Upgrading the firewall
In this section, you will learn how to upgrade your firewall and what steps need to be taken to ensure a smooth process. We will review important information to keep in mind when preparing your maintenance window and providing for a contingency plan. In-depth upgrade procedures are provided in Chapter 8, Upgrading Firewalls and Panorama.
Understanding the partitions
Before we start the upgrade procedure, there’s an important bit of information you need to know. Like most Linux systems, the hard disk has been partitioned into specific segments. These segments serve a specific purpose.
A few important ones are as follows:
/is the root partition, which is where the operating system is installed/opt/pancfgis where the configuration files and dynamic update files are kept/opt/panrepois the repository for downloaded operating system (PAN-OS) images/opt/panlogsis the partition wherelogdatabaseis stored
The disk space usage can be viewed with the following command:
admin@PA-220> show system disk-space
Filesystem Size Used Avail Use% Mounted on
/dev/root 3.8G 1.7G 1.9G 48% /
none 2.0G 60K 2.0G 1% /dev
/dev/mmcblk0p5 12G 3.3G 7.5G 31% /opt/pancfg
/dev/mmcblk0p6 3.8G 2.2G 1.5G 59% /opt/panrepo
tmpfs 2.0G 247M 1.8G 13% /dev/shm
cgroup_root 2.0G 0 2.0G 0% /cgroup
/dev/mmcblk0p8 4.6G 3.5G 942M 79% /opt/panlogs
/dev/loop0 111M 5.6M 100M 6% /opt/panlogs/wildfire/tmpfile
tmpfs 12M 0 12M 0% /opt/pancfg/mgmt/lcaas/ssl/private
None
The cool thing about the / root partition is that it is actually one of two sysroot partitions. The system has actually been partitioned with two operating system-specific partitions, of which just one is mounted at a time. The upgrade procedure actually installs the new PAN-OS onto the inactive partition.
This allows inline upgrades without interrupting the active partition. Once the new operating system has been installed, the GRUB bootloader is configured to load the other sysroot partition at the next boot, causing the new PAN-OS to become active:
admin@PA-220> debug swm status
Partition State Version
--------------------------------------------
sysroot0 REVERTABLE 10.0.3
sysroot1 RUNNING-ACTIVE 10.0.9
maint EMPTY None
This mechanism also allows a smooth rollback in case an upgrade fails and it is decided you need to go back to the previous situation. You can trigger the > debug swm revert debug command to tell the bootloader to switch the toggle again to the previous sysroot partition and reboot the system via > request restart system, and after the device has rebooted, you are back on the previous PAN-OS with the pre-upgrade configuration loaded.
Upgrade considerations
When upgrading, you will need to map out where you are, where you need to go, and how you need to get there. Finding where you are can be achieved by looking at the dashboard’s General Information section and looking for the software version. Deciding where you need to go may require some research and consideration:
- Which features are required? Are there new features in a release you need, or are you running smoothly with the features you have?
- Is the code train “mature”? Is a new major release brand new, and do the new features weigh up against the risk of being an early adopter?
- Are there outstanding advisories that trump the required features? Was a critical vulnerability found that has not been addressed in the version you plan to go to?
- When is an upgrade required and when is it optional? Is there a direct need to upgrade due to a vulnerability or a bug, or are there features in a newer release that will be helpful?
These questions will help you determine which upgrades need to take place immediately and which ones can be planned ahead of time, possibly with a more relaxed testing process before deploying to the production environment or even postponed until a more mature maintenance release version is available.
Which features are required?
Determining which features are contained in each PAN-OS version requires the most research. You can open https://docs.paloaltonetworks.com and search Feature Guide, which will return all the new feature guides for the major PAN-OS versions.
Is the code train “mature”?
Maturity can be estimated by looking at the maintenance release version. All PAN-OS versions are made up of three numbers—PAN-OS X.Y.Z (for example, 9.0.5):
- X is the number of the major software release
- Y is the number of the feature version release
- Z is the number of the maintenance release
X will change when a new major software version is released containing new functionality and usually containing some changes in its expected behavior and possibly a new look and feel.
Each new software release is usually followed by a new feature version around 6 to 9 months after its release, mostly containing some new features. Maintenance release versions are released for all code trains anywhere between 5 and 9 weeks and mostly contain bug fixes.
There will occasionally be PAN-OS version names that end in -hx, which denotes a hotfix. This is a maintenance release that was published ahead of schedule and usually only contains one or a few critical hotfixes (for example, 9.0.2-h1).
