Thanks to various technology companies, we can break down communication barriers between people who speak different native languages. We can simply install an app on our smartphone such as Google Translate and translate a foreign language into our own and vice versa.
For a device to communicate with another on a network, it requires a set of protocols or a protocol suite. A protocol suite is a common format that devices can use by following a set of rules for exchanging messages with other devices on a network. A protocol suite enables devices to speak a common, universal language that allows all networking devices to understand each other.
Years ago, computer manufacturers made their own protocol suites, which, in most instances, allowed only same-vendor devices to communicate and exchange data on a network. Some of these protocol suites were AppleTalk and Novel Netware (IPX/SPX), which were proprietary to the vendor and not suitable for consumers on a large scale.
Then came the Open Systems Interconnection (OSI) reference model and the Transmission Control Protocol/Internet Protocol (TCP/IP) suite. In the following subsections, we will further discuss and compare both the OSI model and TCP/IP protocol suite.
OSI reference model
The OSI reference model is a seven (7) layer model that was developed by the International Organization for Standardization (ISO) in the 1970s. It was intended to be a fully operational protocol suite to allow all devices on a network to intercommunicate using a mutual language. However, it was never actually implemented in any systems.
You may be wondering, if it's not implemented in any operating systems and devices, why is it important we learn about the OSI reference model? Each layer of the OSI model has a unique functionality associated with a computer network. This allows network engineers to better understand what happens on each layer when performing troubleshooting tasks.
During the development of the OSI model, it was noted the model consisted of seven layers. These are as follows:
- Layer 7: Application
- Layer 6: Presentation
- Layer 5: Session
- Layer 4: Transport
- Layer 3: Network
- Layer 2: Data link
- Layer 1: Physical
Why are there so many layers? Each layer of the OSI model has a particular responsibility for ensuring a device is able to successfully exchange messages with other devices on a network. In the following sections, we are going to learn the essentials of each layer and how they help us understand network operations. This enables us to better identify and troubleshoot network-related issues in the industry.
Tip
We can take the first letter of each layer of the OSI model to create an easy-to-remember phrase: All People Seem To Need Data Processing.
As an example, when a device such as a computer wants to send a message (data) to another device either on a local or remote network, the data has to flow downward in the OSI model, passing through each layer. During this process, a specific set of rules, encoding, and formatting is applied. This is known as encapsulation. Whenever a recipient is processing a message, it goes upward, passing each layer, and parts of the message are stripped away. This is known as de-encapsulation.
The following diagram shows the typical flow of a message through the OSI model when one device is sending a message and another device is accepting and processing an incoming message:
Figure 1.4 – Visual representation of traffic flowing through the OSI model
In the field of networking, a device such as a computer creates a Protocol Data Unit (PDU), sometimes referred to as a datagram. This is the raw data to be sent across a network to another device. At each layer of the OSI model, the PDU has a different name. These names are used to reference the characteristics of the PDU at a particular layer. In your exam, it's important to use this terminology. The following diagram shows a table containing the layers of the OSI model and the name of the PDU at each layer:
Figure 1.5 – PDUs at each layer of the OSI model
To get a better understanding about each layer of the OSI model and the characteristics of PDUs as they are passed between layers, we will discuss the role and function of each layer in the following sections. Let's take a closer look.
Layer 7 – Application layer
The application layer (Layer 7) is the closest layer to the user within the protocol suite. It provides an interface for communication between the applications running in a local system and the underlying network protocols. To further explain, imagine you would like to get a bit more information on the Cisco Certified Network Associate (CCNA) certification. In today's world, internet access is readily available to us, either on mobile data plans that utilize 4G and LTE technologies or internet cafes and coffee shops with free internet access via their Wi-Fi network. Whichever method we use to access the internet, we always need an important application: a web browser to view web pages in a graphical interface, which helps us navigate the internet easily.
Let's continue with our analogy. One action you may want to perform is to visit Cisco's website at www.cisco.com to research the examination objectives and better prepare yourself for the certification.
Opening your favorite web browser, you enter the URL www.cisco.com and hit Enter. Within a couple of seconds, the Cisco website is displayed within the browser's interface. Looking closely at the address bar in the browser, we can see that the Hypertext Transfer Protocol Secure (HTTPS) protocol has been involved by the web browser, as shown in the following image:
Figure 1.6 – HTTPS protocol used in web browser
Keep in mind that the web browser is simply an application running on our computer or smart device that allows us, the user, to use an application layer protocol such as HTTPS to exchange messages (encoded in web languages) between our computer and a web server. This makes the HTTPS protocol one of many application layer protocols.
