AWS and cloud in general have evolved considerably from the time when security in cloud was seen as an impediment to moving your data, applications, and workload to cloud to today when security in cloud is one of the major reasons organizations are moving from data centers to cloud. More and more executives, decision makers, and key stakeholders are vouching that security in cloud is further ahead, and more reliable and economical than security in on-premise data centers. These executives and decision makers are from multiple geographies, and various industries with stringent security requirements and regulatory compliance such as Department of Defense, Banking, Health Care, Payment Card Industry, and so on, and belong to all levels such as CIO, CTO, CEO, CISO, System Administrators, Project Managers, Developers, Security Analysts, and so on.
As a result, cloud adoption rate has been rapidly increasing for the past few years across the globe and across industries. This trend is led by large enterprises where security plays a pivotal role in deciding if an enterprise should move to the cloud or not. AWS provides fully integrated and unified security solutions for its cloud services that enables its customers to migrate their workloads to cloud. Let us look at some predictions for the exponential growth of Cloud Computing by industry leaders:
- Gartner says that by 2020, a corporate no-cloud policy will be as rare as the no-internet policy today.
- Global Cloud Index (GCI) forecasts that cloud will account for 92% of the data center by 2020, meaning 92% of all data and computing resources will be using cloud by 2020.
- International Data Corporation (IDC) says that today's cloud first strategy is already moving the towards cloud.
AWS is architected to be one of the most flexible and secure cloud environments. It removes most of the security burdens that are traditionally associated with IT infrastructure. AWS ensures complete customer privacy and segregation of customer resources and has scores of built-in security features. Moreover, every customer benefits from the security processes, global infrastructure and network architecture put in place by AWS to comply with stringent security and compliance requirements by thousands of customers across the globe from scores of industries.
As more and more organizations move towards cloud, security in cloud has been more of a paradigm shift for many. Even though for the most part, security that is provided in cloud has most of the same functionalities as security in traditional IT, such as protecting information from theft, data leakage, and deletion.
However, security in the cloud is in fact slightly different to security in an on-premises data center. When you move servers, data and workload to AWS cloud, responsibilities are shared between you and AWS for securing your data and workload. AWS is responsible for securing the underlying infrastructure that supports the cloud through its global network of regions, availability zones, edge locations, end points, and so on, and customers are responsible for anything they put on the cloud such as their data, their application, or anything that they connect to the cloud such as the servers in their data centers. They are also responsible for providing access to their virtual network and resources in cloud, this model is known as AWS shared security responsibility model.
The following figure depicts this model:
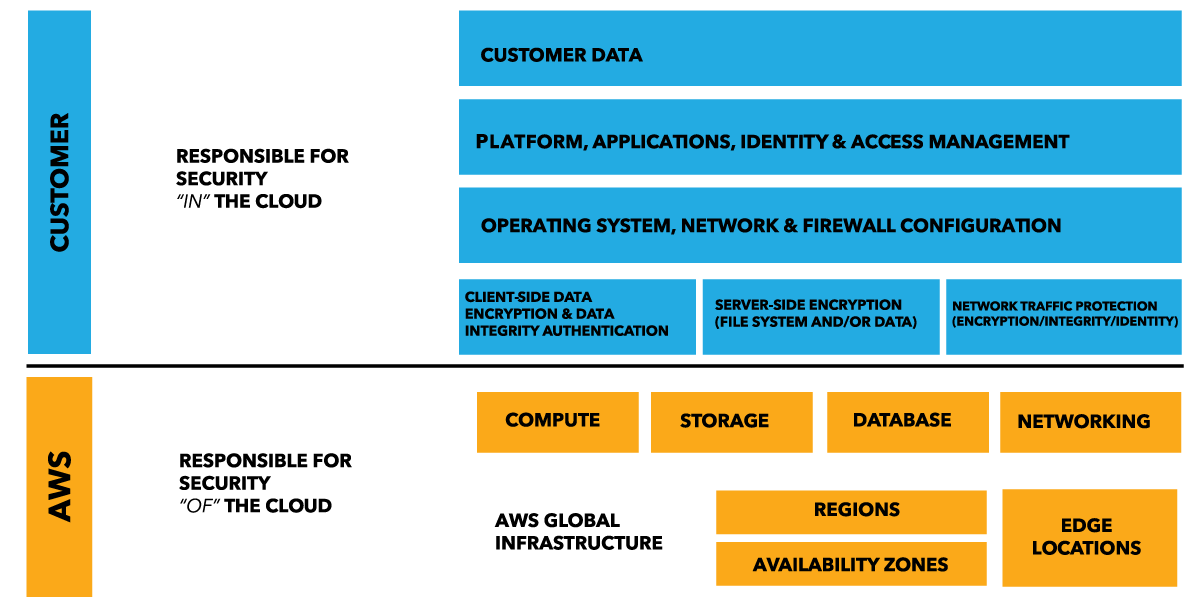
In order to master AWS Security, it is imperative for us to identify and understand AWS' share of security responsibilities as well as our share of security responsibilities before we start implementing them. AWS offers a host of different services that can be distributed in three broad categories: infrastructure, container, and abstracted services. Each of these categories has its own security ownership model based on how end users interact with it and how the functionality is accessed:
- Infrastructure Services: This category includes compute services such as Amazon Elastic Cloud Compute (EC2) and associated services, such as Amazon Elastic Block Store (EBS), Elastic Load Balancing, and Amazon Virtual Private Cloud (VPC). These services let you design and build your own secure and private network on cloud with infrastructure similar to your on-premises solutions. This network in AWS cloud is also compatible and can be integrated with your on-premises network. You control the operating system, configure the firewall rules and operate any identity management system that provides access to the user layer of the virtualization stack.
-
Container Services: There are certain AWS services that run on separate Amazon EC2 or other infrastructure instances but at times you don’t manage the operating system or the platform layer. AWS offers these services in a managed services model for these application containers. You are responsible for configuring firewall rules, allowing access to your users and systems for these services using AWS Identity and Access Management (IAM) among other things. These services include AWS Elastic Beanstalk, Amazon Elastic Map Reduce (EMR) and Amazon Relational Database Services (RDS).
- Abstracted Services: These are AWS services that abstract the platform or management layer. These are messaging, email, NoSQL database, and storage services on which you can build and operate cloud applications. These services are accessed through endpoints by using AWS APIs. AWS manages the underlying service components or the operating system on which they reside. You share the underlying infrastructure that AWS provides for these abstracted services. These services provide a multi-tenant platform which isolates your data from other users. These services are integrated with AWS IAM for secure access and usage. These services include Simple Queue Service, Amazon DynamoDB, SNS, Amazon Simple Storage Service (S3), and so on.
Let us look at these 3 categories in detail along with their shared security responsibility models: