are commonly referred to as layer 2 devices or layer 2 switches.
Finally, you should be aware that layer 2 switches can support several networking enhancements such as Virtual LAN (VLAN) and Class of Service (CoS) tagging, which is accomplished by adding a 4-byte 802.1Q field between the MAC addresses and EtherType field. You might see these frames between switches (but not on user ports).
VLAN is a layer 2 solution that allows administrative partitioning of various ports on a switch into separate broadcast domains. Devices located on different VLANs are effectively isolated from each other as if they were on separate physical networks. VLANs can be dispersed across multiple switches without running separate cables for each VLAN if the switches support VLAN tagging. Communication between devices on separate VLANs generally requires using a router.
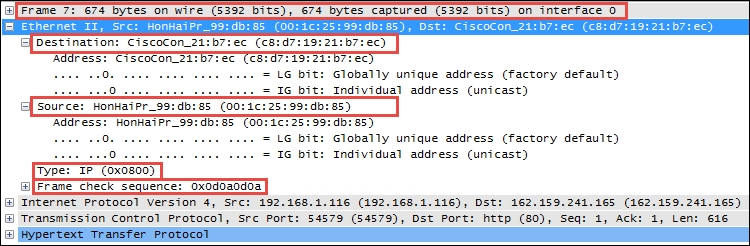
In the following Wireshark packet details screenshot, the Ethernet II frame Destination and Source MAC addresses, Type (indicating that the next layer protocol is IP), and Frame check sequence are circled, as is the Frame summary.
Note
Wireshark displays a summary of each frame that includes frame sizes, captured timestamps and interframe times, and other useful information. This is metadata calculated by Wireshark to aid in analysis and not a part of the captured frame.
The following screenshot highlights the significant fields of an Ethernet frame:
Note
Any additional analysis provided by Wireshark in any area of the Packet Details pane that is calculated or otherwise not part of actual packet contents will be encased in brackets.
Layer 3 – the network layer
The network layer (called the Internet layer in the DARPA model) primarily handles the routing of packets across and to other networks along the path from source computers to destination hosts based on the destination IP address. The two most common protocols seen at this layer are Internet Protocol and Address Resolution Protocol.
Internet Protocol
The most common protocol in use at this layer is Internet Protocol Version 4 (IPv4), which includes several essential fields to accomplish the task of routing packets across networks:
- Differentiated Services (DiffServ): This field supports an enhancement to the IP that is generally called Quality of Service (QoS) and allows classification of certain types of traffic (voice, video, and so on) so that these packets can receive priority handling in cases of network congestion.
- Total length: This is the total length of the packet (minus the Ethernet MAC header).
- Identification (IP ID): This an incrementing number used to support fragmentation.
- Flags: These are used to support fragmenting (dividing a packet into two or more smaller ones) in case the large packets have to be divided into several smaller ones to traverse a packet-size-limited link. These flags along with the IP ID field values allow proper reassembly of the fragmented packets into the original.
- Fragment offset: If the Flag field is 1 (more fragments), the value in this field indicates the offset from the start of the original payload in bytes that this fragment packet contains.
- Time to Live (TTL): This is a "hop" or time counter that is decremented every time a packet passes through a router. If the TTL reaches zero, the packet is discarded. The primary purpose is to keep packets from living forever and crashing the network in the case of an inadvertent path loop.
- Protocol: This identifies the protocol in the IP packet's payload. Wireshark uses this to determine the next protocol dissector to apply to packet decodes.
- Source and destination IP addresses: These are the IP addresses of the sending machine and the ultimate destination machine. IP addresses are 4 bytes long and are represented as four octets (numbered 0 through 255 decimal) separated by periods.
In the following screenshot, the significant IPv4 fields are circled. These are the fields you'll want to inspect and be comfortable with when doing packet analysis at this layer.

Address Resolution Protocol
Another protocol you'll see at the network layer is Address Resolution Protocol (ARP), which is used by a device to obtain the MAC address of another device when it only knows that device's IP address.
