Exploring the foundations of cybersecurity
What is cybersecurity? Cybersecurity defines processes, technology, and design frameworks developed to protect organizations' devices, programs, data, and other valuable assets from unauthorized access from a cyber threat.
This section will provide you with a basic understanding of cybersecurity, key terms such as risk versus vulnerability, and different cybersecurity frameworks, which include the CIA Triad, NIST, ISO, and SOC2.
Threats, assets, vulnerabilities, and risks will be covered in the following section. We will explain the fundamentals of how cybersecurity professionals protect data, devices, networks, and systems from attacks from viruses, malware, hackers, and data breaches.
Asset, vulnerability, risk, and threat
Some terms you will hear often within cybersecurity are asset, vulnerability, risk, and threat. These are key terms you should learn and know. We will cover these briefly in this section
Here are their breakdowns:
- Asset: This is anything in the environment that needs to be protected, such as data, people, proprietary tools, and processes essential for business operations.
- Vulnerability: A weakness within your organization that can be exploited, such as flaws in software code and out-of-date software.
- Risk: The likelihood or possibility a threat was successful in breaching your network, the risk would be the asset's total loss. The following is an example of the risk formula to identify your organization's risk:
Risk = Threat x Vulnerability
- Threat: Anything that is trying to degrade, disrupt, or steal your asset is a threat. This would include cybercriminals or insider threats.
The preceding is not an inclusive list, it is the basics to help you get started. We encourage you to dig further into each of these to understand their roles within cybersecurity. Next, we will discuss the CIA Triad.
What is the CIA Triad?
The CIA Triad is not the Central Intelligence Agency composed of US government employees who provide national security intelligence to congressional leaders in America. The CIA Triad in cyber means Confidentiality, Integrity, and Availability. These are the core pillars of information security (InfoSec) a subset of cybersecurity. Throughout this chapter, we will focus on the CIA Triad three pillars as they are foundational elements of InfoSec.
The CIA Triad will be referenced throughout your career because it's the foundation in developing information security policies.
"So, what is the CIA Triad?" We are happy you asked. We will explain the CIA Triad by using the following diagram:
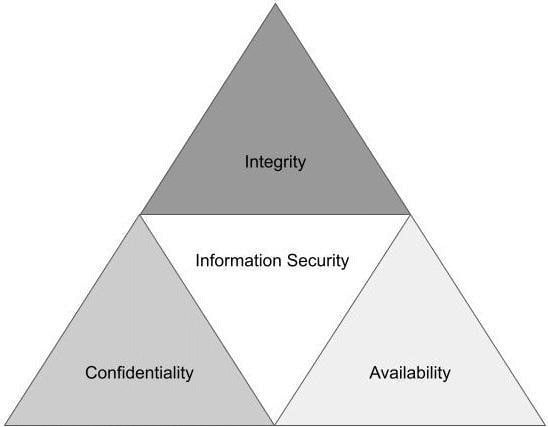
Figure 1.1 – CIA Triad
The easiest way of thinking about the CIA Triad is as a security model to help unpack various information technology (IT) security components. This model helps develop security policies to identify problem areas on a network while providing appropriate solutions. In the next section, we dissect each pillar in more detail.
Confidentiality
The best way to think about confidentiality is ensuring that only select users can access specific data. This could include encryption techniques, but there are far more ways to achieve confidentiality on a network.
Generally, all organizations have some form of sensitive information. This may include client data, company proprietary data, and customer or employee personal identification information (PII). Most companies' information systems store information that has some degree of sensitivity.
Data is the new gold and criminals target organization data in the hope of either encrypting or stealing data. Then the organization are forced to pay large ransoms to get it back. A common attack technique is a ransomware attack, where a criminal either encrypts or steals your data then holds it hostage until you pay the ransom using cryptocurrency.
Note
Cybercriminals will often target organizations with significantly more sensitive data because they know the payout will be larger.
An attack vector used for a ransomware attack is a phishing email. Once the threat actor has successfully breached the network, the second phase of an attack could include password stealing, credential harvesting, and data encryption.
