Evaluating the efforts of controls
The following recipes provide information on how to evaluate controls based on the benefit they have for your business.
Getting ready
Understanding the controls considered and the one-time cost and operational cost associated with them.
How to do it...
When identifying and deciding on the controls, bear in mind the principle keep it simple. Most authority documents only require evidence of compliance but do not demand certain controls. Therefore, use controls that are available within your company whenever possible. When brainstorming for possible controls for a given requirement, use the most efficient and cost-effective one. Many times, one control might not be sufficient, and several controls may have to be implemented to get the desired effect.
The most straightforward approach is to look at the objective and answer the question whether the control will reduce the risk of reaching your objective within an acceptable level. An acceptable level could mean that some controls will not reach their goal. To do this, a matrix is a great help.
A more holistic approach is harder to evaluate, as the cost of a control is most often easier to calculate than the benefit it creates. Still, it should be considered. When deciding on the right control, do not only look at the control itself but at the broader scope the control has on your business. It is important to understand what technology could be used to implement this control or what technology is underlying the control and could be used to create benefits to the business. The following illustration provides some examples on cost versus benefit for controls that help evaluate which controls to choose:
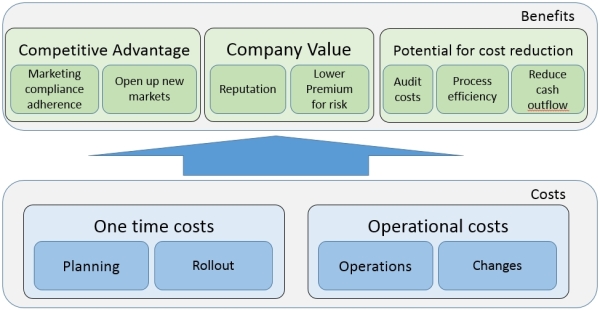
Automated controls are always more desirable than manual ones. The cost effectiveness of such controls comes from the following:
- Automation of monitoring and regulation activities
- Achievement of a much higher coverage through automated controls, for example, an example eliminating a higher percentage of (fraud) risks
- Creating process efficiency
- Creation of objective controls as they lower audit costs
In the previous recipes, we talked about compliance requirements for access and authentication management. In the next recipe, we will discuss authorization.
Access and identity management is a compliance requirement that is found in different regulatory requirements. In cases where identity lifecycle management is purely a manual activity, creating controls for this might may seem like creating more manual work; however, by introducing Microsoft Active Directory Domain Services, the identity lifecycle management process, including deletion and changes, will be more efficient.
GPO for password compliance is an automated control already within the AD DS. The only manual effort is deciding on GPO and configuring it within AD DS. The overall one-time cost of planning an Active Directory Domain and implementing it will outweigh the cost and resources required for manual activities, such as using creation and management in each and every application as well as ensuring password compliance to meet requirements. Hence, the potential exists to create more efficient processes within systems and applications.
Audit costs are quite often lower for automated controls than for manual ones. Automated controls do not face the risk of human error or subjective interpretation. Therefore, auditors require more evidence that a manual control is effective, thus qualifying for the goal of the control.
Another qualifier for an automated control is a detective one, as those could help to minimize undesirable cash outflow. Think about an example; suppose that the wrong supplier has been chosen, leading to the loss of favorable supplier conditions, such as discounts.
The competitive advantage should be considered to evaluate the usage of a control. Controls help prevent failure of the company or a certain unit. As an example, take PCI DSS and the result of noncompliance.
Creating a compliance program could open up new markets, while noncompliance could eliminate them. The PCI DSS mentioned in the previous recipe is an example of eliminating a customer base in the case of noncompliance. As mentioned before, without compliance, the credit institutes reserve the right to revoke processing of credit cards.
Another competitive benefit of compliance controls is opening up new customers and markets. One of the most basic compliance regulations, tax compliance, is such an example. In many countries, governmental bidding invitations are only open to companies that have declared tax in time and have paid their taxes. The consequence of noncompliance could be the loss of potential orders.
More companies demand certain IT security certification to be eligible to provide a bid. As IT security is one of the aspects of many regulatory requirements, the first step toward such a certificate is already made.
How it works...
Evaluating the effectiveness of a control requires research on your part to understand the impact they have on the business. At one side are the costs incurred by them, and on the other side are the possible benefits when implementing them.
































