In the following Wireshark packet details screenshot, note that the Ethernet frame destination MAC address is Broadcast (ff:ff:ff:ff:ff:ff), Type is ARP (0x0806), and the station has provided its own MAC and IP address in the ARP protocol Sender fields (which other stations listen to and use to build a table of MAC and IP addresses). It provides the IP address of the target device and puts all zeros in the Target MAC Address field. The target device should return a similar ARP packet addressed to the requestor with its MAC address in the Sender field.
A station will send an ARP request only in the following situations:
- The station that requires a MAC address for a target device hasn't heard a previous broadcast of that station's MAC address, or its ARP table has timed out (ARP entries are only kept for a period).
- The station that requires a MAC address for a target device has calculated (from the target's IP address and its own subnet mask) that the target device should be on the same LAN. Otherwise, the station assumes the target device is on a different network and sends its first session initiation packet to the default gateway (router) MAC address based on the entry in the sending station's default gateway configuration setting. The default gateway will forward the packet to the appropriate egress port to route it to the destination.
- The station that needs to send a packet to a distant network doesn't know the MAC address of its default gateway (for example, just after a power-up).
The following screenshot highlights the significant fields of an ARP packet:

Other protocols utilized at this layer include Internet Control Message Protocol (ICMP), which is used to send network error messages between devices, and Internet Group Management Protocol (IGMP), which is used by hosts and adjacent routers to establish multicast (one-to-many) group memberships for network applications such as streaming video and gaming.
Layer 4 – the transport layer
The transport layer, as it's called in both the OSI and DARPA models, is responsible for transporting packets of data in unique sessions between applications or a user and an application by means of port numbers. The combination of a device or user's IP address and that device or user's assigned port number (referred to as a socket) will be different from another devices or users' IP address and port numbers (on the client side).
If the source host for a packet is a server, the source port is likely to be a well-known number for standard applications and services, such as port 80 for HTTP.
The transport layer typically uses one of two protocols, User Datagram Protocol or Transmission Control Protocol, with the latter being the more prevalent for most applications.
User Datagram Protocol
The User Datagram Protocol (UDP) is a fairly simple protocol. It is considered an unreliable transport as there's no guarantee of packet delivery or ordering, but it has lower overhead and is used by time-sensitive applications such as voice and video traffic, as well as by network services applications such as DNS.
The UDP header is only 8 bytes long and consists of the following:
- Source and Destination port number:These are 2 bytes each.
- Length: This is the length of the UDP header plus the payload. This is a 2-byte field.
- Checksum: This is the 2-byte field used to check errors of the UDP header and data. If no checksum was generated by the transmitter, this will be all zeros.
The following screenshot shows the fields contained in a UDP header:

Transmission Control Protocol
Unlike UDP, the Transmission Control Protocol (TCP) provides reliable delivery of data by detecting lost, duplicated, or out-of-order packets, requesting retransmission of lost data, or rearranging packets in the right order before delivering them to the application. TCP can also accept a large chunk of data from an application and handle getting the data transported to the other end reliably using multiple packets and reassembling them at the other end (as can UDP, but not reliably; the application has to determine and recover from lost packets).
The TCP header contents and length can vary depending on the options that may be in use, but in its simplest implementation, it consists of:
- Source and Destination ports (2 bytes each): These are well-known registered ports that are used (on servers) to access standard application services such as HTTP, FTP, SMTP, databases, and so on. Port numbers assigned to client/user sessions are usually in a higher number range and assigned sequentially.
- Sequence number (4 bytes): This is a number that represents the first octet in any given segment. Sequence numbers are initialized at the beginning of new sessions as a random number, and then incremented as data bytes and sent.
- Acknowledgment number (4 bytes): When the ACK flag bit is set, this field contains the next sequence number expected from the sender, which in turn acknowledges receipt of all the bytes received up to that point.
Note
The use of sequence and acknowledgment numbers are how the TCP ensures reliable delivery of data by tracking the number and order of received bytes.
Sequence and acknowledgment numbers are large and difficult for humans to follow; Wireshark can convert and display these as relative values that start with 0 at the beginning of a session to make it easier to inspect them and relate the values to the number of bytes transmitted and received.
- Flags (9 bits): These bits are used to control connection setups, terminations, and flow control mechanisms.