Not all data breaches are criminal in action, meaning someone in the organization could share classified information with someone who does not have the appropriate classification to read the data. An example could include forwarding an email to the wrong Susan Smith. Instead of sending it to Susan Smith in Countermeasure, they instead sent it to Susan Smith in Human Resources. Another example is leaving a computer unattended and the email inbox open with PII data exposed for another employee to see.
An intentional or unintentional data breach will lead to the same result: sharing confidential data with those who do not have access.
Countermeasures to help reduce the likelihood of a data breach and increase confidentially would include the following:
- Access control list
- File and volume encryption
- Authentication through software to control access
- Administrative policies
- Continuing employee training and awareness
- Physical hardenings such as cameras and access control
The preceding countermeasures should be part of a layered security approach. It is best to have multiple security countermeasures in place to protect the confidentiality of data.
Integrity
This pillar ensures that your data stays intact and is not changed or altered. This provides data assurance, completeness, and accuracy. Data integrity is essential for both data at rest (stored data) and at flow (emails). Integrity maintenance starts with access control and ensuring that only authorized users have access to modify data.
Data integrity protection extends beyond malicious attacks. Unintentional alterations can occur if access controls are not maintained and the employee obtains access to a file and deletes or alters files, causing data loss or, network complications.
Try searching Largest data breach of today, or Largest data breach of 2021, and more than one article about different breaches will come up. Why? Because data breaches are becoming more and more prevalent and, unfortunately, will never go away.
Hackers are becoming more creative and finding novel ways to lure their victims into their clickbait. The cyberwar between cybercriminals and cybersecurity experts is a cat and mouse game. The number one thing you can do to protect integrity of data is ensure your organization's countermeasures are maintained regularly. Authentications should be robust, with access control updated regularly to help prevent unauthorized access to networks and files.
Another great example of how integrity of data is being questioned are through deep fakes. Deep fakes are videos or photos that look and sound like the real thing. As technology becomes better, identifying deep fakes becomes more challenging. The integrity of the document or photo is then in question and can create a myriad of other problems.
Availability
Availability ensures that the users have timely and uninterrupted access to information, systems and networks. How many times have you been working and suddenly your cloud storage stops working or the document you were working on is gone or corrupt? Availability ensures access to data at any time without any obstacles such as network outages or data breach.
A malicious attack includes cyber-espionage, where the attacker's intent is to impact the network by encrypting all the data. By denying access to the data, organizations are forced to pay the ransom or start over from scratch, which can also cost a lot of money and time. There are unintentional and non-malicious activities that impact availability that include natural disasters, bandwidth, or unscheduled software updates.
Important note
Certain individual states in the United States are proposing new laws to ban ransom payments to cybercriminal.
An example attack method that adversaries use to disrupt companies' data availability is known as Denial of Service or DoS attacks. This is an unsophisticated attack in which an attacker will flood a server with requests to overwhelm and disrupt the web service or degrade services for clients and employees.
Countermeasures to strengthen availability are as follows:
- Large organizations should consider hardware redundancies such as backup servers and data storage availability.
- Automatic cloud-scaling capabilities.
- Monitoring software such as endpoint protection to monitor the network for performance will help prevent unwanted traffic.
- Standard firewalls and routers should be updated regularly to ensure compliance.
At this point, you should have a solid foundational understanding of the CIA Triad, its purpose, and how to apply it within your organization. Next, we will cover three different cybersecurity frameworks. This is dense information, so I completely understand if you are reaching for something a little stiffer than water.
Different cybersecurity frameworks
The first cybersecurity framework we will discuss is NIST. NIST stands for National Institute of Standards and Technology. NIST is a framework that helps a company develop organizational controls and risk management for their information security program.
Important note
There are other internationally recognized security frameworks not covered in this book; these include IASME, COBIT, and CIS.
The NIST framework is broken into three parts:
- Framework Core
- Implementation Tiers
- Framework Profiles
Framework Core
The Framework Core is made up of five functions. The easiest way to remember them is to think of Identify and Protect as the organization's actions to prepare itself against a cyberattack. Detect, Response, and Recover are all the things you will do after a breach or incident occurs.
The five core functions are as follows:
- Identify: Manages risks by correctly understanding assets, data, and other resources.