The following are some commonly known application layer protocols:
- File Transfer Protocol (FTP)
- Simple Mail Transfer Protocol (SMTP)
- Domain Name System (DNS)
- Dynamic Host Configuration Protocol (DHCP)
- HyperText Transfer Protocol (HTTP)
In reference to the OSI model, the web browser (application) creates the raw HTTPS message. At this point, the PDU is known as data. Data has no additional encoding or formatting as it is simply the raw (bare) message the application has generated. However, in this state, the PDU can only be recognized and interpreted by another similar application that understands HTTP/S.
When the application layer has finished its job, it passes the PDU onto the lower layer, known as the presentation layer.
Layer 6 – Presentation layer
A very important factor in communication is how content is presented. We must always try to ensure the format in which the message is written or spoken can be interpreted by the recipient very clearly. Imagine an ambassador who only speaks English is traveling to a foreign country on diplomatic business where the foreign nationals do not speak English. This will be a challenge for the ambassador; it can negatively affect some of the communication that they have with the locals during their visit. Having a dedicated person as a translator will assist the ambassador in communicating clearly with the foreign nationals.
We can apply this analogy to a network. There are many protocols that exist both inside and outside of a computer system; some are on the network itself, while others are on the operating systems of a server or desktop computer. Furthermore, as previously mentioned, each layer of the OSI reference model has its own set of protocols, which aid in the transmission of data between devices.
When an application layer protocol such as HTTPS sends the raw data to the network, it passes through the presentation layer (Layer 6), which has to perform some tasks before sending it to the lower layers. The presentation layer is responsible for the following functions:
- Data formatting
- Data compression
- Data encryption and decryption
Most importantly, data formatting ensures the raw data is presented or formatted into a compatible format for both the lower layers and the recipient's device(s) to understand. It's a bit like creating a universal language on a digital network.
Let's look at a simple analogy to further explain this concept. Imagine having to write a letter to a friend who resides in another country. After writing your letter, you securely enclose it within an envelope and insert the correspondence destination address before dropping it off to the local mail courier. Since the letter is intended for international shipping, the local courier will attach an international shipping label containing a universal format for the addressing information. This means the local courier company may need to pass the letter onto another courier until it reaches the intended destination. During this process, each courier will be able to read and interpret the information printed on the universal shipping label because its format is standardized. The same applies to messages passing to the lower layers of the OSI model, hence the importance of the presentation layer.
Another function of the presentation layer is compressing data before it is placed on the network and decompressing it on the recipient's device. Lastly, the presentation layer encrypts data before transporting it between the sender and receiver over a network. On the receiving device, the presentation layer is responsible for the decryption of the encrypted message.
At the presentation layer, the PDU is still known as data. Next, the PDU is passed on to the session layer.
Layer 5 – Session layer
The session layer (Layer 5) has a simple responsibility. At this layer, there are three main functions that work together with a device to ensure datagrams (messages) can be exchanged across a network. These are as follows:
- Create or build a session between a sender and receiver.
- Maintain the established session during the transmission of messages between the sender and receiver devices.
- Terminate a session when both parties indicate they no longer want to communicate with each other.
Keep in mind that, at the session layer, the PDU maintains the same name as the upper layers: data.
Layer 4 – Transport layer
The transport layer (Layer 4) is responsible for moving datagrams between the upper layers (application layer) onto the network itself. At the transport layer, the PDU has a new name, Segment.
At the application layer, there are many applications (programs) that generate network traffic, such as HTTP or SMTP, at any time. When each application layer protocol sends their datagram to the network, the transport layer has the responsibility of tracking these conversations as they occur.
Whenever a device wants to send a message across a network, the transport layer prepares the datagram (message) and separates it into manageable pieces for delivery. This is due to the fact that networking devices such as switches and routers, together with client machines such as desktop and server operating systems, have limitations regarding the amount of data that can be put in an IP packet. Therefore, the transport layer handles how to segment and reassemble these messages between the sender and the receiver.