- Window size (2 bytes): This indicates the current size of the buffer on this host used to store received data until it can be handed off to the receiving application. This information lets the sending host adjust data flow rates in case of network or host congestion.
The following screenshot highlights the significant fields of a TCP header:

Layer 5 – the session layer
The session layer handles setting up, controlling, and ending sessions within an application between two computers. This is not necessarily the same thing as, for example, a TCP connection, although the two will be related. The application sessions can span and outlive multiple network connections. An example of a networking protocol that operates at this layer is Network Basic Input/Output System (NetBIOS).
Layer 6 – the presentation layer
The presentation layer converts incoming and outgoing data from one format to another and handles encryption/decryption and/or compression if any of these are required. The presentation layer is also responsible for the delivery and formatting of information to the application layer for further processing or display. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCII-coded file.
Layer 7 – the application layer
The application layer, which may (or may not) perform separate functions from the application itself, handles message formatting, human to machine interfaces, and so on. This layer represents the services that directly support applications such as software for file transfers, database access, e-mail, and so on.
In many widely used applications, no distinction is made between the presentation and application layers. For example, HyperText Transfer Protocol (HTTP), which is generally regarded as an application-layer protocol, has presentation-layer aspects such as the ability to identify character encoding for proper conversion, which is then done in the application layer.
In the DARPA model, the OSI layers 5-7 are combined into an application layer. From a packet analysis standpoint, the particular manifestations and visibility (in Wireshark) of the functions in the top layer(s) will vary depending on the applications and specific protocols employed to support them.
The following diagram summarizes the OSI and DARPA layers and how various networking protocols and services align with these layers and each other:

Encapsulation
You may have observed by now that packets encapsulate various protocols into successive layers, just like peeling an onion. An Ethernet frame contains a datagram payload; this datagram is a packet with an IP header and payload. The IP packet payload consists of a TCP header and data segment, which in turn may contain an HTTP header and payload. This encapsulation is easier to visualize when working within Wireshark's Packet Details pane.
IP networks and subnets
Before moving on, a short review of typical IP subnetting terms and typical applications should help clarify the terms used in this book and will act as a refresher for those already versed in IP addressing.
A /24 designator placed after a network IP address in diagrams or device configurations is a Classless Inter-Domain Routing (CIDR) designator that indicates the following:
- The first 24 out of the 32 bits in the 4-byte IP address represents the network portion of any IP address on this network. This network is designated as
10.1.1.0(the next/24network would be10.1.2.0, then10.1.3.0, and so on). - The last 8 bits of the 32-bit address can be used to give workstations, hosts, and other devices an IP address, with the following exceptions:
- The first host address on this network is reserved as a network designator to build routing tables:
10.1.1.0(typically called the loopback address) - The last host address on this network is reserved as an IP broadcast address:
10.1.1.255
The 8 bits binary is equal to 256 decimal, minus the preceding two exceptions. This leaves 254 usable IP addresses for devices, starting with
10.1.1.1,10.1.1.2, and so on up to10.1.1.254. - The first host address on this network is reserved as a network designator to build routing tables:
- Another way of expressing subnet masks is in a dotted decimal format,
255.255.255.0, which again indicates that the first 24 bits of an IP address is the network and the remaining 8 bits are for hosts. - There are Class A, Class B, and Class C address ranges, as well as a subset of IP ranges reserved as private addresses to use within organizations.
The following table shows the IP address ranges in the three major classes:
Class of IP address
Starting IP address
Ending IP address
A
1.0.0.0126.255.255.255B
128.0.0.0191.255.255.255C
192.0.0.0223.255.255.255The following table shows the private IP address ranges:
Class of private IP addresses
Starting IP address
Ending IP address
A
10.0.0.010.255.255.255B
172.16.0.0172.32.255.255C
192.168.0.0192.168.255.255 - Subnet masks can be configured to allow more or fewer hosts per subnet with a corresponding tradeoff in having fewer or greater network addresses with which to build multiple networks within larger organizations.
A deeper review of IP addressing and subnetting is beyond the scope of this book. If you're not familiar with these concepts, some additional study would be advisable as a solid understanding of IP subnetting is essential for most analysis activities.
