There are several services that you will want to turn on when you need them. The general use of services in Windows and Linux is to have them start when the computer boots up. Most administrators spend little time managing services unless something goes wrong. In the Kali system, you will tend to shut down the workstation when you are not actually doing security analysis tasks, and you certainly do not want security tools, such as OpenVAS or Metasploit, that you have on your workstation to be accessible over the internet. This means that you will want to start them when you need them and shut them down when you are not using them.
You can find the commands to start and stop Kali Services from the Applications menu—Applications | System Services
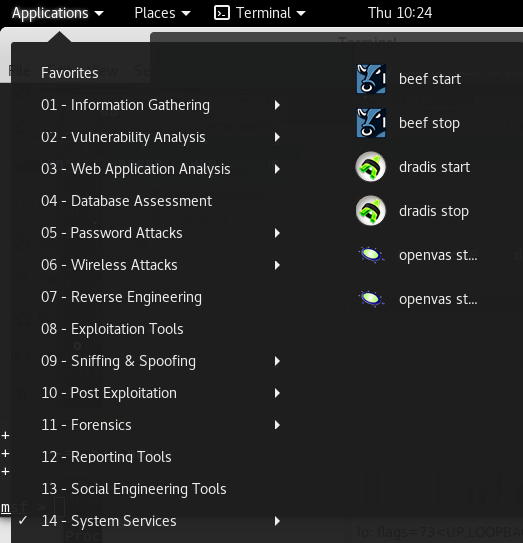
Another way to work with services is by using systemctl on the command line. As an example, consider...


























































