Networking concepts on-premises and in the cloud
Let’s dive into the building blocks of networks. Here, we will cover various components of networks that range from software, hardware, and standards. This chapter will not go into detail on networking because networking is such a broad topic, and some books just focus on networking. We will cover the necessities to ensure that you understand networking in the context of ethical hacking.
When you start to communicate on a network, the information that you are sending needs to be translated into something that computers can understand. Yes, ultimately, it’s all 0s and 1s, but let’s focus on the various pieces before that. We will begin by looking at packets.
Packets
When information is transmitted across a network or the internet, it needs to be formed into a unit that can be carried across a network. This is called a packet, or a network packet. This network packet contains information that ultimately gets routed to destinations on the internet. Think of a packet as an envelope that you would send using the postal service. You would put something inside that envelope, provide a return and destination address, and the postal service would sort and route it to the destination.
In terms of networking, the packet would contain a similar composition.
The contents inside the packet would be your data, the return address would be your Source MAC address and IP address, and the destination address would be your destination MAC and IP address. Now, there will be some routing involved, all of which is handled by hardware such as routers, which will make modifications to the different MAC and IP addresses.
MAC address
All devices that communicate on a network will have a networking interface card (NIC). This can be either an Ethernet or wireless adapter. Every single NIC has a unique identifier, which is called a media access control (MAC) address. This address aims to uniquely identify your machine on the network. MAC addresses are used by routers or switches (OSI Layer 2) to send packets to a specific destination. MAC addresses consist of 48-bit numbers that are written in hexadecimal format; for example, 00:00:5e:00:53:af. Every MAC address will have an organizationally unique identifier (OUI), which is the first 24 bits of the MAC address. The remaining 24 bits are used to uniquely identify the device. Looking at our example MAC address, if we had to break it down into the OUI and the device identifier, it would look like Figure 1.1:
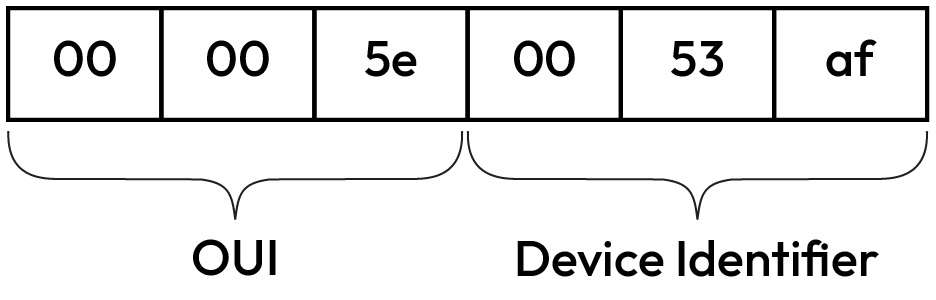
Figure 1.1 – Breakdown of a MAC address
IP addresses
Internet Protocol (IP) addresses enable data to be transferred across networks (OSI Layer 3). They are crucial to networking because they contain information that enables devices to communicate. Such information may be things such as location information, which enable devices to communicate with each other in dissimilar environments.
Tip
If you are looking for a refresher on the OSI model, please take a look at this link: https://www.networkworld.com/article/3239677/the-osi-model-explained-and-how-to-easily-remember-its-7-layers.html.
The makeup of an IP address contains numerals that are separated by a period. For example, 192.168.1.1 is an example of an IP address. Within an IPv4 network, the numbers can vary from 0 to 255 for each piece of an IP address, which means that an IP address can range from 0.0.0.0 to 255.255.255.255. Some of the addresses within that range are reserved for various purposes; you can find more information about these reservations in the following note. In an Internet Protocol version 6 (IPv6) network, an IPv6 address is a 128-bit alphanumeric value. This 128-bit value is arranged into eight groups of 16 bits. Each group is separated by a colon. IPv6 is the successor to IPv4, a previous addressing infrastructure with limitations that IPv6 was created to remedy. In comparison to IPv4, IPv6 has significantly more address space. Consider the following example of an IPv6 address: 684D:1111:222:3333:4444:5555:6:77. Here, you will notice how it differs from IPv4. Due to its size, it allows a significantly larger IP address space.
Note
IP addresses are assigned by the Internet Assigned Numbers Authority (IANA).
IP addresses are split into two categories: public and private. Private consists of IP address ranges that are not routable on the internet. These are generally what you would have on your local network, such as your Wi-Fi network and so forth. Public IP addresses are routable on the internet. Your internet provider would assign you a public IP address on your home network for you to access the internet. You can easily check what your public IP address is by searching for what's my IP on Google Search.
Now that we have the very basics of networking covered, let’s move on to cloud computing.
Cloud computing
Today, the term cloud computing is not unheard of. Many people working in the IT industry know about cloud computing and probably make use of it daily. When you work on email services, social media, online gaming, and so forth, this is all cloud computing in action. Major software companies such as Google, Microsoft, and Amazon offer cloud computing and a range of cloud services.
Note
There are a lot of other providers who offer cloud services, apart from those that I have mentioned. Performing a quick internet search for Cloud Service Providers will give you a comprehensive list.
In terms of cloud computing, various types of cloud setups exist. The most common ones today are the public cloud, private cloud, and hybrid cloud. There are differences between them, as described next.
Public cloud
A public cloud is administered predominantly by a third party. These cloud environments provide easy access to the public (hence the term public cloud) via the internet. Resources that are available here entail storage, compute, applications, and more. The key here is that anyone who wants to use these services can make use of them. Public clouds are cost-effective, relieving you from the expensive costs of having to purchase hardware, manage it, and so forth. With the public cloud, anyone with an internet connection can make use of the services. There are several security concerns with public clouds, especially when it comes to data residency and who has access to the data. However, many public cloud providers provide solutions to address this.
