Dealing with multiple virtual machines simultaneously can become tedious, time-consuming, and frustrating. To reduce the requirement of jumping from one VMware screen to the next and to increase the ease of communication between your virtual systems, it is very helpful to have SSH configured and enabled on each of them. This recipe will discuss how you can use SSH on each of your Linux virtual machines.
Configuring and using SSH
Getting ready
To use SSH on your virtual machines, you must first have an SSH client installed on your host system. An SSH client is integrated into most Linux and macOS systems and can be accessed from a Terminal interface. If you are using a Windows host, you will need to download and install a Windows Terminal services client. One that is free and easy to use is PuTTY.
PuTTY can be downloaded from http://www.putty.org/.
How to do it...
Follow along to configure the SSH client (we are using PuTTY) on the Kali Linix:
- You will initially need to enable SSH directly from the Terminal in the graphical desktop interface. This command will need to be run directly within the virtual machine client. With the exception of the Windows XP virtual machine, all of the other virtual machines in the lab are Linux distributions and should natively support SSH. If you followed along in the Managing Kali Services recipe, the SSH service should already be running. If not, the technique to enable this is the same in nearly all Linux distributions and is shown as follows:
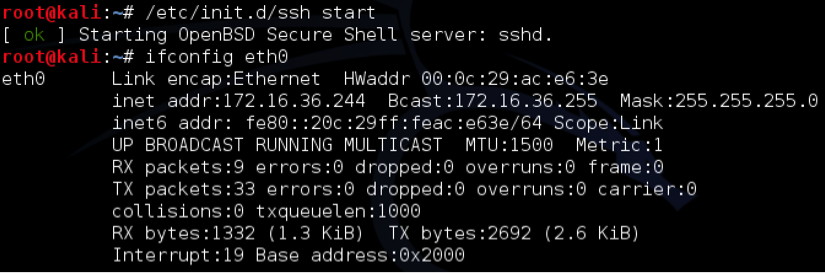
- The /etc/init.d/ssh start command will start the service. You will need to prepend sudo to this command if you are not logged in as root.
- If an error is received, it is possible that the SSH daemon has not been installed on the device. If this is the case, the apt-get install ssh command can be used to install the SSH daemon. Then, ifconfig can be used to acquire the IP address of the system, which will be used to establish the SSH connection.
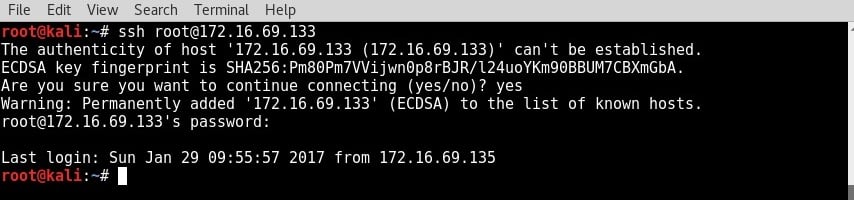
- Once activated, it is possible to access the VMware guest system using SSH from your host system. To do this, minimize the virtual machine and open your host's SSH client.
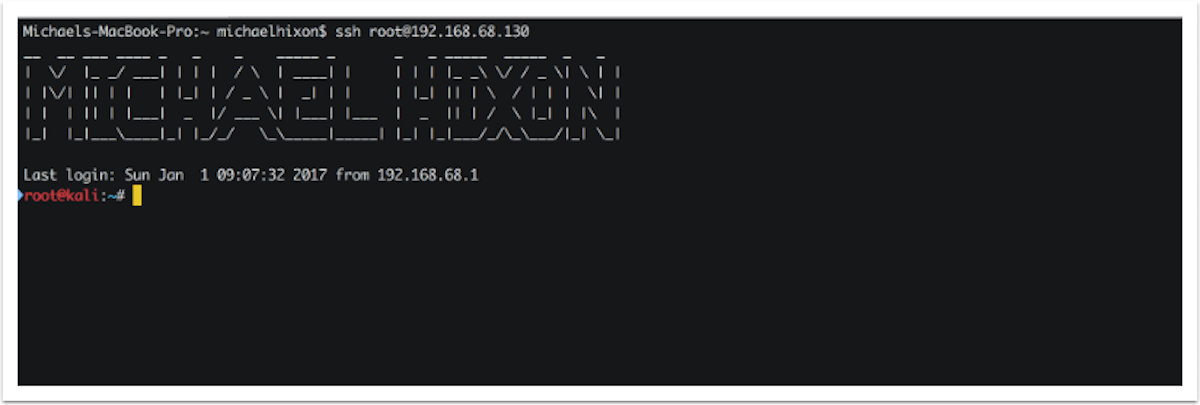
- If you are using macOS or Linux for your host system, the client can be called directly from the Terminal. Alternatively, if you are running your VMs on a Windows host, you will need to use a Terminal emulator such as PuTTY. In the following example, an SSH session is established by supplying the IP address of the Kali virtual machine:
Downloading the example code
You can download the example code files for all Packt books you have purchased from your account at http://www.packtpub.com. If you purchased this book elsewhere, you can visit http://www.packtpub.com/support and register to have the files e-mailed directly to you.
You can download the example code files for all Packt books you have purchased from your account at http://www.packtpub.com. If you purchased this book elsewhere, you can visit http://www.packtpub.com/support and register to have the files e-mailed directly to you.
