Promoting a server to a read-only domain controller
Read-only domain controllers were introduced with Windows Server 2008. They have been hugely popular for providing Active Directory Domain Services to branch offices and small perimeter networks.
Read-only domain controllers are the ideal type of domain controllers for environments with the following:
- Poor physical security
- Relatively few user accounts and/or devices
- Relatively poor bandwidth to central data centers with domain controllers
- Little local IT knowledge and/or experience
These characteristics are typically true for branch offices. Before read-only domain controllers, administrators had to make the hard choice between doing nothing, placing fully (read-write) domain controllers in these locations, or upgrading the available bandwidth and/or resiliency of the networking connections between the branch offices and the head office or central data center(s).
Some organizations have opted to deploy read-only domain controllers in perimeter networks. Microsoft supports only one read-only domain controller per Active Directory site. This way, any perimeter network deployment would not have much Active Directory resiliency. Many organizations have, therefore, opted for a separate Active Directory forest for these implementation scenarios.
Getting ready
Read-only domain controllers have requirements that we need to adhere to before we can deploy and use them:
- At least one domain controller running Windows Server 2008 (or a newer version of Windows Server).
- The Windows Server 2003 Forest Functional Level (FFL), or a higher FFL.
- The Windows Server 2008 Domain Functional Level (DFL), or a higher DFL, for the Active Directory domain(s) in which you intend to implement read-only domain controllers.
ADPrep /rodcprepneeds to have run at least once on the domain controller holding the Domain Naming Master FSMO role, but this step may be skipped when the Active Directory environment was never set up or has never run with pre-Windows Server 2008-based domain controllers.- When implementing read-only domain controllers for branch offices, create the corresponding Active Directory sites and site connections first.
- Check for proper Active Directory replication before implementing a read-only domain controller.
Read-only domain controllers allow for scoped replication. It's a recommended practice to determine the user accounts and computer accounts that are strictly needed in the branch office location. The read-only domain controller will be able to cache the passwords for these accounts to speed up authentication for these accounts in the branch office. The Allowed RODC Password Replication Group is the default group in which to add (groups of) user accounts and computer accounts for this functionality.
If you desire strict group memberships for this functionality per read-only domain controller, create the groups you need before you promote the Windows Server installation to a read-only domain controller for which you need the group scope.
Another way to think about security before promoting the first read-only domain controller is to determine the privileged accounts and otherwise sensitive accounts for which you do not want passwords replicated to the read-only domain controller you intend to create. These (groups of) accounts can be specified as the accounts that are denied from replicating passwords to the RODC.