As mentioned previously, there are many protocols at the application layer that handle data in different ways. Web traffic uses HTTP and HTTPS, which is formatted differently from email traffic, which uses the SMTP application protocol. Each protocol is designed to interpret its own type of traffic just fine, but if foreign traffic enters its application, it would be malformed and foreign in nature and therefore be discarded. One of the most important roles of a transport layer is to ensure data is passed to the corresponding applications. In other words, if a web browser is sending HTTP(S) traffic to a device on a network, the recipient application protocol on the destination device is expected to be running HTTP or HTTPS, such as a web server.
The transport layer ensures each datagram is sent to its corresponding application or application layer protocol by assigning a unique port number to the PDU, therefore creating a transport layer header. This process is known as encapsulation.
To get a better understanding of this process, let's use a simple analogy of a commercial tower whose tenants are various companies sharing the same physical infrastructure: the building. Typically, the main public area is the lobby, displaying a directory listing of each company and their floor number.
Let's think of the building as an operating system (OS). According to RFC 6335, there are 65,535 logical network ports within an OS. These ports are categorized as follows:
Figure 1.7 – Network port number ranges
The well-known ports are those that are commonly used by application layer protocols, which are as follows:
- File Transfer Protocol:
20, 21
- Secure Shell (SSH), Secure Copy (SCP):
22
- Telnet:
23
- SMTP:
25
- DNS:
53
- DHCP:
68, 69
- HTTP:
80
- POP:
110
- IMAP:
143
- HTTPS:
443
Each application layer protocol/service uses a unique port that they send and receive their traffic type to and from. For example, all HTTP traffic will be sent to a device running a web server application (IIS, Apache, or Nginx) with open port 80. For HTTPS traffic to enter the web server, port 443 is the default port that must be open.
Registered ports are used by software and other vendors who want to use a specific port only for their application. These dynamic ports are used temporarily when a device is sending traffic and are sometimes referred to as ephemeral ports. For example, if a PC wants to send traffic to a web server, we know the web server will have port 80 and/or 443 open by default. However, the PC must use a source port. This means a dynamically generated port (ephemeral) between 49152 to 65535 will be used.
Tip
For more information of service names and port number assignment, please see the following URL: https://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.xhtml.
Getting back to our analogy, each person (datagram) who is entering the building (OS) has the intention of visiting a specific company (application protocol/service). They are instructed to take a specific elevator or staircase (transport layer) to reach the destination company in the building. When the individual (datagram) exits the elevator or staircase, they are faced with a few doors (network ports) to different companies on the same floor. Walking through a door (port) will carry the individual to a specific company. Within the OSI model and TCP/IP protocol suite, the transport layer inserts its own header, which contains the source port number of the sender and the destination port number of the recipient to ensure the datagram goes through the correct network port (doorway). This way, it can reach the relevant application layer protocol to be processed.
The following diagram represents the encapsulation of data. The transport layer inserts our header, which contains the source and destination port addresses:
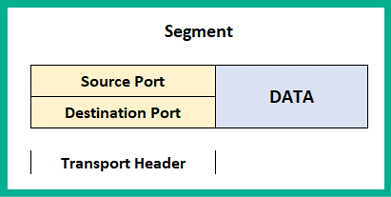
Figure 1.8 – Transport header information
Within the transport layer, there are two protocols that are responsible for the delivery of messages between a sender and a receiver over a network. These are the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP).
Transmission Control Protocol
TCP is often referred to as a connection-oriented protocol that guarantees the delivery of a message between a sender and a receiver. Before messages are exchanged between two devices, a TCP three-way handshake is established.
The following diagram shows the TCP three-way handshake process:
Figure 1.9 – TCP three-way handshake
The following is a live capture I took while using Wireshark. Look closely and you'll notice the sender, 172.16.17.14 (Client A), has sent a TCP Synchronization (SYN) packet to a destination address of 172.16.17.18 (Client B). By default, Client B responds with a TCP acknowledgement but additionally with a TCP SYN because it also wants to communicate with Client A. Hence, a TCP SYN/ACK packet gets returned. Finally, Client A receives the TCP SYN/ACK packet and responds with a TCP ACK to establish the TCP three-way handshake, as shown here:
Figure 1.10 – TCP three-way handshake shown in Wireshark
Once this process is complete, whenever each message is delivered to the recipient, a TCP ACK packet is sent back to the sender, indicating a successful delivery. However, if a sender does not receive a TCP ACK response from a recipient after a certain time, the sender will resend the message until a TCP ACK is received. This is how TCP ensures the delivery of messages on a network. However, due to the high overhead of TCP ACK packets on the network, not all application layer protocols uses TCP as their preferred choice of transport protocol. Some use UDP instead.