A code train will reach a reliable maturity around the x.x.4 or x.x.5 maintenance release version when it is somewhat safe to assume most critical bugs have been found and addressed.
Check the release notes for any known issues so that you can appropriately prepare if there are any caveats: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-release-notes.html.
Are there outstanding advisories that trump the required features?
Advisories regarding which maintenance release versions to choose or avoid can be found at https://securityadvisories.paloaltonetworks.com/ and https://live.paloaltonetworks.com/t5/Customer-Resources/.
When is an upgrade required and when is it optional?
Each major version has a base image, usually the x.x.0 version, which contains all the vital parts of the PAN-OS image.
This allows the following maintenance versions to be smaller in size, containing only critical updates. The base image needs to be downloaded onto the system before a maintenance version can be installed. It is not required for the base image to be installed in order to be able to install the maintenance version when upgrading from a lower major version. It is also not required to install any intermediate maintenance versions unless the release notes explicitly mention that there is an issue that requires a step in between.
Say, for example, that your firewall is currently on PAN-OS 9.1.4 and you need to get to PAN-OS 10.0.5. You can download a PAN-OS 10.0.0 base image, followed by PAN-OS 10.0.5, and then directly install and reboot PAN-OS 10.0.5. Your system will be directly upgraded from 9.1.4 to 10.0.5.
If your firewall is currently on PAN-OS 9.0.10 and you want to go to PAN-OS 10.0.5, you do need to download, install, and reboot to a PAN-OS 9.1.0 base image before you can install PAN-OS 10.0.5.
Important note
In the latter case, it is recommended, but not mandatory, to download and install the preferred maintenance release (see the previous Customer Resources URL: https://live.paloaltonetworks.com/t5/Customer-Resources/) in the PAN-OS 9.1 code train to prevent running into bugs that could halt the upgrade process.
You will now have a good understanding of when and why you would need to upgrade and how to decide which version you need to upgrade to. In the following section, we’ll briefly go over the upgrade process via different methods; see Chapter 8, Upgrading Firewalls and Panorama, for a more thorough upgrade process.
Upgrading via the CLI
Via the CLI, commands can be quickly executed to perform tasks. When upgrading via the CLI you first need to retrieve the available software images that can be installed on your system. You won’t be able to download any images before the list is retrieved:
admin@PA-220> request system software check
Version Size Released on Downloaded
---------------------------------------------------------
10.1.4 353MB 2021/12/22 11:51:17 no
10.1.3 298MB 2021/10/26 18:51:50 yes
10.1.2 297MB 2021/08/16 14:51:59 no
10.1.1 280MB 2021/07/21 09:33:49 no
10.1.0 540MB 2021/06/02 08:15:33 yes
10.0.8 363MB 2021/10/21 22:42:18 no
10.0.8-h8 359MB 2021/12/20 12:23:36 no
Next, you can download the desired PAN-OS version:
admin@PA-220> request system software download version 10.1.4
Download job enqueued with jobid 31
You can track the download status with the following command:
admin@PA-220> show jobs id 31
Enqueued Dequeued ID Type Status Result Completed
--------------------------------------------------------------
2021/12/3117 23:24:15 23:24:15 31 Downld FIN OK 23:25:31
Warnings:
Details:Successfully downloaded
Preloading into software manager
Successfully loaded into software manager
When the software is successfully downloaded, you can commence installing it onto the system. You will be prompted that a reboot is required to complete the installation and to confirm whether you are sure that you want to continue. Type Y to proceed with the installation:
admin@PA-220> request system software install version 10.1.4
Executing this command will install a new version of software. It will not take effect until system is restarted. Do you want to continue? (y or n)
Software install job enqueued with jobid 32. Run 'show jobs id 32' to monitor its status. Please reboot the device after the installation is done.
You can track the installation progress through the show jobs command:
admin@PA-220> show jobs id 32
Enqueued Dequeued ID Type Status Result Completed
--------------------------------------------------------------
2021/12/3117 23:35:28 23:35:28 32 SWInstall FIN OK 23:38:59
Warnings:
Details:Software installation successfully completed. Please reboot to switch to the new version.
To complete the installation, reboot the firewall. Type Y into the dialog if you are certain that you want to go ahead with the reboot. Rebooting will cause all sessions to be interrupted and no new sessions to be accepted until the firewall has completed the autocommit job:
admin@PA-200> request restart system
Executing this command will disconnect the current session. Do you want to continue? (y or n)
The autocommit job runs right after a reboot and serves to load the configuration onto the data plane. After a software upgrade, this process can take a while:
admin@PA-200> show jobs all
Enqueued Dequeued ID Type Status Result Completed
--------------------------------------------------------------
2021/12/31 23:44:27 1523:44:27 1 AutoCom FIN OK 23:44:36
If you prefer to upgrade the firewall via the web interface, follow the procedure outlined in the next section.