- Protect: Protocols and countermeasures in place to protect critical infrastructure.
- Detect: Defines what makes an event versus regular network activity.
- Respond: Response to events through predefined actions.
- Recover: Recovery processes for repair services and network.
If you want to learn more about NIST and download the framework's Core Function and Category spreadsheet, you can visit https://www.nist.gov/ and search for NIST Framework.
Implementation Tiers
The Implementation Tiers are a total of four tiers, which range from partial to adaptive. Figure 1.2 provides you with a graphic depiction of the NIST Tiers and the degree to which information is shared, and how well cybersecurity risk and decisions are integrated into the organization's broad spectrum:
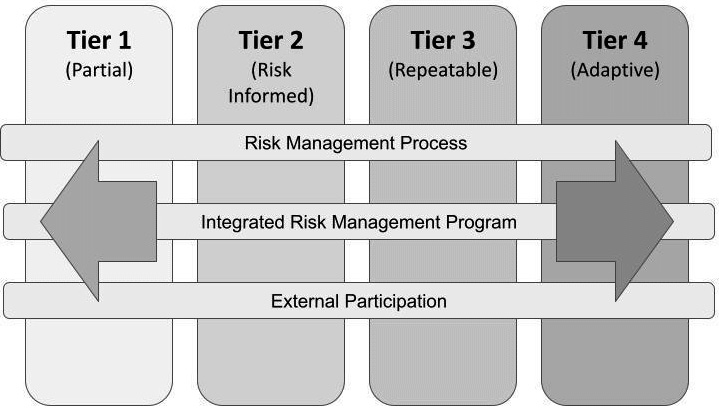
Figure 1.2 – NIST Implementation Tiers
These Tiers are defined by the organization requirements' objective. The organization must decide its level of risk, resources, and tools to defend against a breach.
Framework Profiles
The last portion of the NIST Framework is optional but highly encouraged because it helps an organization define its unique security posture objectives. Protection of data is essential, and companies must clearly define their risks and resources. The Framework Profiles are used to identify opportunities for refining or improving overall cyber hygiene. Organizations can have a current and future profile for their end state. A business may also have different profiles based on their business needs and capabilities. This process takes time and should be looked at as an ongoing and never-ending process.
Organizations should always be working on their current cyber profile to identify opportunities to increase cyber awareness and harden overall cybersecurity posture to improve security.
ISO Cybersecurity Framework
ISO 2700/27001 was created by the International Organization for Standardization. Their certifications are recognized internationally as the international standard for validation for cybersecurity programs. This standard is more risk-based focused versus technical focus.
Important note
Cybersecurity risk is an organization's probability of exposure or loss resulting from a data breach or cyberattack. When an organization takes a risk-based approach, it typically means the organization uses a methodology based on the analysis of the risk and the risk of the management framework.
This framework has over a dozen different standards for organizations to use for their security management of assets.
SOC2 Cybersecurity Framework
SOC2 stands for Service Organization Control Type 2 and is a cybersecurity framework and auditing standard developed by the American Institute of Certified Public Accountants (AICPA) to ensure organizations are securely managing client and vendor data. NIST and SOC2 may appear to be opposite sides of the same coin; both are designed to review an organization's internal controls.
Note
NIST offers a framework for InfoSec and privacy controls while SOC2 enables organizations to obtain certifications of compliance.
We encourage you to take additional time and look into these frameworks, and the others, when you have more time. Next, we will discuss the different types of cyber attacks.
Types of cyber attacks
There are a lot of terms you will learn and need to understand to speak cyber. Terms used to explain certain cyber attacks are essential to know so you can understand the threat to then implement the proper countermeasure to mitigate the threat. For example, if an organization was concerned about a Distributed Denial of Service (DDoS) versus a phishing attack, the infosec team would have different countermeasures to investigate and mitigate the risk.
This section describes the top 10 most seen cyberattacks. This is basic information designed to provide a high-level context of different threats.
Distributed Denial of Service (DDoS)
A DDoS attack is achieved when an adversary targets your network and floods it with a high number of packets. This type of attack is measured by the amount of bandwidth involved. An example is in 2019 when a DDoS attack impacted GitHub. GitHub reported a peak of 1.35 terabits per second. At the time, this was the largest DDoS attack to date.