User Datagram Protocol
The UDP is a connectionless protocol, known for its best-effort delivery methods. Best-effort simply means the UDP protocol will send the message but will not provide reassurance during delivery. This means that if the message is lost during transmission, UDP will not attempt to resend it. Unlike TCP, it does not provide any message delivery guarantees. If an application layer protocol such as DNS uses UDP for transporting its messages, the transport layer will send it off to its intended destination without any prioritization or any reliability during the message's transmission on the network.
Unlike TCP, UDP does not provide any delivery confirmation, though some application layer protocols prefer UDP for its low overhead and speed on the network.
Layer 3 – Network layer
The network Layer, (Layer 3) is responsible for the logical address on the network and the encapsulation of the IP header, which adds both the source (sender) and destination (receiver) IP version 4 (IPv4) and/or Internet Protocol version 6 (IPv6) addresses to the packet.
This layer provides the following functions:
- Logical addressing of end devices
- Encapsulation and de-encapsulation of datagrams
- Routing (moving packets between networks)
The Internet Protocol (IP) operates at this layer. IP is a connectionless protocol, which means the protocol itself does not establish a session with a recipient before attempting to send or receive messages. In a similar way to the UDP of the upper layer (transport layer), it is also sent using best-effort mechanisms, thus providing no delivery guarantee for IP packets. Lastly, IP can function independently from the medium on the network (copper, fiber optic, or even wireless). Since IP does not have any reliability, the responsibility of ensuring packet delivery depends on the transport layer.
Furthermore, the network layer provides the functionality of directing traffic flows using routing protocols, which operate using the IP. At this layer, routers operate as they have the ability to read and understand IP addressing and the contents of a packet.
When the PDU is passed down to the network layer, it is encapsulated with an IPv4 or an IPv6 header to provide logical addressing, as shown here:
Figure 1.11 – Packet header
Keep in mind that the source and destination IP addresses do not change during their transmission between devices on a network. However, there is one exception: the source IP address changes when it passes a NAT-enabled router, which is configured to change a private IPv4 address into the public IPv4 address of the router's internet-facing interface. We will cover Network Address Translation (NAT) in Chapter 9, Configuring Network Address Translation (NAT).
At this state, the PDU is called a Packet. In later chapters, we'll discuss IPv4 and IPv6 in greater detail.
Layer 2 – Data link layer
The data link layer (Layer 2) of the OSI model is responsible for allowing the messages of the upper layers to access the physical network. It also controls how data is placed and received on the physical network (media), and it handles error detection and flow control. Within the data link layer, there are two sublayers. These are the Logical Link Control (LLC) and the Media Access Control (MAC).
Logical Link Control
LLC encapsulates the packet that's received from the network layer into a frame by adding a Layer 2 header containing the source (sender) and destination (receiver) MAC addresses. At the end of the frame, a trailer is added. The trailer of a frame contains the File Check Sequence (FCS). The data link layer creates a hash value to represent the contents of the frame; this is known as the Cyclic Redundancy Check (CRC) hash value. The CRC value is located in the FCS field of the trailer. The recipient device(s) use this value to determine whether the frame was corrupted or modified during its transmission between the sender and the receiver.
Media Access Control
For a device to connect and communicate on a computer network, a Network Interface Card (NIC) is required. The NIC allows the device to establish a connection to the physical network, regardless of whether the medium is copper or fiber optic cabling, or a wireless connection such as Wi-Fi. The NIC enables a device to exchange messages with another device while using the media (or medium) as the highway.
The MAC address is 48 bits (6 bytes) in length and is presented in the format of hexadecimal values; that is, 0 1 2 3 4 5 6 7 8 9 A B C D E F. An example of a MAC address is 12 : 34 : 56 : 78 : 9A : BC. The first 24 bits of the MAC address are known as the Organization Unique Identifier (OUI). The OUI identifies the manufacturer of the Network Interface Card (NIC) and the second 24 bits are assigned by the manufacturer. The MAC address is also known as a burned-in address (BIA) since it is hardcoded onto the hardware and, theoretically, can't be changed.