Switching and routing packets
So far, we've covered the topics required to discuss how packets of data get routed from computer A to host B across LANs and/or WANs over distances that may range from across a room to across the globe. The important concepts to remember are that Ethernet frames work with switches and IP packets work with routers to accomplish this feat, which we'll cover in the next section.
Ethernet frames and switches
To reiterate what was outlined in the layer 2 (the data-link layer) discussion, Ethernet frames are switched from the entry port to the appropriate destination port based on the destination MAC address. Network switches build tables of which MAC addresses belong to each port, compare a frame's destination MAC address to these tables, and switch the frame to the appropriate egress port if the destination is on the same switch or out a trunk port to another switch or router otherwise.
Note that the first time a switch sees a destination MAC address it doesn't recognize, it sends the packet (which will usually be an ARP packet) out all the ports until a device answers and it can add the new MAC address to its content addressable memory (CAM) table that maps MAC addresses to specific ports.
Frames carrying packets destined for remote networks are sent to the default gateway port MAC address. If you look at a list of MAC addresses in the Ethernet tab of a Conversations table in Wireshark and see an address with a drastically higher volume of traffic than the other stations, this is likely a default gateway (router) port MAC address. This port is the pathway into/out of this LAN from/to other networks.
On any given LAN, you'll see workstations, servers, and routers generating ARP and Domain Name Service (DNS) requests:
- ARP: This is used to resolve IP addresses to MAC addresses
- DNS: This is used to resolve hostnames to IP addresses
In the following diagram, there are two user workstations and a server that are connected together in a LAN residing on the 10.1.1.0/24 IP network. A router is attached to this network, which has a WAN link to another location.

The following two scenarios leverage this drawing to show how MAC addresses are utilized to switch Ethernet frames around local area networks:
- The workstation with MAC address B wants to use an application on the server Venus, which is unknown to all the network devices as it was just powered up. The workstation knows the IP address of Venus as the IP address was preconfigured in the client application, but it doesn't know the server's MAC address.
The workstation broadcasts an ARP packet with its own MAC and IP address as the sender, the IP address of the Venus server, and all the zeros for the MAC address in the Target fields. Venus responds to the workstation with an ARP response that includes its MAC address of C in the sender MAC address.
The workstation then sends a session initiation packet to the server using the server's MAC address as the destination MAC in the Ethernet frame.
These Ethernet frames traversed switch 3, which learned both devices' MAC addresses from observing the ARP conversations. The rest of the switches in the LAN network learned workstation C's MAC address when it broadcasted its ARP packet (because switch 3 sent this ARP packet out all ports), but not the server's MAC as the server responded directly to C.
- The workstation with MAC address A now wants to use an application on the server Venus. It doesn't know the server's MAC address either, so it sends an ARP request as well, which switch 2 broadcasts out all its ports, as does switch 1 and switch 3 as the switches only look at MAC addresses and the destination MAC address of any ARP request is ff:ff:ff:ff:ff:ff, so each switch is obliged to send the broadcast frame out all ports.
However, when the server Venus responds to A's ARP packet, using A's MAC address, each switch in the path has learned which ports it saw A's MAC address come in on. So, each switch only sends Venus' response out the appropriate port back to workstation A. The same is true for learned non-broadcast frames. If a switch doesn't recognize a destination MAC address of a nonbroadcast frame, these are sent out all ports the first time as well.
As switch CAM tables get populated with MAC addresses and their associated ports, the number of frames that must be sent to every device in the LAN as well as the workload on all these devices is reduced significantly.
IP addresses and routers
When packets need to leave the LAN to get to a remote IP network, routers are required to route the packets based on their destination IP addresses. The following scenario (still referring to the preceding screenshot) illustrates some of the details involved in one possible situation.
