Privacy in cyberspace
Every country has its own jurisdiction system and laws. Typically, respective laws are applicable within the country. Even within federal governments, sometimes different states will have different laws and acts. The reason is if any incident takes place, the law enforcement bodies of respective areas or state stake the required actions.
Cyberspace works completely differently, though, as in most incidents, the perpetrator connects remotely over the internet with the target. Most of the time, the attacker is located in a different state or country than the target. The internet is an unregulated space and no one has direct ownership. Every time we access the internet, we need to remember that we are connected to an unregulated space and we need to look after our own security as the internet cannot be completely governed due to its architecture and very nature.
Whenever we are connected to cyberspace using any type of device, we are risking breaches of our privacy. In reality, we compromise our privacy in different layers. When we connect to the internet, we use different kinds of devices. It can be a mobile device, laptop, desktop, and so on. The first layer is the device that we connect to the internet as it stores lots of information. Then, we have the application that we use to access and surf the internet, typically a browser. The browser also keeps lots of information. Then, the device must be connected to the internet using some sort of media; this can be a wired or wireless connection. Whatever connection we use, there is a possibility that the network is collecting information on us. This is known as network capturing.
The next layer is the devices to which the network is connected. This includes Wi-Fi routers, switches, and firewalls that are connected to the network, and they also collect information. The network connection is then connected to the Internet Service Provider (ISP), which collects different kinds of information about the connection. If you are accessing a particular website, the host web server collects information about the connection. This information includes the timestamp, your public IP address, the type of browser being used, and the operating system.
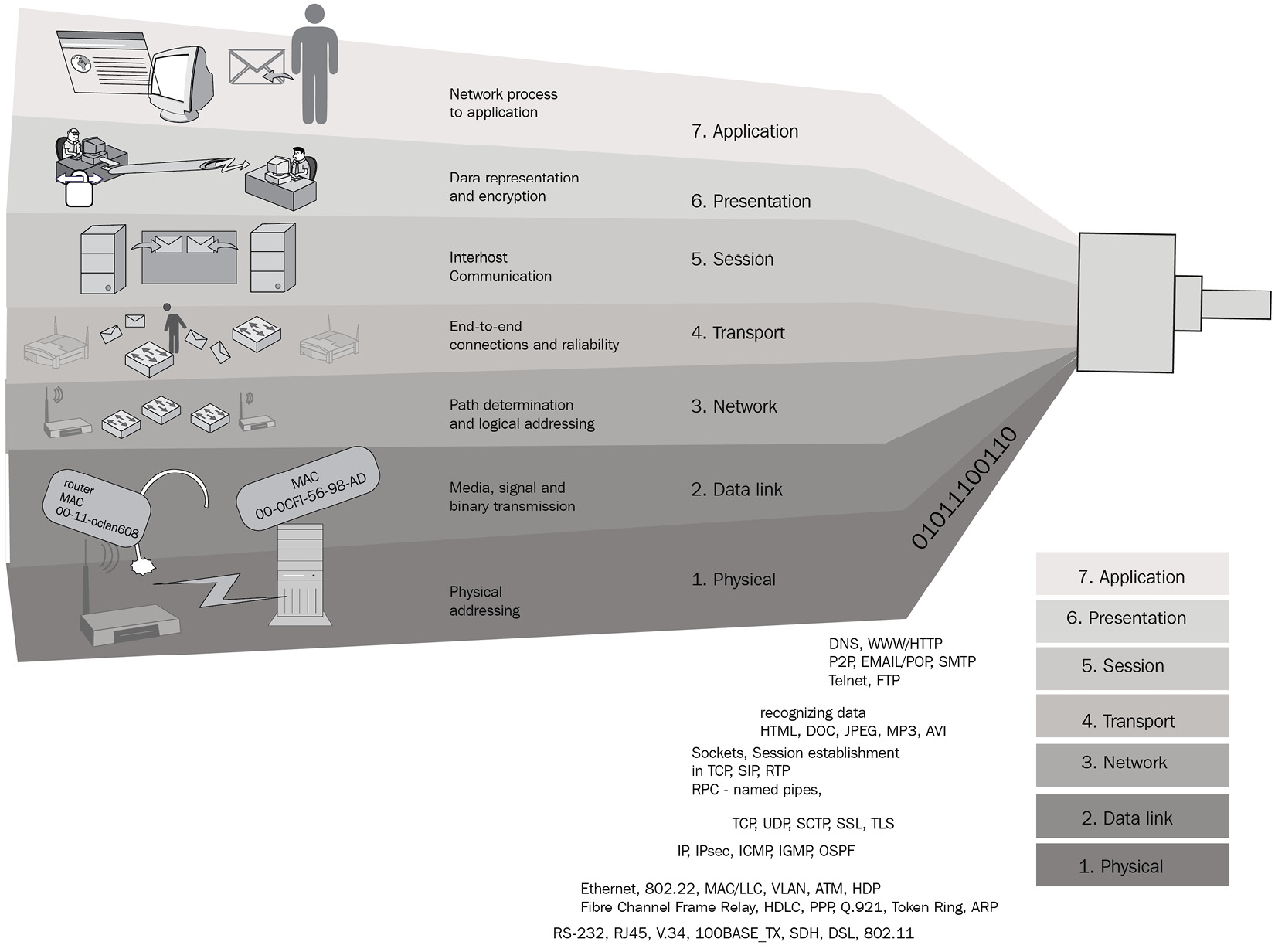
Figure 1.9 – Different layers where different types of information pass through
When you look at these layers, even if an attacker is not involved, there are multiple layers where information is being collected about your connection. As we discussed earlier, this includes personal and sensitive information about you.
This gives an understanding of the different layers between the web application and the device. Importantly, if any of the layers are compromised by attackers, it will become more crucial as then attackers have control and access to these layers. They can even intercept communications and acquire credentials if the protocols of the communication used are weak.
When you perform any activity on the internet, or within the network using an application, data goes through these layers when communicating with other entities. As an example, when you draft an email using an email client such as Microsoft Outlook, data is created in the application layer and all the other layers are responsible for different tasks:
- Layer 7 – application: This layer is where the users are directly interacting with the device using an application such as a browser.
- Layer 6 – presentation: This layer is preparing source and destination devices to communicate with each other. Encryption and decryption take place in this layer.
- Layer 5 – session: This layer helps to establish, manage, and terminate the connection between the source and destination devices. Communication channels are referred to as sessions.
- Layer 4 – transport: Transporting data from the source to the destination takes place in this layer. If the dataset is large, then data will be broken into pieces in this layer.
- Layer 3 – network: This layer is responsible for mapping the best paths for data traversal between devices and delivering messages through nodes or routers.
- Layer 2 – data link: This layer is responsible for switching connected devices.
- Layer 1 – physical: This layer represents the physical connectivity, including cables and other mediums responsible for sending data as frames.
When thinking of privacy, you need to concentrate on all the layers, including the device, application, network, communication, and web servers. For example, if you are using a shared device and save passwords on the web browser, your private information can be stolen easily, as there are many free tools out there to make life more easy.
If you access https://www.nirsoft.net/utils/web_browser_password.html, you can download web browser password viewers, which can retrieve stored passwords easily.
The same site also provides you with a range of free tools that can be used with the Graphical User Interface (GUI) or scripts (command-line tools) to automate the process.

























