The following diagram represents a datagram known as the Frame. It contains both a Data Link Header and a Trailer:
Figure 1.12 – Frame header
Notice that an additional field inserted called the Preamble. The Preamble is a 7-byte field used on an Ethernet frame to indicate the start of the frame, its sequencing, and its synchronization. Before the data link layer places a message on the physical layer, it needs to break it up into smaller piece called bits. Each bit will contain the addressing headers, trailers, and the preamble, which contains a sequence for each bit.
The following diagram represents a depiction of two computers. PC A is sending some messages to PC B and since the blocks represent the message, it has been segmented into small bits. These are then sent across the network to the recipient:
Figure 1.13 – Bits moving across the physical layer
When the bits are received on the destination device, the sequence numbers of each bit will help the recipient reassemble the bits into a message.
To check the MAC address of your network adapters on a Microsoft Windows operating system, use the following instructions:
- On your Windows computer, use the keyboard combination Windows Key + R to open Run.
- Enter
cmd and click OK.
- The Windows Command Prompt window will appear; enter
ipconfig /all to display the current settings of all the network adapters on your device.The following screenshot shows the output after running the ipconfig /all command:
Figure 1.14 – MAC address on a Windows device
On Microsoft Windows, the Physical Address is the MAC address of the NIC.
Important note
On some operating systems, the MAC address is shown in XX:XX:XX:XX:XX:XX, XXXX.XXXX.XXXX, or XX-XX-XX-XX-XX-XX format.
Additionally, if you would like to determine the manufacturer of the device, use the following steps:
- Open your web browser and go to https://www.wireshark.org/tools/oui-lookup.html. You can enter the search term
mac vendor lookup to discover more OUI lookup websites on the internet.
- Enter the MAC address of the NIC in the search field and start the search.
The following is the OUI search results:
Figure 1.15 – MAC vendor lookup
Now that you know about the data link layer, how to determine the MAC address, and how to perform a vendor lookup, let's take a look at the physical layer.
Layer 1 – Physical layer
The physical layer (Layer 1) is used to transport the messages that are created by the host device using network media. When messages are placed on the media, they are converted into signals such as electrical, light, and radio frequency, depending on the medium (copper, fiber, or wireless). At this layer, the PDU is known as bits.
Network components
In very network there is some form of media that's used to transport messages (signals) between devices. Ethernet is the underlying technology standard that describes how messages (signals) are transmitted over a cable at a defined speed. Ethernet is part of a family of communication standards developed by the Institute of Electrical and Electronic Engineers (IEEE).
Important note
Specifically, Ethernet is defined by IEEE 802.3.
Furthermore, Ethernet has standards for both copper and fiber optic cabling and supports speeds ranging from 10 Megabits per second (Mbps) to 10 Gigabits per second (Gbps). Keep in mind that these speeds may vary based on various variables, such as the length of the cable, the type of cable, and whether the signals are transmitted through copper or fiber.
There are two main types of cabling that are used on an Ethernet network: copper and fiber. In the following sections, we will outline the characteristics of each type and their use cases.
Copper cabling is very cheap and easy to implement in almost all environments. There are two popular types of copper cables: Unshielded Twisted Pair (UTP) and Shielded Twisted Pair (STP).
Important note
STP cables provide protection from electromagnetic interference (EMI) compared to the UTP cable. However, due to this added feature, the cost of STP cables is a bit higher because a metal shielding is used during the manufacturing process and this needs to be grounded.
Each of these cables contains a total of eight copper wires, each of which has their own color code, as follows:
- Green
- White and green
- Orange
- White and orange
- Blue
- White and blue
- Brown
- White and brown
With copper, there are a number of cable categories. The following are the characteristics of various cables:
- Cat 3: Contains two pairs of twisted wires and supports
10 Mbps at a maximum distance of 100 meters
- Cat 5: Contains four pairs of twisted wires and supports up to
100 Mbps at a maximum distance of 100 meters.
- Cat 5e: Contains four pairs of twisted wires and supports up to
1,000 Mbps at a maximum distance of 100 meters.
- Cat 6: Supports up to
10 Gbps from up to 37 to 55 meters.
- Cat 6a: Supports up to
10 Gbps from up to 100 meters.
- Cat 7: Supports up to
10 Gbps from up to 100 meters.
Copper cables are all susceptible to attenuation. Attenuation is the loss of signal over a great distance. In the field of networking, when a device is sending a signal over the wire, the longer the distance the signal has to travel, the more likely the signal will deteriorate (get weaker) as it's moving along the wire.