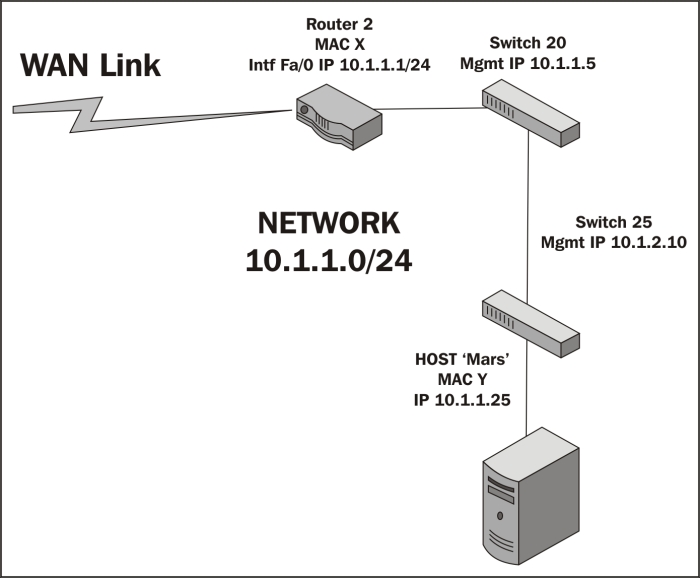
Workstation A now wants to use an application on the server Mars, which resides on a different network than in the previous scenarios. And in this case, workstation A doesn't know the IP address of the server; it only needs its name. Workstation A will send a DNS request packet to the DNS server IP address configured in its network settings (the DNS server isn't shown here) with the hostname Mars; the DNS server will return the IP address of Mars 10.1.2.25. Workstation A calculates that this host isn't on its own network from a comparison of its IP address and subnet mask with Mars' IP address, so it sends the session initiation packet to router 1, which was configured as its default gateway in its network settings. We'll assume that Workstation A already knows the MAC address of router 1's port from a previous ARP exchange to find router 1's MAC address from the given IP address.
When the router receives A's frame, which was sent to the router port's MAC address, it inspects the destination IP address inside the IP header and looks up the appropriate port to forward the packet to. This routing process is supported by routing table entries the router builds from route information broadcasted by other routers; each router tells all the others what networks it knows a route to.
In this case, the Ethernet frame surrounding A's packet is stripped off and the remaining payload (packet) is sent across the WAN link to router 2, which also inspects the IP header destination IP address and looks up the correct port to forward the packet to. Router 2 wraps the packet in a new Ethernet frame with its own MAC address X as the source and the Mars server's Y address as the destination MAC (assuming the router already has the server in its MAC table), and transmits the packet out onto the LAN to get switched to the Mars server, as shown in the following diagram:
Ethernet frames and switches
To reiterate what was outlined in the layer 2 (the data-link layer) discussion, Ethernet frames are switched from the entry port to the appropriate destination port based on the destination MAC address. Network switches build tables of which MAC addresses belong to each port, compare a frame's destination MAC address to these tables, and switch the frame to the appropriate egress port if the destination is on the same switch or out a trunk port to another switch or router otherwise.
Note that the first time a switch sees a destination MAC address it doesn't recognize, it sends the packet (which will usually be an ARP packet) out all the ports until a device answers and it can add the new MAC address to its content addressable memory (CAM) table that maps MAC addresses to specific ports.
Frames carrying packets destined for remote networks are sent to the default gateway port MAC address. If you look at a list of MAC addresses in the Ethernet tab of a Conversations table in Wireshark and see an address with a drastically higher volume of traffic than the other stations, this is likely a default gateway (router) port MAC address. This port is the pathway into/out of this LAN from/to other networks.
On any given LAN, you'll see workstations, servers, and routers generating ARP and Domain Name Service (DNS) requests:
- ARP: This is used to resolve IP addresses to MAC addresses
- DNS: This is used to resolve hostnames to IP addresses
In the following diagram, there are two user workstations and a server that are connected together in a LAN residing on the 10.1.1.0/24 IP network. A router is attached to this network, which has a WAN link to another location.

The following two scenarios leverage this drawing to show how MAC addresses are utilized to switch Ethernet frames around local area networks:
- The workstation with MAC address B wants to use an application on the server Venus, which is unknown to all the network devices as it was just powered up. The workstation knows the IP address of Venus as the IP address was preconfigured in the client application, but it doesn't know the server's MAC address.