What happens during at attack like this is the threat actor will overwhelm the server and make it impossible to conduct business as usual (BAU). Unlike most attacks, where the attacker is trying to gain access, a DDoS is designed to degrade the company network and denial of service.
If you see a DDoS attack, it's likely an unsophisticated attack. However, recently, experts are beginning to see cybercriminals using DDoS as a secondary attack vector layered onto a primary attack. An example is when a threat actor targets a victim using a phishing lure. Once successful, they will encrypt all the victim's data. If the client refuses to pay the ransom, the threat group will conduct a DDoS on their network to disrupt it enough, making it impossible to conduct BAU. Eventually, the victim will pay or wipe everything and migrate to an entirely new server, which can be very costly with a lot of downtime.
Here are some types of DDoS attacks you may see:
- TCP SYN Flood attack: This happens during the Transmission Control Protocol (TCP) session when initializing a handshake. They exploit the buffer space and overload the system with connection requests.
- Smurf attack: The attack will spoof a known IP address and the Internet Control Message Protocol (ICMP) to overwhelm the target network. This is an echo request targeted at a select range of IPs with a response reaching back to the spoofed IP.
- Teardrop attack: The attacker will overlap the length and fragment fields within sequential IP, causing the system to try and fail at reconstructing the packets making the system stop working.
- Ping of Death attack: This attack uses IP packets to ping a target network and a large IP size. When the IP packet is not allowed, the threat actor will fragment the IP. Once the system accepts the packet, it will then experience buffer overflows and crashes.
Man-in-the-Middle
Man-in-the-Middle is when an adversary places themselves between a client and server's communication. This is when the following could occur:
- Session hijacking: This is when the attacker can control the client and then disconnect the client from the server. Once disconnected, the attack will replace the host machine IP address with the attacked IP address then spoof the client sequence number. The computer would look like BAU while under the control of the attacker.
- IP spoofing: This is when the attacker uses what appears to be a legitimate IP address to communicate with the host computer. The host machine could accept the packet from the spoofed IP and act upon it.
- Replay: The attack will replay an old message to obtain access to a system. This is accomplished when the attackers intercept a message to save for later use.
Mitigation techniques include using secured session tokens, time-stamping messages, and secure DNS. Multi-Factor Authentication, or MFA, and digital certificates also help to mitigate these attacks and aid in keeping confidentiality and integrity intact during communication.
Note
MFA is a multi-step authentication process to grant users access to specific applications. Examples of MFA include something you know, something you have, and something you are. Examples would be a password, an authenticator code, and a fingerprint.
Phishing, spearphishing and business email compromise attacks
Phishing is the most used vector for cyberattacks. Phishing attacks can be divided into three different attacks listed below.
- Spearphishing: Targeted attack that focus on a small group of people or organization.
- Business Email Compromise (BEC): Targets higher leadership or someone who can make purchases. Typically, the lure in this attack will be about a gift card purchase coming from a trust source
- Phishing: Untargeted attacks sometimes referred to as a "spray and pray" attack. Spray and pray are the most common phishing attacks and they are designed to hit a larger number of emails without a specific target in mind.
Typically, the emails will come from a trusted source to lure its victims to click. They will also use emotional queues to get their victims to click, such as urgency or money tied to the message.
Most organizations have certain protocols to ensure their employees are trained to identify a phishing email versus a legitimate email.
Drive-by attack
Have you ever seen an advertisement online to win an iPad? Surprise, you never win an iPad, but you might win new malware on your computer. These attacks are called drive-by compromises because they lure their victims by setting clickbait on either legitimate websites or within a search engine.
Protection from these attacks could include spam-blocking software and maintaining an updated and patched browser. Try to avoid having too many unnecessary programs, browser extensions, or apps on your computer. These are third-party vendors that could be hacked and could impact you and your security.
Password attack
Attackers know if they obtain your password, they will likely have access to others areas of your system.
Tip
Do not use the same password for everything. Consider the strength of the password to the data you are attempting to protect. The password for your bank account should be stronger than the password you use for your video streaming platform. Both have personal data, but one has more critical data than the other.