Upgrading via the web interface
Software images can be downloaded and installed from the Device | Software menu. The first time you access this page, you will be presented with an error message because no repository has been loaded yet:
Figure 2.21: Error message on the first visit to the software page
You can ignore this warning; click Close and then click Check Now. Once the repository has loaded, you will see all the available software images:
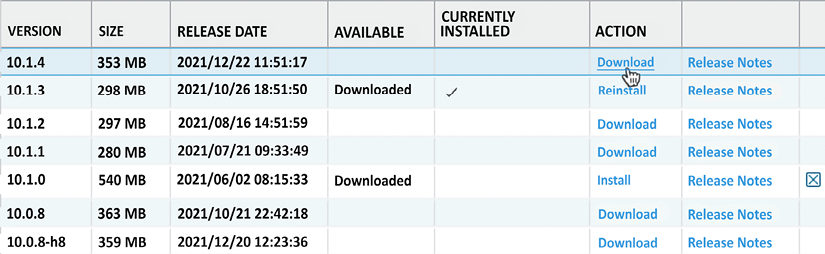
Figure 2.22: Software management page
Click the Download link next to the PAN-OS version you want to upgrade to and wait for the download dialog to complete.
Once the new PAN-OS package is downloaded, it will be listed as such on the Software page, as shown. Click the Install link next to the image to start the installation:
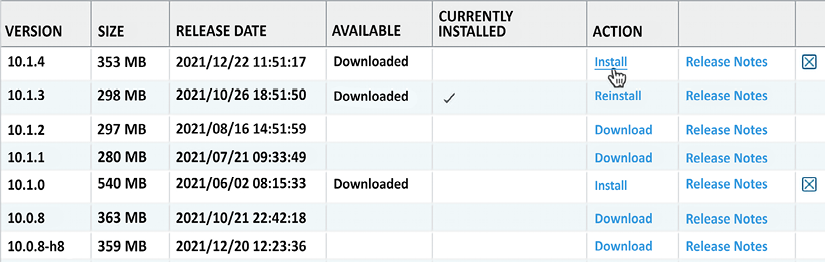
Figure 2.23: Image downloaded and ready to install
At the end of the installation, you will be prompted to reboot. You can skip the reboot if you want to postpone the actual upgrade to a later time. Otherwise, click Yes, as shown:
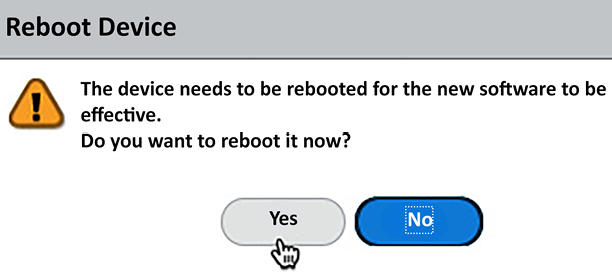
Figure 2.24: Post-installation reboot dialog
Below is an upgrade cheat sheet that will help you prepare and plan your upgrade.
Upgrade cheat sheet
The next steps outline a solid methodology to get to a stable PAN-OS version before placing the firewall in production:
- Go to https://live.paloaltonetworks.com/t5/Customer-Resources/ for release recommendations.
- In Device | Software, click on Check Now to load the latest list of available PAN-OS images.
- Download and install the recommended image of your current release.
- When the installation completes, a dialog window will ask if you want to reboot the device. Click Yes.
- Wait for the unit to boot up again and download the base image for the next major version.
- Download and install the recommended maintenance release for the next major version.
- When the dialog asks you to reboot the device, click Yes.
- Repeat steps
5through7until you’re on the version you need to reach.
Remember that for an HA cluster or panorama environment, you need to do the following:
- Disable preemption in the High Availability configuration before you start, and re-enable it after the upgrade is completed on both members
- Check both members for functionality before you start. The upgraded device will become non-functional until the lowest member has caught up (the cluster favors the lowest software member)
- Upgrade the panorama centralized management first
You have now made sure the firewall is fully set up for success by ensuring the content packages are automatically downloaded and installed, and the appropriate PAN-OS firmware has been installed. Next we will take a look at ensuring the management interface configuration is set up securely.
































