The workstation broadcasts an ARP packet with its own MAC and IP address as the sender, the IP address of the Venus server, and all the zeros for the MAC address in the Target fields. Venus responds to the workstation with an ARP response that includes its MAC address of C in the sender MAC address.
The workstation then sends a session initiation packet to the server using the server's MAC address as the destination MAC in the Ethernet frame.
These Ethernet frames traversed switch 3, which learned both devices' MAC addresses from observing the ARP conversations. The rest of the switches in the LAN network learned workstation C's MAC address when it broadcasted its ARP packet (because switch 3 sent this ARP packet out all ports), but not the server's MAC as the server responded directly to C.
- The workstation with MAC address A now wants to use an application on the server Venus. It doesn't know the server's MAC address either, so it sends an ARP request as well, which switch 2 broadcasts out all its ports, as does switch 1 and switch 3 as the switches only look at MAC addresses and the destination MAC address of any ARP request is ff:ff:ff:ff:ff:ff, so each switch is obliged to send the broadcast frame out all ports.
However, when the server Venus responds to A's ARP packet, using A's MAC address, each switch in the path has learned which ports it saw A's MAC address come in on. So, each switch only sends Venus' response out the appropriate port back to workstation A. The same is true for learned non-broadcast frames. If a switch doesn't recognize a destination MAC address of a nonbroadcast frame, these are sent out all ports the first time as well.
As switch CAM tables get populated with MAC addresses and their associated ports, the number of frames that must be sent to every device in the LAN as well as the workload on all these devices is reduced significantly.
IP addresses and routers
When packets need to leave the LAN to get to a remote IP network, routers are required to route the packets based on their destination IP addresses. The following scenario (still referring to the preceding screenshot) illustrates some of the details involved in one possible situation.
Workstation A now wants to use an application on the server Mars, which resides on a different network than in the previous scenarios. And in this case, workstation A doesn't know the IP address of the server; it only needs its name. Workstation A will send a DNS request packet to the DNS server IP address configured in its network settings (the DNS server isn't shown here) with the hostname Mars; the DNS server will return the IP address of Mars 10.1.2.25. Workstation A calculates that this host isn't on its own network from a comparison of its IP address and subnet mask with Mars' IP address, so it sends the session initiation packet to router 1, which was configured as its default gateway in its network settings. We'll assume that Workstation A already knows the MAC address of router 1's port from a previous ARP exchange to find router 1's MAC address from the given IP address.
When the router receives A's frame, which was sent to the router port's MAC address, it inspects the destination IP address inside the IP header and looks up the appropriate port to forward the packet to. This routing process is supported by routing table entries the router builds from route information broadcasted by other routers; each router tells all the others what networks it knows a route to.
In this case, the Ethernet frame surrounding A's packet is stripped off and the remaining payload (packet) is sent across the WAN link to router 2, which also inspects the IP header destination IP address and looks up the correct port to forward the packet to. Router 2 wraps the packet in a new Ethernet frame with its own MAC address X as the source and the Mars server's Y address as the destination MAC (assuming the router already has the server in its MAC table), and transmits the packet out onto the LAN to get switched to the Mars server, as shown in the following diagram:

IP addresses and routers
When packets need to leave the LAN to get to a remote IP network, routers are required to route the packets based on their destination IP addresses. The following scenario (still referring to the preceding screenshot) illustrates some of the details involved in one possible situation.
Workstation A now wants to use an application on the server Mars, which resides on a different network than in the previous scenarios. And in this case, workstation A doesn't know the IP address of the server; it only needs its name. Workstation A will send a DNS request packet to the DNS server IP address configured in its network settings (the DNS server isn't shown here) with the hostname Mars; the DNS server will return the IP address of Mars 10.1.2.25. Workstation A calculates that this host isn't on its own network from a comparison of its IP address and subnet mask with Mars' IP address, so it sends the session initiation packet to router 1, which was configured as its default gateway in its network settings. We'll assume that Workstation A already knows the MAC address of router 1's port from a previous ARP exchange to find router 1's MAC address from the given IP address.
When the router receives A's frame, which was sent to the router port's MAC address, it inspects the destination IP address inside the IP header and looks up the appropriate port to forward the packet to. This routing process is supported by routing table entries the router builds from route information broadcasted by other routers; each router tells all the others what networks it knows a route to.