How to do it...
Just like read/write domain controllers, promoting a Windows Server installation to a read-only domain controller consists of three steps:
- Installing the Active Directory Domain Services role
- Promoting a server to a domain controller
- Checking proper promotion
When using dcpromo.exe, you do not have to install the role beforehand.
There are several ways to promote the server. The following table displays the possibilities:
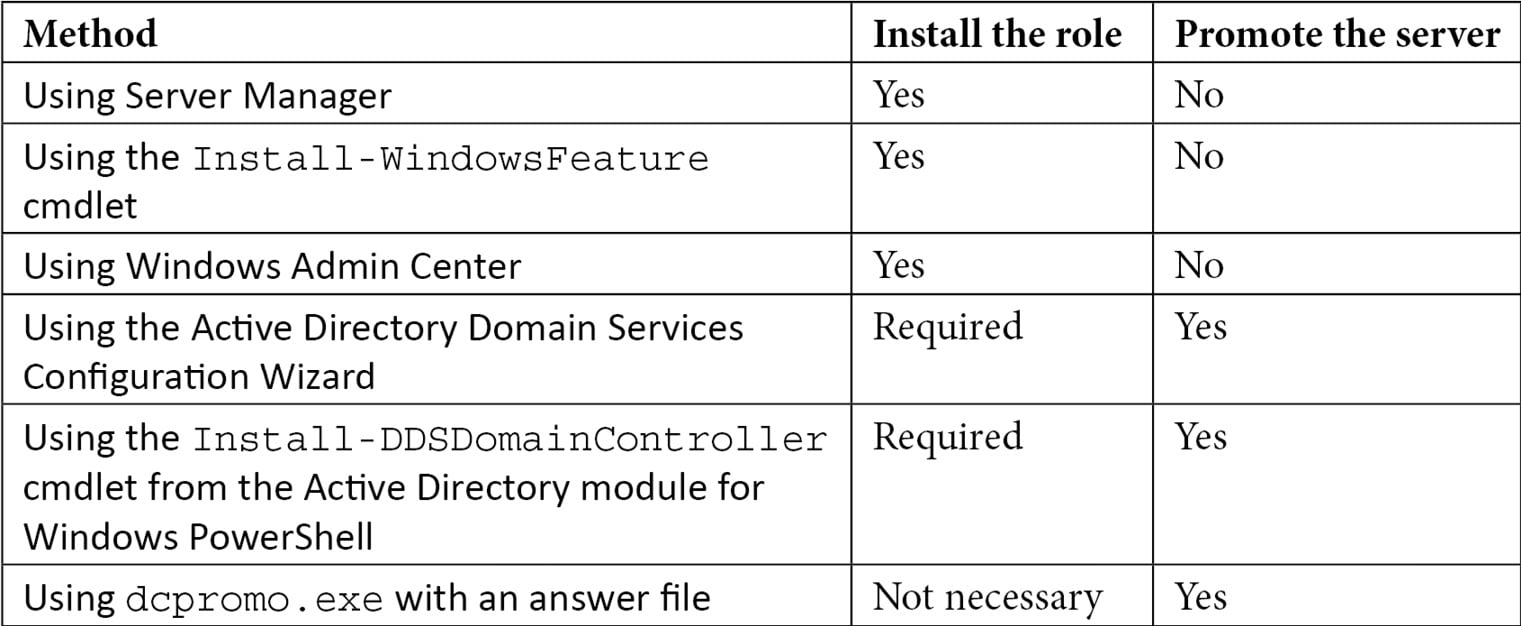
Table 2.3 – Methods for installing the Active Directory Domain Services role and promoting a server to a domain controller
The methods in the table are all explained in more detail in this recipe.
Installing the Active Directory Domain Services role
There are three ways to install the Active Directory Domain Services role:
- Using Server Manager
- Using the
Install-WindowsFeaturecmdlet - Using Windows Admin Center
Using Server Manager
To install the Active Directory Domain Services role using Server Manager, perform these steps:
- Press Start.
- Search for Server Manager and click its corresponding search result or run
servermanager.exe. The Server Manager window appears. - In the gray top bar of Server Manager, click Manage.
- Select Add Roles and Features from the menu. The Add Roles and Features Wizard window appears, with the Before you begin screen.
- On the Before you begin screen, click Next >.
- On the Select installation type screen, select Role-based or feature-based installation and click Next >.
- On the Select destination server screen, select either the local Windows Server installation from the server pool list, the remote Windows Server installation you intend to promote to the domain controller from the server pool list, or both types of resources.
- Click Next >.
- On the Select server roles screen, select the Active Directory Domain Services role from the list of available roles. The Add Roles and Features Wizard pop-up window appears.
- On the pop-up screen, click the Add features button to add the features that are required for Active Directory Domain Services. These features include the Group Policy Management tool, Active Directory module for Windows PowerShell, Active Directory Administrative Center, and AD DS Snap-Ins and Command-Line Tools.
- Back on the Select server roles screen, click Next >.
- On the Select server features screen, click Next >.
- On the Active Directory Domain Services screen, providing an overview of Active Directory and Azure AD, click Next >:
Figure 2.8 – Methods for installing the Active Directory Domain Services role and promoting a server to a domain controller
- On the Confirm installation selections screen, click Install.
- When configuration of the Active Directory Domain Services server role is done, click Close to close the Add Roles and Features Wizard.
Using the Install-WindowsFeature cmdlet
As an alternative to using Server Manager, the Install-WindowsFeature cmdlet
can be used. Perform the following line of Windows PowerShell in an elevated window to install the Active Directory Domain Services role:
Install-WindowsFeature AD-Domain-Services -IncludeManagementTools
The preceding line of Windows PowerShell offers the only way to install the Active Directory Domain Services role on a Server Core installation of Windows Server locally.
