The MITRE ATT&CK framework explained
As we have mentioned before, different cybersecurity vendors commonly give different names to hacker groups and malware families. Therefore, knowledge exchange becomes more complicated, eventually affecting the performance of the community. The MITRE ATT&CK framework was created to address this and other similar issues and let security experts speak the same language. This is a vendor-agnostic global knowledge base on various attack techniques grouped into tactics, which also provides examples of the attackers and malware utilizing them, giving the tactics widely accepted names.
Basic terminology
Here are some of the most important terms used in this field:
- Tactic: Represents a high-level goal of the attacker, a reason why the corresponding action is performed
- Technique: The practical way in which the defined high-level goal is achieved
- Sub-technique: A more detailed and granular description of how exactly a certain action is conducted
- Procedure: An actual implementation of the technique/sub-technique
- TTPs: Stands for tactics, techniques, and procedures: a summary of the methods used by attackers with an explanation of what is achieved by utilizing them
- Group: Represents a set of related adversarial activities likely to be performed by a single entity known under this name
- Mitigation: Technology and concepts that are used to circumvent or prevent an attack
- Software: Code that can be used to conduct adversary actions, combining both publicly available tools and malware
- Matrix: A combination of TTPs related to a particular industry secto
There are several matrices within the framework for the enterprise, Industrial Control Systems (ICSs), and mobile sectors. The most commonly used one is the Enterprise Matrix, so let’s talk about it in greater detail.
Enterprise Matrix
At present, the Enterprise framework defines the following tactics:
- Reconnaissance: This stage involves collecting relevant information about the victim to perform a successful attack, for example, about some organization’s infrastructure and personnel.
- Resource development: Here, attackers establish all the required dependencies based on the collected information. This can be achieved by various means: buying/renting, creating, or stealing the prerequisites (for example, hosting or software).
- Initial access: At this stage, attackers attempt to establish the first foothold within the victim’s environment. One of the most common examples of this tactic is sending spear-phishing messages (mainly emails).
- Execution: Here, attackers execute code of any kind within the victim’s environment to achieve their goals.
- Persistence: Includes everything attackers do to maintain their presence within the compromised environment. Common examples include adding malicious code to autorun or adding SSH keys to the list of authorized entries.
- Privilege escalation: As the initial access is in many cases achieved by compromising low-access accounts, here, attackers attempt to gain higher-level permissions to have more control over the affected environment.
- Defense evasion: The main goal of the attackers here is to avoid being detected until their objective is achieved. Examples include obfuscating malicious code or marking related files as hidden.
- Credential access: This tactic involves stealing credentials to misuse them later. Some of the most common techniques here involve dumping saved credentials and intercepting them, for example, by logging pressed keys.
- Discovery: Here, attackers collect information on the internals of the victim’s environment, starting with the network and the local systems. This information is generally used to facilitate other tactics, such as lateral movement.
- Lateral movement: At this stage, attackers propagate upward to other machines until the systems of interest are reached.
- Collection: Involves collecting various information of interest from the affected systems. Common examples include stealing proprietary source code and documents.
- Command and control: This tactic covers the various ways attackers may remotely communicate with compromised systems.
- Exfiltration: Techniques that attackers may utilize to actually move sensitive information out of the compromised environment.
- Impact: Finally, this tactic describes other ways attackers may have a negative impact on compromised systems. Common examples include the manipulation, interruption, or destruction of critical systems and data.
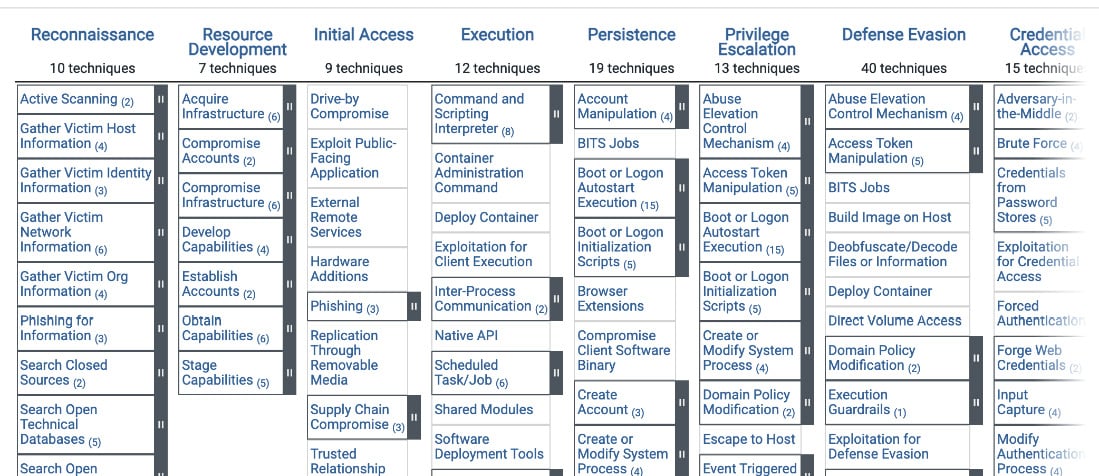
Figure 1.1 – Web representation of the MITRE ATT&CK’s Enterprise Matrix
It is worth mentioning that the framework is not static and constantly evolves, incorporating users’ feedback and addressing the new challenges the industry faces. Each version of the framework is shipped with a Structured Threat Information Expression (STIX) representation of itself: https://github.com/mitre-attack/attack-stix-data. It allows efficient integration with various software products and makes it possible to combine stability and efficiently oversee any changes introduced. STIX is a versatile format that is also commonly used by the cybersecurity community to exchange IoCs, where version 1 is XML-based and version 2 is JSON-based.

























