In this case, the Ethernet frame surrounding A's packet is stripped off and the remaining payload (packet) is sent across the WAN link to router 2, which also inspects the IP header destination IP address and looks up the correct port to forward the packet to. Router 2 wraps the packet in a new Ethernet frame with its own MAC address X as the source and the Mars server's Y address as the destination MAC (assuming the router already has the server in its MAC table), and transmits the packet out onto the LAN to get switched to the Mars server, as shown in the following diagram:

WAN links
Actually, network packets may traverse several routers and WAN links to reach the destination network, and each router traversed is called a hop. In the context of packet analysis, you should be aware that WAN links can introduce packet delivery delays or latency due to the following four major factors:
- Physical speed-of-light propagation delay: This is the amount of time required for electrical or light signals to travel across copper/fiber cables over long distances.
- Network routing/geographical distance: The WAN link routes are never in a straight line between points. They have to traverse major telephony switching centers and route along railways, roads, and other opportunistic paths.
- Serialization delay into and across WAN links: The WAN links are often slower speed links, and it takes a finite amount of time to send packet data across these links one bit at a time.
- Queuing delays: In network device buffers, including additional delays that may be induced by Quality of Service policies, some packets receive priority and others have to wait longer for their turn to be transmitted.
The effects of network delay incurred across LAN and WAN links can be seen and measured in Wireshark packet traces by inspecting the elapsed times between session setup packets.
Wireless networking
Wireless networks utilize a range of 802.11 specifications to provide connectivity over 2.4 or 5 GHz frequency bands at a variety of speeds. The significant differences between wireless frames and those found on wired networks are as follows:
- Wireless networks employ carrier sense (every station is listening), multiple access (shared medium), and collision avoidance (avoiding collisions instead of just recovering from them) techniques, which reduce the throughput
- In addition to data frames, which get forwarded to the wired network, wireless frame types include the following:
- Management frames: This is used for authentication and association tasks
- Control frames: This controls send/receive functions on the shared media to help avoid collisions
Wireshark can be used to capture and analyze packets on Wireless networks. However, in order to analyze the control and management frames, as well as select the radio channels to capture on without having to associate with a specific channel, specialized adapters are required. These adapters are available from various networking vendors.
These wireless adapters and their drivers enable Wireshark to display a pseudo header just below the frame header in the Packet Details pane, which includes information about:
- Data rate: This is the maximum data transfer rate possible across the radio channel
- Channel frequency: This is the RF channel frequency that the station is using
- Channel type: This is the
802.11protocol used, and the common types are a, b, g, and n - RF signal and noise levels: This is the received RF signal strength and background noise levels; the larger the difference between these two the better the signal can be decoded
Remember when analyzing wireless networks, the wireless access points utilize a wired LAN connection to the rest of the network that may warrant a separate analysis. The access point strips off the 802.11 header and encapsulates a packet in an Ethernet frame before sending the packet off on the wired network.
The following screenshot illustrates the contents of a typical Radiotap Header and IEEE 802.11 frame; note the Data Rate, Channel frequency, and Signal/Noise values:

Note
There are numerous reference materials and books that you can read to learn more about networking and network protocols. One of the classic sources is TCP/IP Illustrated Volumes I, II, and III, W. Richard Stevens, Addison-Wesley Professional, available online or in book formats.
Summary
The important points covered in this chapter included how Ethernet frames are switched to the appropriate switch ports on a LAN based on destination MAC addresses that packets are routed across and to remote networks based on destination IP addresses, and how the frames carrying packets destined for remote networks based on the destination IP address are sent to the default gateway's port MAC address.
We also covered how and why slower and/or longer distance WAN links can add significant amounts of delay to packet transmissions, which slows application data exchanges and increases user response times. We finished the chapter by discussing how Wireshark can capture and analyze packets on 802.11 wireless networks using specialized adapters.
In the next chapter, we'll cover in detail how to capture and filter packets using Wireshark.























