Using Windows Admin Center
Although a PowerShell script can be run from the Windows Admin Center, it also offers a native way to install roles and features. Perform these steps:
- In the Windows Admin Center, click the Windows Server installation you want to install the Active Directory Domain Services role onto from the list of All Connections.
- In the left navigation menu, click Roles & features.
- In the main pane, select the Active Directory Domain Services role from the Roles and features list by clicking the selection box to the left of it.
- Click + Install. The Install Roles and Features blade appears.
- Click Yes to continue the installation with the additional Active Directory module for Windows PowerShell, Group Policy Management, AD DS Snap-Ins and Command-Line Tools, and Active Directory Administrative Center features installed.
- A notification pops up informing you that Windows Admin Center has Successfully completed installation of Active Directory Domain Services, which appears in the notification area when the roles and features have been successfully installed.
Promoting the server to a domain controller
There are three ways to promote a Windows Server installation to a read-only domain controller:
- Using the Active Directory Domain Services Configuration Wizard
- Using the
Install-ADDSDomainControllercmdlet from the Active Directory module for Windows PowerShell with the dedicated-ReadOnlyReplicaparameter - Using
dcpromo.exewith an answer file
Using the Active Directory Domain Services Configuration Wizard
Perform these steps to promote the server to a read-only domain controller:
- Press Start.
- Search for Server Manager, click its search result, or run
servermanager.exeor return to Server Manager when you've accomplished installing the Active Directory Domain Services role using Server Manager. - In the left navigation pane, click AD DS.
- Click the More... link in the yellow ribbon titled Configuration required for Active Directory Domain Services at server.
- In All Servers Task Details and Notifications, follow the Promote this server to a domain controller link. The Active Directory Domain Services Configuration Wizard window appears.
- On the Deployment Configuration screen, select Add a domain controller to an existing domain. Then, input the DNS domain name and administrator credentials for the Active Directory domain for which you intend to add a read-only domain controller. Click Next > to proceed to the Domain Controller Options screen:
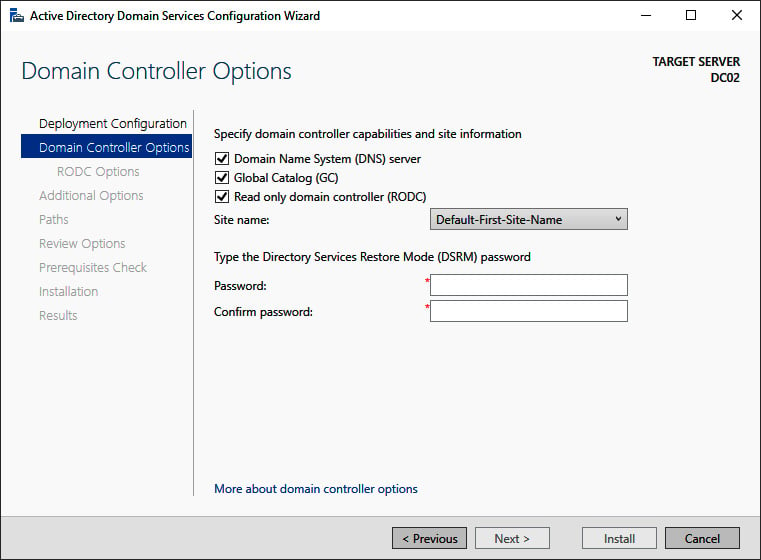
Figure 2.9 – The Domain Controller Options screen of the Active Directory Domain Services Configuration Wizard
- On the Domain Controller Options screen, we're presented with a few options:
- Select the Read only domain controller (RODC) option.
- When preferred, select the Domain Name System (DNS) server and Global Catalog (GC) options.
- Select a site name from the drop-down list of available Active Directory sites.
- Enter the Directory Services Restore Mode password for the intended read-only domain controller.
