Differences between ISO 27001 and NIST
As it has fewer controls to implement, and since there’s no control over it (NIST doesn’t have a certification scheme), NIST is considered somewhat less mature; also, as it is backed by the US government and not an international committee, it is not considered much outside the US. But if you like plain instructions and don’t want to spend a fortune, at least in the beginning, it can be a good idea to use NIST. Finally, it is possible to get the best of both worlds by implementing both at the same time.
What’s NIST?
The National Institute of Standards and Technology (NIST) is a non-regulatory US government agency founded in 1901 that develops technology, standards, and metrics to drive innovation in the US science and technology sectors. NIST is headquartered in Gaithersburg, Maryland.
NIST publishes the Special Publication 800 series, which contains guidance documents and recommendations. As part of the previous series, they released Special Publication 800-53, which catalogs 20 security and privacy control groups. NIST recommends that entities implement these security and privacy controls as part of their risk management strategies. These controls cover access control, security awareness training, incident response plans, risk assessments, and continuous monitoring.
The NIST compliance framework was developed to provide a customizable guide for entities on how to manage and reduce cybersecurity-related risks. In its guide, NIST combines existing standards, guidelines, and best practices. However, it is critical to understand that simply adhering to NIST guidelines will not make your entity 100% secure, which is why the NIST guidelines begin by instructing entities to use a value-based approach to protect their assets.
The NIST Cybersecurity Framework (CSF) is a voluntary (recommended by the Department of Commerce) cybersecurity framework that allows businesses to develop information security, risk management, and control programs. NIST standards are now used in fields ranging from nanotechnology to cybersecurity. Through an executive order in 2013, NIST was tasked with developing a cybersecurity framework, and in February 2014, it published version 1.0 of the Framework for Improving Critical Infrastructure Cybersecurity. Version 1.1 was released to the public in April 2018.
The CSF is one of NIST’s voluntary programs that is based on existing standards and guidelines and is designed to assist entities in better managing and reducing cybersecurity risk. The CSF is presented in a 48-page document that details various cybersecurity activities and desired outcomes that entities can use to assess their cybersecurity risk, risk maturity, and information security infrastructure.
What is the purpose of the NIST CSF?
The CSF has three major components, the framework core, implementation tiers, and profiles, all of which are designed to help you benchmark your entity’s risk maturity and prioritize actions to improve it.
At its core, it has five functions: identify, protect, detect, respond, and recover.
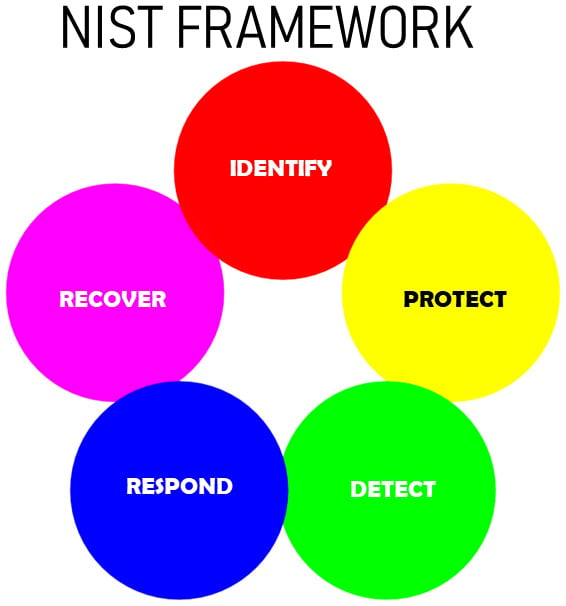
Figure 1.2 – The five functions, NIST
While the CSF focuses on cybersecurity issues, these activities are common in most risk management systems. The functions are further subdivided into 23 categories that cover the fundamentals of putting together a cybersecurity program.
The CSF has implementation tiers. For each of these five functions, the NIST CSF employs a ranking system on a scale of 0-4 to generate a final number that can be used to benchmark an entity’s level of risk maturity.
A profile, which is based on a tier, allows an entity to pinpoint its current level of risk tolerance and prioritize security controls and risk mitigation tactics. This section is intended to assist an entity in growing by comparing its current profile to target profiles, thereby assisting you in determining how to allocate budget and employee resources to improve cybersecurity practices over time.
What are the parallels between ISO and NIST?
When comparing NIST CSF and ISO 27001, both provide strong frameworks for cybersecurity risk management. It would be simple to integrate ISO 27001 standards and NIST CSF into a company that wants to become ISO 27001 compliant. Their control measures are comparable, and their definitions and code are fairly interchangeable across frameworks. Both frameworks provide simple vocabulary, which enables clear communication about cybersecurity issues across multidisciplinary teams and with external stakeholders.
What’s the distinction between ISO and NIST?
There are a few key differences between NIST CSF and ISO 27001, including risk maturity, certification, and cost.
Risk maturity
ISO 27001 is a good choice for operationally mature entities seeking certification, whereas the NIST CSF may be best for entities in the early stages of developing a cybersecurity risk management plan or attempting to mitigate previous failures or data breaches.
ISO 27001 certification provides globally recognized certification through third-party auditing, which can be costly but can improve your entity’s reputation as a business that stakeholders can rely on. The NIST CSF does not provide such certification.
Cost
The NIST CSF is free to use, whereas ISO 27001 requires a fee to access the documentation—another reason why a start-up might want to start with the NIST CSF and then make a larger investment in the process as it scales with ISO 27001.
NIST versus ISO – which is better for my company?
Finally, what is best for your company is determined by its maturity, goals, and specific risk management requirements. ISO 27001 is an excellent choice for operationally mature entities that are under external certification pressure. However, you may not be ready to embark on an ISO 27001 certification journey just yet, or your entity may be at a stage where it would benefit from the NIST CSF’s clear assessment framework. A NIST audit can provide you with an idea of where your entity stands before developing and implementing more stringent cybersecurity measures and controls.
As your entity matures, the two frameworks can be integrated—following the NIST CSF can be a useful precursor to your ISO 27001 certification journey. The NIST CSF provides a framework for growing entities to structure their Information Security (IS) risk assessments. If you already have these structures in place, you may want to pursue ISO security and compliance certifications. A proactive and efficient ISMS benefits from the right software, whether you’re starting with NIST CSF or growing with ISO 27001.

























