Some of the techniques used for password hacking includes brute-force and dictionary attacks:
- Brute-force attack is when the attacker will rely on guessing, often through automation, and attempting as many times as possible. Typically the guesses are attributed back to the user's likes and hobbies. If your password is complex enough, it will take a long time to crack it.
- Dictionary attack is when the attacker attempts to use the most common passwords.
If either of these attacks are successful, the attacker will gain access to your machine and can collect or encrypt your data.
MFA helps mitigate this risk, as do timeouts.
Note
Timeout sessions are examples of when a user is logged off after idle time or after a certain period of time such as 12 hours. Then the user must re-authenticate to begin the session again.
Cross-site scripting attack
A cross-site scripting attack happens when a user goes to a legitimate website that was injected with malicious code. When the victim visits this website, the website will transmit the page with the attack payload in an HTML text. Then the malicious script will execute on the host machine. The outcome could be seen by stealing cookies, capturing screenshots, and logging keystrokes by prompting the user to log in again.
SQL injection attack
This type of attack is seen within a database-driven website. The attacker will input a SQL command into a database input to run the predefined SQL command. If successful, the SQL injection can modify or exploit data on the database, and even give a command to the operating system. To reduce the likelihood of this type of attack, ensure your access to the database is updated regularly, sanitize your variables/inputs, and configure baselines for the database management systems.
Malware attack
Malware is a fancy way of saying malicious software. There are many different types of malware, which can be Trojans, stealth viruses, logic bombs, worms, droppers, and ransomware. We encourage you to conduct your own research to learn more about malware.
Malware is the standard type of infection you will likely see on a system. It's essential to have a basic understanding of each type of malware and how it can infect a system. The best approach to limit possible infection of malware is by keeping operating systems patched, VPN enabled, and using an updated browser. Most successful attacks can be avoided with proper system patching and software updates.
Eavesdropping attack
An eavesdropping attack is also known as a snooping or sniffing attack. Unlike the Man-in-the-Middle attack, an eavesdropping attacker listens either passively or actively to the user's network. They listen to the network traffic to find data such as credit card info or passwords. The best prevention against this type of attack is MFA and overall system encryption.
Rogue software attack
Attackers have been using rogue software attacks since 2008. The attacker will lure its victims by making them think they have a virus on their machine. Once they have struck panic in the victim, they will convince them to pay for a removal tool that is masquerading as legitimate software.
The vector for this type of attack can be when a user goes to a website and suddenly sees a popup saying, "Your system has been infected with malware, act now, click here to conduct a virus scan." Once the victim clicks, depending on the victims antivirus, the download begins. Another name for the malware used in this type of an attack is called scareware because the purpose is to scare the victim into reacting quickly.
The following diagram will assist you with remembering the attack names:
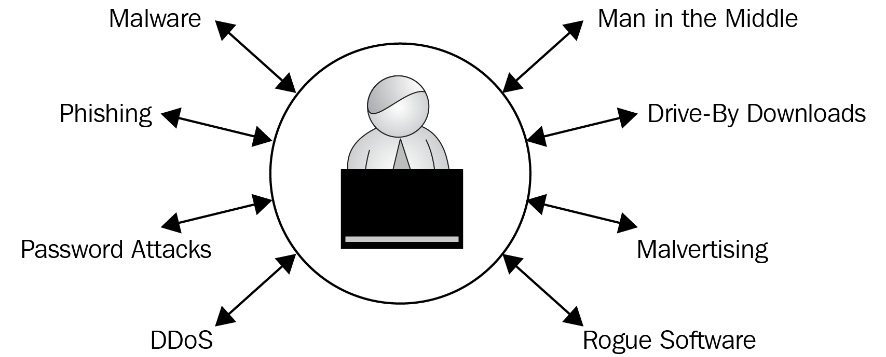
Figure 1.3 – Types of cyber attacks
As we conclude this section, we encourage you to take the time to research and learn more about cyberattacks.
In the next section, we will discuss cyber careers. I will provide you some pros and cons to prepare you for entering this field.

























































