What is an IDS?
An IDS works by monitoring network traffic, system logs, and other relevant information to identify and analyze patterns and signatures associated with known threats or abnormal behavior. The primary goal of an IDS is to detect and alert security administrators about potential threats or breaches. When an IDS identifies suspicious behavior or patterns, it generates an alert, notifying the security team to take appropriate action.
Types of IDS
There are two main types of IDS: NIDS and host-based IDS (HIDS). The main difference between a NIDS and a HIDS is the monitoring scope and types of activities they detect. Have a look at the following table to look at the differences:
|
NIDS |
HIDS |
|
|
Scope |
It works at the network level, monitoring the data going to and from different devices to look for abnormal behaviors or events that might indicate an intrusion. |
It is installed directly on the host’s and monitor’s log files, system calls, file integrity, and other host-specific files for any unusual activities. |
|
Location |
Functions at one or more central places in a network’s infrastructure to monitor and analyze traffic going through those points. |
Operates locally on individual hosts or devices, keeping an eye on actions that are unique to that machine. |
|
Detection focus |
A NIDS detects network attacks and anomalies. It can detect port scans, DoS attacks, intrusion attempts, and other network infrastructure threats. |
A HIDS monitors host activity. It detects unauthorized access, file system changes, critical system file modifications, and suspicious processes or behaviors that may indicate a compromised host. |
|
Popular tools |
Suricata, Snort |
Wazuh, OSSEC |
Table 1.1 – NIDS versus HIDS
In the following diagram, you can see that a NIDS is installed to monitor network traffic while an HIDS monitors individual devices.
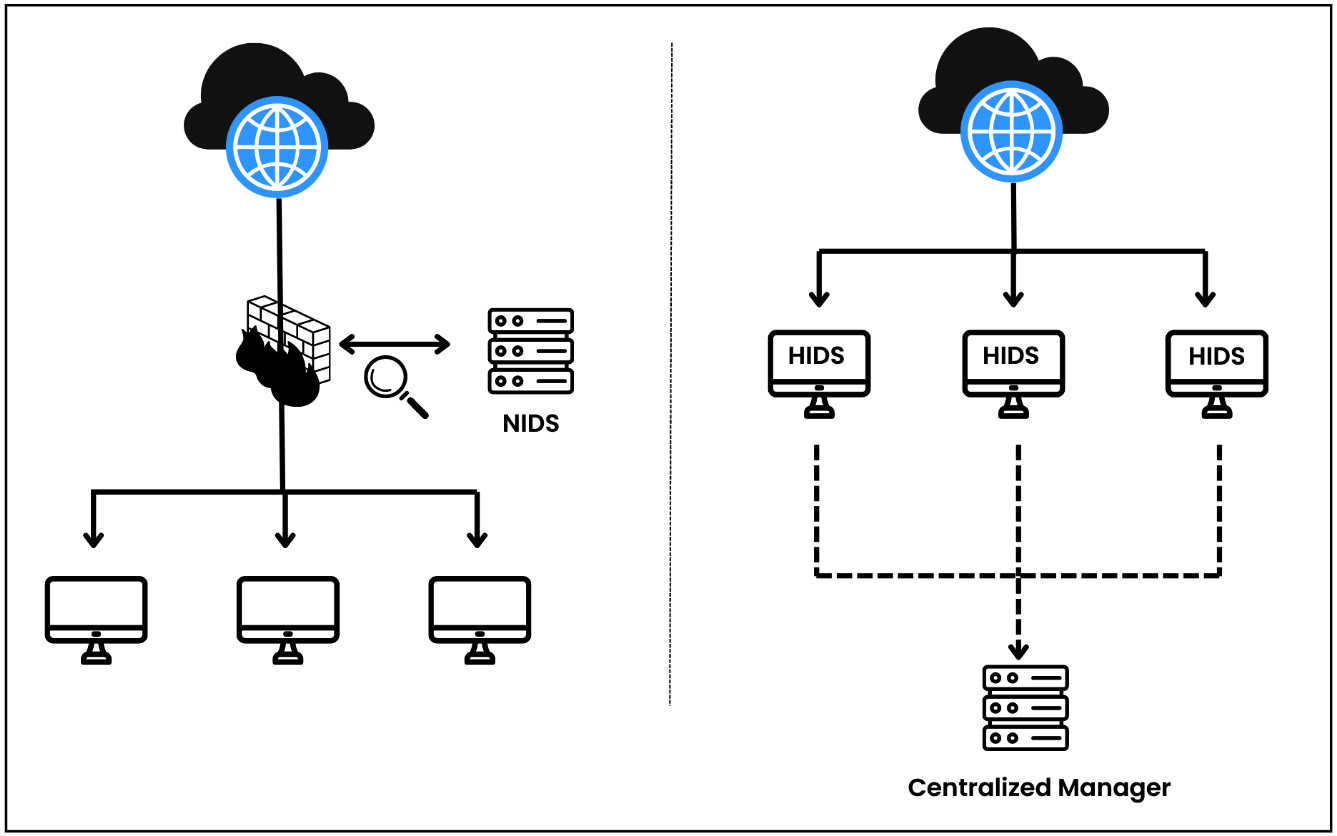
Figure 1.1 – NIDS versus HIDS

































































