Encode/Decode/Hash dialog
In this recipe, we are going to go over how to perform encoding and decoding and hashing in ZAP Proxy.
Getting ready
For you to be able to go over this recipe, you will need to have ZAP installed on your computer and also have it started and running.
How to do it…
Encoding is the process of converting data from one form to another, whereas decoding is reversing this conversion. ZAP comes built with a feature to aid its users with a quick way to convert and divert data. In addition to this process, and contained within the same setting, is a feature that creates simple hashes of that data. To get started, select from the menu bar at the top tools, then a little over halfway down, select Encode/Decode/Hash.
Tip
For a shortcut hotkey, on a Windows system, press Ctrl + E. On a macOS system, press Command + E.
When the editor opens, the first thing to note is the input field, which you use to enter the text you wish to encode, decode, and hash, determine illegal UTF-8 bytes, or convert to Unicode. Once you enter the desired text, all the fields will automatically be converted for you.
Next, there is a toolbar that offers a few options. These are as follows:
- Add new tab: Adds a new tab
- Delete selected tab: Removes the currently selected tab
- Add output panel: Adds an output panel to the current tab
- Reset: Resets all the tabs to their default state
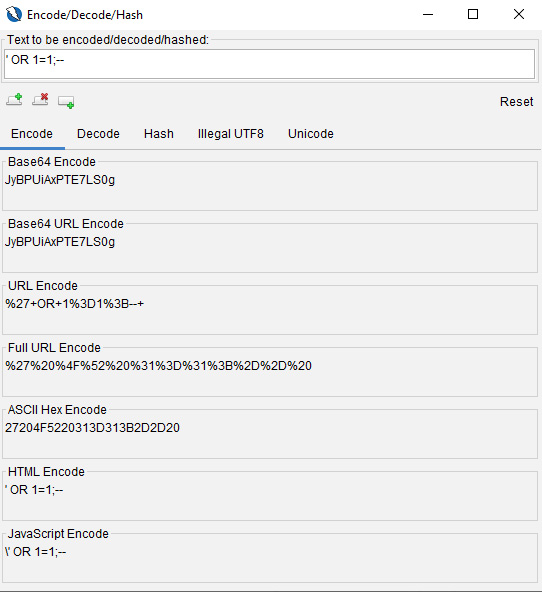
Figure 2.28 – The Encode/Decode/Hash dialog box
As indicated in the Script drop-down menu in the output panel in Figure 2.29, a user can add new fields for comparing data.
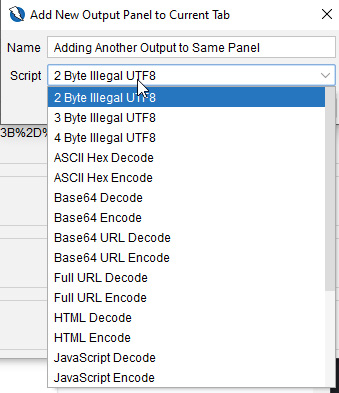
Figure 2.29 – The output panel
With your encoded or hashed script, we’ll move on to fuzzing and how to configure different options for optimizing your approach to web application penetration testing.
How it works…
Using this tool can quickly change operational use with wordlists used in fuzzing applications with attack vectors such as cross-site scripting, SQL injection, and so on. The ability to quickly get a list of different values can help in bypassing poorly implemented validation or encoding in web applications.
See also
For a tool with robust operations for encoding, decoding, and hashing strings, check out CyberChef: https://gchq.github.io/CyberChef/.

































