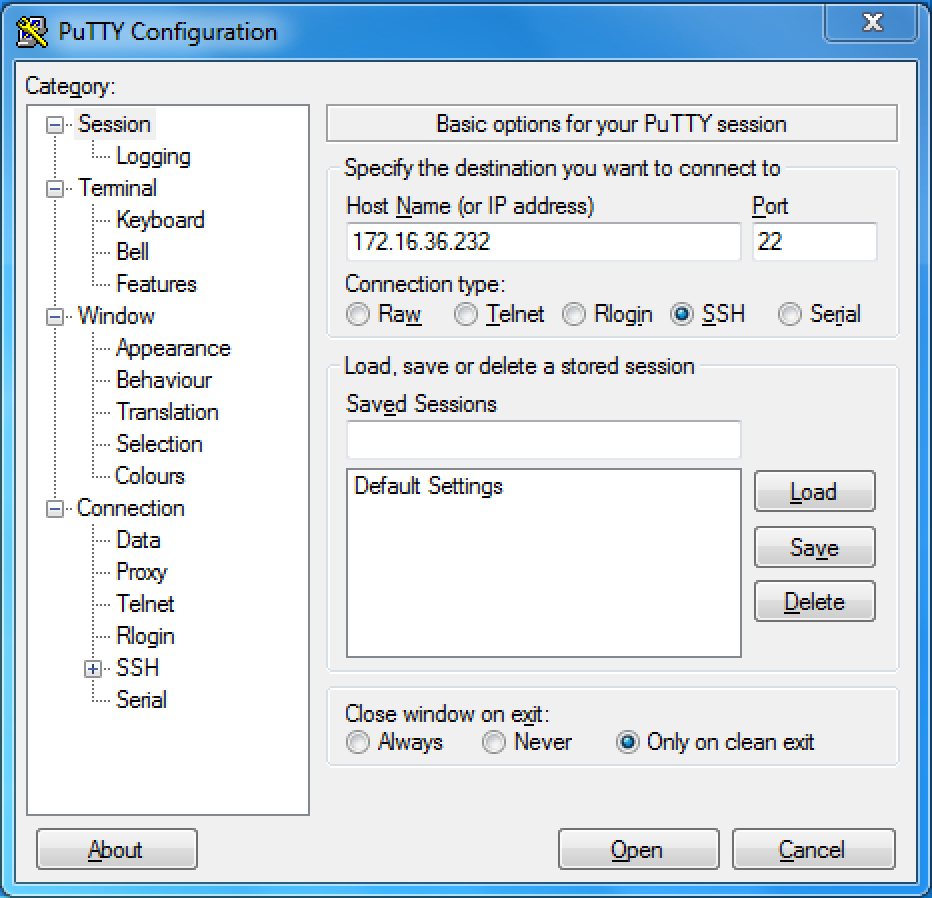
- Once the connection configurations have been set, click on the Open button to launch the session. We will then be prompted for the username and password. We should enter the credentials for the system that we are connecting to. Once the authentication process is completed, we will be granted remote Terminal access to the system, as seen in the following screenshot:
- It is possible to avoid having to authenticate every time by providing your public key in the authorized_keys file on the remote host. The process to do this is as follows:
ssh-copy-id (user)@(host)
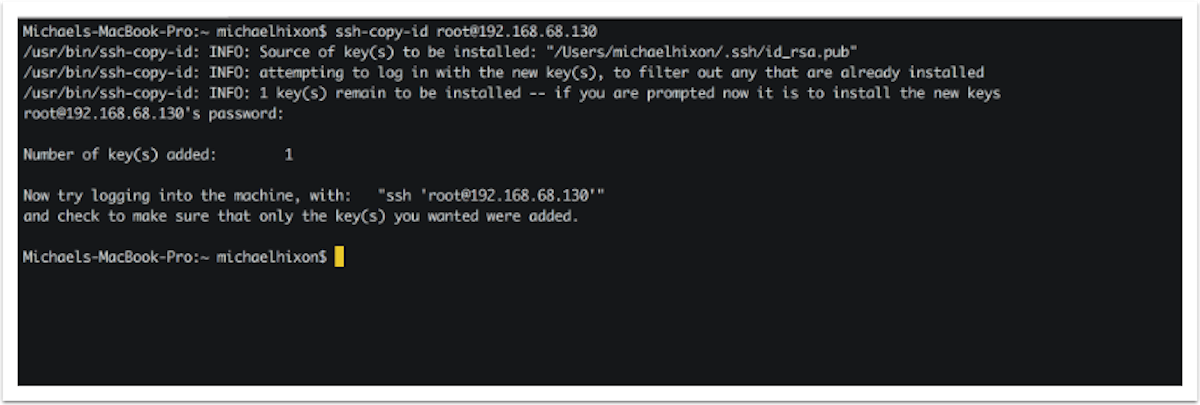
- Once you have done this, you should be able to connect to SSH without having to supply the password for authentication:
How it works...
SSH establishes an encrypted communication channel between the client and server. This channel can be used to provide remote management services and to securely transfer files with Secure Copy (scp).


























































