Penetration testing is not just a single activity, but a complete process. There are several standards available that outline steps to be followed during a penetration test. This section aims at introducing the penetration testing lifecycle in general and some of the industry-recognized penetration testing standards.
Penetration testing standards
Penetration testing lifecycle
Penetration testing is not just about using random tools to scan the targets for vulnerabilities, but a detail-oriented process involving multiple phases. The following diagram shows various stages of the penetration testing lifecycle:
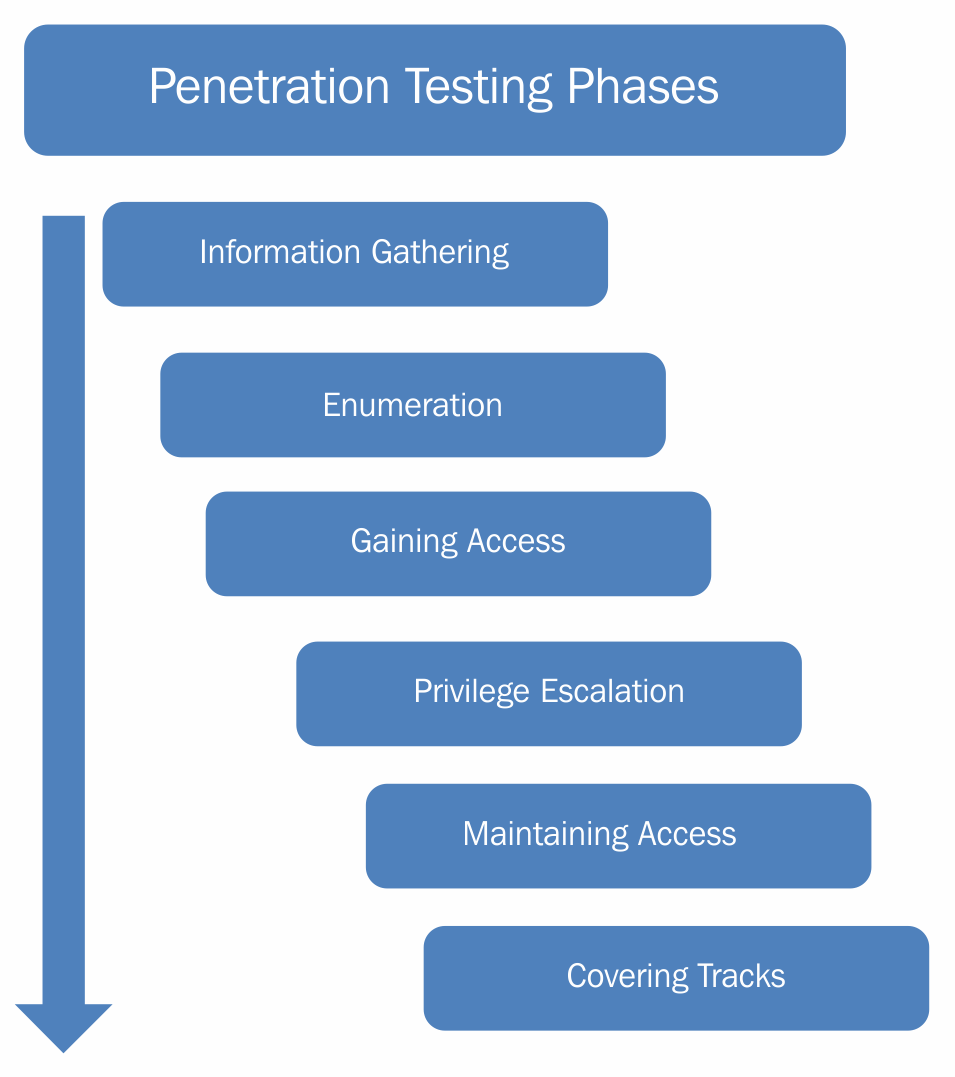
- Information gathering phase: The information gathering phase is the first and most important phase of the penetration testing lifecycle. Before we can explore vulnerabilities on the target system, it is crucial to gather information about the target system. The more information you gather, the greater is the possibility of successful penetration. Without properly knowing the target system, it's not possible to precisely target the vulnerabilities. Information gathering can be of two types:
- Passive information gathering: In passive information gathering, no direct contact with the target is established. For example, information about a target could be obtained from publicly available sources, such as search engines. Hence, no direct contact with the target is made.
- Active information gathering: In active information gathering, a direct contact with the target is established in order to probe for information. For example, a ping scan to detect live hosts in a network would actually send packets to each of the target hosts.
- Enumeration: Once the basic information about the target is available, the next phase is to enumerate the information for more details. For example, during the information gathering phase, we might have a list of live IP's in a network. Now we need to enumerate all these live IPs and possibly get the following information:
- The operating system running on the target IPs
- Services running on each of the target IPs
- Exact versions of services discovered
- User accounts
- File shares, and so on
- Gaining access: Once the information gathering and enumeration have been performed thoroughly, we will have a detailed blueprint of our target system/network. Based on this blueprint, we can now plan to launch various attacks to compromise and gain access to the target system.
- Privilege escalation: We may exploit a particular vulnerability in the target system and gain access to it. However, it's quite possible that the access is limited with privileges. We may want to have full administrator/root-level access. Various privilege escalation techniques could be employed to elevate the access from a normal user to that of an administrator/root.
- Maintaining access: By now, we might have gained high-privilege access to our target system. However, that access might last only for a while, for a particular period. We would not like to have to repeat all the efforts again, in case we want to gain the same access to the target system. Hence, using various techniques, we can make our access to the compromised system persistent.
- Covering tracks: After all the penetration has been completed and documented, we might want to clear the tracks and traces, including tools and backdoors used in the compromise. Depending on the penetration testing agreement, this phase may or may not be required.













































