- Click Next > to proceed to the RODC Options screen:
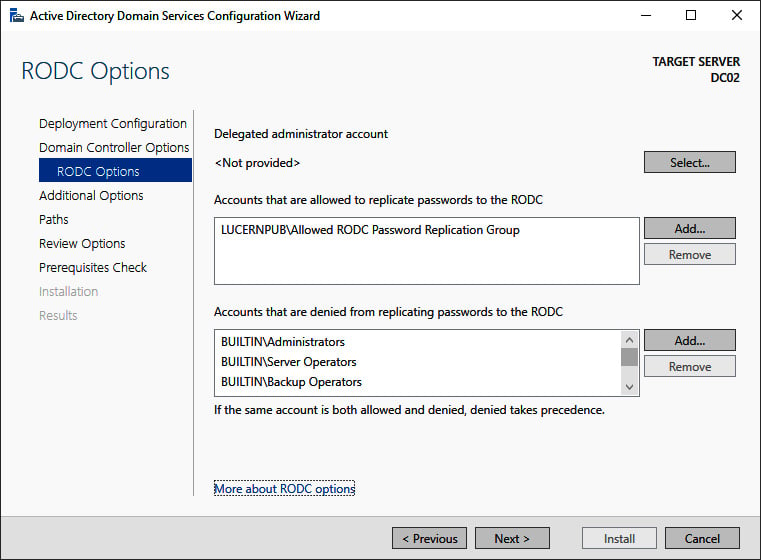
Figure 2.10 – The RODC Options screen of the Active Directory Domain Services Configuration Wizard
- On the RODC Options page, perform the following optional actions:
- Select a user account for delegation.
- Select Accounts that are allowed to replicate passwords to the RODC.
- Select Accounts that are denied from replicating passwords to the RODC.
Tip
If a group or an account features in both the accounts that are allowed to replicate passwords to the RODC and accounts that are denied from replicating passwords to the RODC, then the group or account is denied from replicating passwords to the RODC.
- Click Next > to proceed to the next screen.
- On the Additional Options screen, optionally select a fully writable domain controller from which to replicate the Active Directory database and the Active Directory
SYSVOL. Click Next > to continue to the Paths screen:
Figure 2.11 – The Paths screen of the Active Directory Domain Services Configuration Wizard
- On the Paths screen, verify the default locations underneath
C:\Windowsor change the values to store Active Directory-related files somewhere else. - Click Next > to proceed.
- On the Review Options screen, review the choices made. Click Next > to proceed to the Prerequisites Checks screen.
Tip
The Review Options screen features a button labeled View script. This button displays the Windows PowerShell script used to execute the read-only domain controller promotion. This reusable script may be a real timesaver, especially when adding several read-only domain controllers to an existing domain.
- After the prerequisites checks have been performed, click Install on the Prerequisites checks screen to start promotion.
After successful promotion, the Windows Server installation will reboot as a read-only domain controller.
Promoting a read-only domain controller using Windows PowerShell
For the Active Directory module for Windows PowerShell, Microsoft does not offer a dedicated PowerShell cmdlet to add a read-only domain controller. Instead, Install-ADDSDomainController is used with the dedicated -ReadOnlyReplica parameter. The simplest script would look like the following code:
Install-ADDSDomainController -DomainName lucernpub.com -Sitename RemoteLocation -ReadOnlyReplica
However, to add a read-only domain controller to an existing domain as you would with the previous example, the following script would be needed:
Install-ADDSDomainController -DomainName lucernpub.com -Credential (Get-Credential) -ReadOnlyReplica -installDNS:$true -NoGlobalCatalog:$false -DatabasePath "E:\NTDS" -Logpath "E:\Logs" -SysvolPath "E:\SYSVOL" -Sitename RemoteLocation
This will add a read-only domain controller to the lucernpub.com Active Directory domain using credentials you will be prompted for securely. The domain controller will be installed with a DNS server and configured as a global catalog server. All the Active Directory-related files are stored in corresponding folders on the E:\ drive, and, when successful, the Windows Server installation you intend as the domain controller will be rebooted automatically.
Replace the values in the preceding sample script with the values of your choice.
Promoting a read-only domain controller using dcpromo.exe
Read-only domain controllers can be promoted using dcpromo.exe with an answer file or with all the installation arguments specified, just like fully writable domain controllers. An added benefit is that dcpromo.exe will install the Active Directory Domain Services server role automatically when it's not yet present.
Using dcpromo.exe with an answer file consists of running the following command line:
dcpromo.exe /unattend: C:\install\dcpromo.txt
A prime example of an answer file to add a read-only domain controller would look like this:
[DCINSTALL]
ReplicaorNewDomain= readonlyreplica
ReplicaDomainDNSName= lucernpub.com
UserDomain= LUCERNPUB
UserName= Administrator
SiteName= RemoteLocation
Password= "P@$$w0rd"
InstallDNS= Yes
ConfirmGC= Yes
CreateDNSDelegation= No
DatabasePath= E:\NTDS
LogPath= E:\Logs
SYSVOLPath= E:\SYSVOL
SafeModeAdminPassword= "P@$$w0rd"
RebootOnSuccess= true
The preceding answer file adds a read-only domain controller to the lucernpub.com Active Directory domain, using the credentials for the administrator account with the P@$$w0rd password. The read-only domain controller is installed with a DNS server and configured as a global catalog server. All the Active Directory-related files are stored in corresponding folders on the E:\ drive, and when successful, the Windows Server installation you intend as the read-only domain controller is rebooted automatically.
Replace the values in the preceding sample file with the values of your choice.
The arguments in the answer file can also be specified as command-line arguments. The arguments can be reused one on one, so the preceding sample answer file would correspond to the following command line:
dcpromo.exe /unattend /replicaornewdomain:ReadOnlyReplica /replicadomaindnsname:lucernpub.com /userdomain:LUCERNPUB /username:administrator /password:"P@$$w0rd" /sitename:RemoteLocation /installdns:yes /confirmgc:yes /databasepath:"E:\NTDS" /logpath:"E:\logs" /sysvolpath:"E:\sysvol" /safemodeadminpassword:"P@$$w0rd"
Replace the values in the preceding command line with the values corresponding to your environment.
Checking proper promotion
After promoting a Windows Server installation to a read-only domain controller, it's recommended practice to check for proper promotion. Perform these steps to check:
- Check the logs: The following two files contain all the actions performed when promoting the Windows Server installation to a domain controller. A good way to check for improper promotion is to search for lines containing errors and warnings, logged in the following files:
C:\Windows\Debug\dcpromo.logC:\Windows\Debug\dcpromoui.log
- Check the event viewer: In the event viewer,
eventvwr.exe, new dedicated logs are created for Active Directory Domain Services. Search these logs for any Active Directory-related errors. - Run Windows updates: Even though one of the recommended steps is to update the Windows Server installation you intend to promote to a read-only domain controller, it's also a recommended step to install Windows updates after the Windows Server installation has been promoted, as updates apply to the newly installed server roles and features too. These role-specific updates are only applied after the role is installed.
How it works...
Read-only domain controllers are different from normal domain controllers in the following ways:
- They allow read-only access to the Active Directory database and SYSVOL. Read-only domain controllers refer to other domain controllers for write operations such as SYSVOL.
- They allow read-only access to the DNS records. Read-only domain controllers refer to other domain controllers for DNS registration requests.
- They allow for scoped replication, so only the accounts that are needed in the Active Directory site where the read-only domain controller is placed are synchronized. This way, privileged accounts and other sensitive accounts remain in the central data center.
- They allow for a quick change of passwords for synchronized users when the read-only domain controller is stolen or otherwise compromised.
- They use their own dedicated account to encrypt their Kerberos tickets. This prevents attackers from decrypting a Kerberos Ticket Granting Ticket (TGT), issued by a read-only domain controller, to obtain the secret of the Kerberos account (
krbtgt).
Additionally, because no Active Directory writes are expected from read-only domain controllers, normal domain controllers don't replicate from them.
See also
For more information, refer to the following recipes:
- See the Preparing a Windows server to become a domain controller recipe.
- See the Promoting a server to a domain controller recipe.
- See the Creating an Active Directory site recipe in Chapter 16, Hardening Azure AD.
- See the Checking replication recipe in Chapter 16, Hardening Azure AD.
































































