Maintenance and snapshotting
Now that the basis for the malware analysis VM has been set up, the tools installed, and everything is ready to go, it is important to ensure that the work does not have to be repeated each time we would like to dynamically analyze a new piece of malware.
If we simply detonated each piece of malware on top of the previous samples, it would confuse our indicators of compromise (IOCs), and we would likely be unable to tell what the result of a previous piece of malware was, what the result of the piece we were analyzing was, and what was just normal system activity.
VirtualBox has a built-in feature that has us covered – Snapshots. A snapshot is exactly as it sounds – a moment-in-time representation of how the VM's filesystem, registry, and other features existed precisely when that snapshot was taken. It allows an analyst to revert a VM to a time before it was purposely infected with malware.
To take a golden-image snapshot of our newly created malware analysis VM, we'll navigate to VirtualBox's main menu, click the hamburger button just to the right of our VM name, and then click Snapshots:
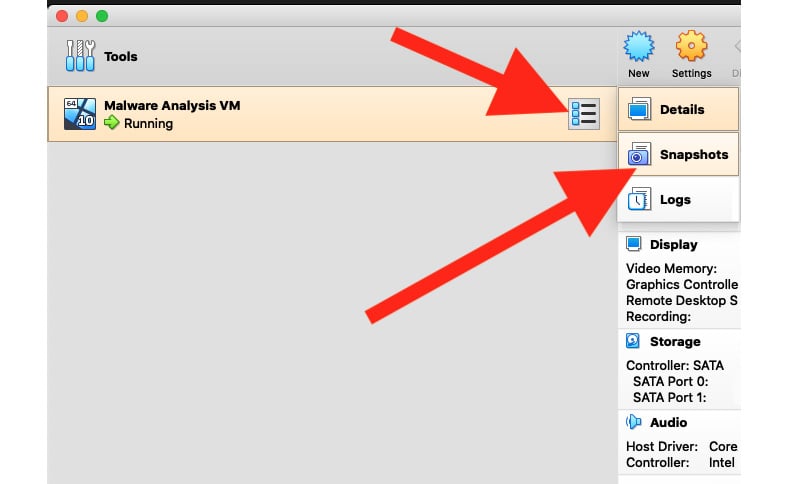
Figure 1.21 – The Snapshots pane to take, manage, and delete any snapshot taken of your VM
Once clicked, the snapshot pane opens, presenting us with the option to take a current snapshot and name it:
Analysis tip
It's best to have highly descriptive snapshot names so that you aren't left guessing and restoring snapshots blindly in an attempt to find the correct one.
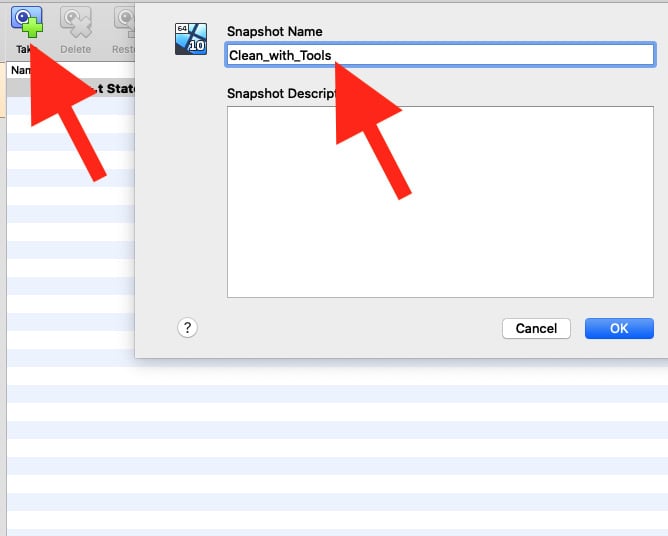
Figure 1.22 – Taking our first snapshot
When OK is clicked, the VM will pause for a few moments to take an image of the moment-in-time configuration and save it for later restoration. Once complete, we'll be able to see our snapshot in the list of available restore points in VirtualBox, as shown in the following screenshot:

Figure 1.23 – The snapshots panel in VirtualBox
Congratulations! You've created your malware analysis VM and ensured that we can continue to use it even after we detonate malware in it several times, returning it to its previous state with the click of a button.
Welcome to your home for the next 10 chapters.
Analysis tip
Snapshots aren't only great for keeping your VM clean! Initial vectors of malware (such as droppers) no longer work after a given period of time. If you have an infected instance of your VM that you think you'd like to study in the future and are unsure whether you'd be able to re-infect it, take a snapshot!














































