Private cloud
Private clouds offer services either over the internet or via a private internal connection. These are limited to selected users and not the public. You may find the terms corporate cloud or internal cloud often used interchangeably with public cloud. This cloud setup aims to provide the benefits of a public cloud with additional controls and, to an extent, additional customization where possible. Private clouds are said to provide a higher level of security concerning data confidentiality – it limits access to third parties. The drawback of a private cloud is that it requires staff to maintain it.
Hybrid cloud
A hybrid cloud combines both public and private cloud solutions. It enables data to be shared between them. This cloud aims to enable organizations to scale where needed, but also provide limited access to restricted data where possible.
If I had to describe cloud computing in simple terms, it is the delivery of computing services that make use of servers, databases, networking, software, storage, and more. All of this is delivered across the internet, referred to as the public cloud. Cloud computing aims to offer faster innovation, flexibility when it comes to resources, and scalability, enabling you to up or downscale your resources with ease. Cloud computing offers various operating models:
- Infrastructure-as-a-Service (IaaS)
- Platform-as-a-Service (PaaS)
- Software-as-a-Service (SaaS)
Cloud computing providers often have a shared responsibility model that describes the responsibility and security tasks that are handled by the provider and the customer. These responsibilities and tasks change as you use different operating models.
The following figure is a sample of Microsoft’s shared responsibility model. Notice how the responsibilities change between SaaS to on-premises:

Figure 1.2 – Microsoft shared responsibility model (Source: https://learn.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility)
All cloud providers will provide some type of responsibility matrix – for example, Amazon Web Services has theirs (https://aws.amazon.com/compliance/shared-responsibility-model/), and the same goes for Google Cloud (https://cloud.google.com/architecture/framework/security/shared-responsibility-shared-fate).
Let’s cover these briefly so that you understand what each model offers. It is important to have a good understanding of these as you prepare for an ethical hack because it gives you insight into who handles the security of the target components such as the operating system and application updates and so forth.
Infrastructure-as-a-Service
IaaS is a standardized method of obtaining computing resources on demand. These services are delivered through the internet via a cloud provider. These services include storage facilities, networks, computing power, and virtual private servers. These are invoiced on a pay-as-you-go basis, which means you are billed based on different criteria, such as how much storage you use or how much processing power you utilize over a set period. Customers do not need to maintain infrastructure under this service model; instead, the provider is responsible for ensuring the contractual quantity of resources and availability.
Some of the advantages of IaaS include the following:
- Very flexible cloud computing model
- Ability to easily automate the deployment of services such as storage, processing power, network, and so forth
- Highly scalable
- Resources can be purchased as needed
As with everything in the computing world, there are security concerns. With IaaS, the following can be seen as security concerns:
- Security threats to system vulnerabilities
- Legacy operating systems in the cloud
- Multi-tenant security, whereby you rely on the vendor to ensure the separation of customer environments
Some examples of IaaS include compute services purchased from cloud vendors. Common use cases of IaaS can be found in large organizations that want to purchase and pay for what they consume, or organizations that are rapidly expanding and need the scalability of hardware.
Software-as-a-Service
SaaS aims to provide web-based solutions. These solutions are controlled by the supplier, which is great as it relieves the pressure of maintaining the software, infrastructure, security of the application, and so forth. SaaS services are often billed by the amount of data stored, number of transactions, number of users and usage, and so on.
The advantages of SaaS include the following:
- Reduce overhead in time and money spent on installing, managing, and upgrading software
- Providers upgrade the solutions, thereby putting you on the latest solution all the time
- Baked-in best practices enable you to test the solution with a good security posture from the get-go
The limitations that exist with SaaS can include the following:
- Data security in terms of large volumes of data exchanged by backend data centers. These transfer business-sensitive data that, if not properly secured, can lead to exposure.
- Lack of control since this is handled by the provider or third parties.
- Reliance on the vendor’s security controls to ensure that the application is secured.
Typical examples of SaaS solutions include Dropbox, Cisco Webex, and Salesforce. The use cases of SaaS can be seen in applications that need both web and mobile access, collaboration solutions that exist on the internet, and more.
Platform-as-a-Service
PaaS provides a bridge between IaaS and SaaS services. PaaS aims to provide customers with a platform that is cloud-based that can be used to build and distribute applications without the need to install integrated development environments (IDEs). Users can also typically specify whatever features they want to be included in their subscription.
There are advantages to PaaS, some of which are as follows:
- Cost-effective deployment of applications
- Easy of deployment with high scalability
- Apps can be customized without the need to maintain the underlying software
Concerning the advantages, there are also limitations and concerns. Some of these are as follows:
- Integrations with outside data centers or on-premises increase, increasing the possible attack surface.
- Third-party data residency poses security risks as to who might be able to view that data. A lack of security controls on the data could be possible.
- Integrations with existing applications could become problematic.
Typical examples of PaaS in the cloud are Heroku, OpenShift, and App Engine. PaaS is beneficial when it comes to streamlining workflows that are leveraged by multiple developers. It also provides speed and flexibility to these workflows.
This section aimed to give you an overview of cloud solutions, the different operating models, and how the shared responsibility of the cloud works. As you craft your ethical hack methodology, you should take this into account in the event your target is making use of cloud services.
























