Nowadays, ISPs are rolling out fiber-optic cables between their head offices and their customers' locations to provide increased bandwidth and other services. You may be wondering, what is fiber optic? Fiber uses light pulses to exchange messages in the form of bits. These light pluses are generated using light-emitting diodes (LEDs) rather than electrical signals used in the regular network cables we are accustomed to. Since fiber cables uses light pulses, this creates a major benefit for network and telecommunication professionals.
The core material a fiber cable is made with is either glass or plastic. The plastic core is cheaper to manufacture and therefore the fiber cable itself is cheaper to the customer. Additionally, it is less fragile compared to a cable with a glass core. The glass core allows for higher throughput due to its less dense material. Keep in mind that neither a glass or plastic core can be bent; both cores can be broken easily with very light force.
Fiber has some benefits; for example, much larger throughputs of network traffic can be supported, signals can travel along a fiber cable for many kilometers without experiencing signal loss, it's immune to EMI and RFI, and it allows service providers to transport more services and bandwidth to customers. However, there are a couple of disadvantages. The cost of fiber is a lot higher than the cost of copper cables because of the material composition. Also, the fragile nature of the fiber optic core (glass or plastic) makes the cable susceptible to damage.
Fiber optic cables can operate in two modes: single mode fiber and multi-mode fiber. The following are the characteristics of these two modes:
Single-mode fiber has the following characteristics:
- Small core
- Suited for long distances
- Uses laser as the light source
- Produces a single straight path for light
- Commonly used to interconnect cities
Multi-mode fiber has the following characteristics:
- Has a larger core
- Suited for long distance but shorter than single-mode fiber
- Uses LEDs as the light source
- Commonly used on LANs
- Allows multiple paths for light
With that, we have covered all the layers of the OSI reference model in detail. Now, let's take a look at the TCP/IP protocol with reference to each network layer.
Understanding the TCP/IP protocol suite
As mentioned in the earlier sections of this chapter, the TCP/IP was developed by the US Department of Defense and has been implemented in all networking devices since its approval. The protocol suite is currently maintained by the Internet Engineering Task Force (IETF).
Unlike the OSI reference model, the new updated TCP/IP protocol suite has five layers. The following diagram displays the five layers, along with their alignment to the OSI model:
Figure 1.16 – OSI model and TCP/IP protocol suite comparison
To compare, the upper layers of the OSI model (application, presentation, and session) are equivalent to the application layer (Layer 4) of the TCP/IP protocol suite. The transport layer of the OSI model remains the same for TCP/IP; however, the data link and physical layers are also equivalent to Layers 1 and 2 of the TCP/IP suite.
Keep in mind that TCP/IP has been implemented in all network-connected devices, ranging from end devices and smartphones to servers and network devices.
 United States
United States
 Great Britain
Great Britain
 India
India
 Germany
Germany
 France
France
 Canada
Canada
 Russia
Russia
 Spain
Spain
 Brazil
Brazil
 Australia
Australia
 Singapore
Singapore
 Hungary
Hungary
 Ukraine
Ukraine
 Luxembourg
Luxembourg
 Estonia
Estonia
 Lithuania
Lithuania
 South Korea
South Korea
 Turkey
Turkey
 Switzerland
Switzerland
 Colombia
Colombia
 Taiwan
Taiwan
 Chile
Chile
 Norway
Norway
 Ecuador
Ecuador
 Indonesia
Indonesia
 New Zealand
New Zealand
 Cyprus
Cyprus
 Denmark
Denmark
 Finland
Finland
 Poland
Poland
 Malta
Malta
 Czechia
Czechia
 Austria
Austria
 Sweden
Sweden
 Italy
Italy
 Egypt
Egypt
 Belgium
Belgium
 Portugal
Portugal
 Slovenia
Slovenia
 Ireland
Ireland
 Romania
Romania
 Greece
Greece
 Argentina
Argentina
 Netherlands
Netherlands
 Bulgaria
Bulgaria
 Latvia
Latvia
 South Africa
South Africa
 Malaysia
Malaysia
 Japan
Japan
 Slovakia
Slovakia
 Philippines
Philippines
 Mexico
Mexico
 Thailand
Thailand
















