Installing and updating Kali Linux
In the previous editions of this book, we focused on the installation of Kali Linux to VMware Player, VirtualBox, AWS, and the Raspberry Pi using the Docker appliance. In this section, we will touch base on installing Kali Linux on these same platforms, along with Google Cloud Platform, and a non-rooted Android phone.
Using as a portable device
It is fairly simple to install Kali Linux onto a portable device. In some situations, clients do not permit the use of an external laptop inside a secure facility. In those cases, typically, a testing laptop is provided by the client to the pentesters to perform the scan. Running Kali Linux from a portable device has more advantages during a pentest or RTE:
- It can fit inside a pocket, in the case of a USB drive or mobile device.
- It can be run live without making any changes to the host operating system.
- You can customize the build of Kali Linux and even make the storage persistent.
There are three simple steps to make a USB drive into a portable form of Kali from a Windows PC:
- Download the official Kali Linux image from:http://docs.kali.org/introduction/download-official-kali-linux-images
- We will be using the Rufus open-source utility to create a bootable disk. Rufus helps to create and format bootable drives. Download the latest Rufus from https://github.com/pbatard/rufus/releases/
- Open the Rufus executable as an administrator. Plug the USB drive into an available USB port. Browse to the location where you have downloaded your image. You should see what is shown in Figure 1.3. Select the right drive name and then click Start:

Figure 1.3: Running Rufus to write Kali Linux to an external disk
Once complete, close the Rufus application and safely remove the USB drive. Kali Linux is now ready as a portable device to be plugged into any laptop and be booted up. If you plan to store information while booted on a live disk, ensure you select Persistence partition size to have a minimum of 4 GB; then select Live USB persistence while booting Kali Linux on the portable device. If your host operating system is Linux, this can be achieved by two standard commands:
sudo fdisk -l
This will display all of the disks mounted on the drive. The dd command-line utility does the convert and copy:
dd if=kali linux.iso of=/dev/nameofthedrive bs=512k
if is used for the input file, of is for the output file, and bs is for the block size.
Installing Kali on a Raspberry Pi 4
A Raspberry Pi is a single-board device that is compact in nature and can run just like a fully loaded computer with minimal functionalities. These devices are extremely useful during RTE and penetration testing activities while on site. The base of the operating system is loaded from an SD card, just like a hard drive for normal computers.
You can perform the same steps as those outlined in the previous section on a high-speed SD card that can be plugged into a Raspberry Pi. We are then ready to use the system without any issues. If the installation is successful, the following screen must be present when Kali Linux is booted from a Raspberry Pi. A Raspberry Pi 4 has been used in this demonstration and accessed the Pi’s operating system using a monitor:

Figure 1.4: Successful installation of Kali Linux on a Raspberry Pi 4
Installing Kali on a VM
In the previous editions, we discussed how to install Kali to different hypervisors. We will do the same here, and take a very quick detour on how to install Kali on such devices.
VMware Workstation Player
VMware Workstation Player, formerly known as VMware Player, is free for personal use and is also a commercial product for business use from VMware as a desktop application that allows a VM to be run inside your host operating system. This application can be downloaded from https://www.vmware.com/uk/products/workstation-player/workstation-player-evaluation.html
We will be using version 16.1. Once the installer is downloaded, go ahead and install the VMware Player accordingly, based on your host operating system. If the installation is complete, you should see a screen similar to that displayed in Figure 1.5:
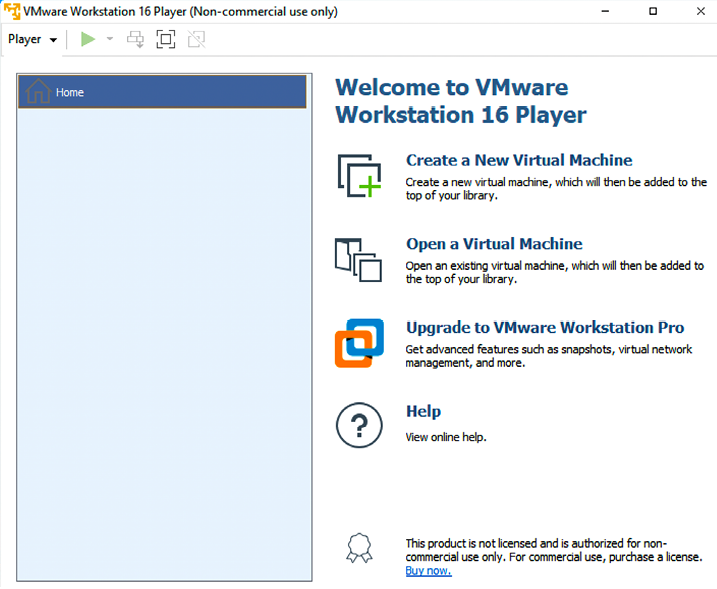
Figure 1.5: Successful installation of VMware Workstation Player
The next step in order to install Kali Linux on VMware is to click on Create a New Virtual Machine and select Installer disc image file (iso). Browse to your ISO file that was downloaded and then click Next. You can now enter a name of your choice (for example, HackBox) and select the Custom Location where you would like to store your VMware image. Click Next and specify the disk capacity. It is recommended that a minimum of 2 GB RAM is used, and 15 GB of disk space is needed to run Kali. Click Next until you finish.
Another method is to directly download the VMware image:
https://www.offensive-security.com/kali-linux-vm-vmware-virtualbox-image-download/
Open the .vmx file and select I copied it. That should boot up the fully loaded Kali Linux in VMware. You can either choose to install Kali Linux as the host operating system or run it as a live image. Once all of the installation steps are complete, you are ready to launch Kali Linux from VMware without any problems. Figure 1.6 shows the screen that should be seen:
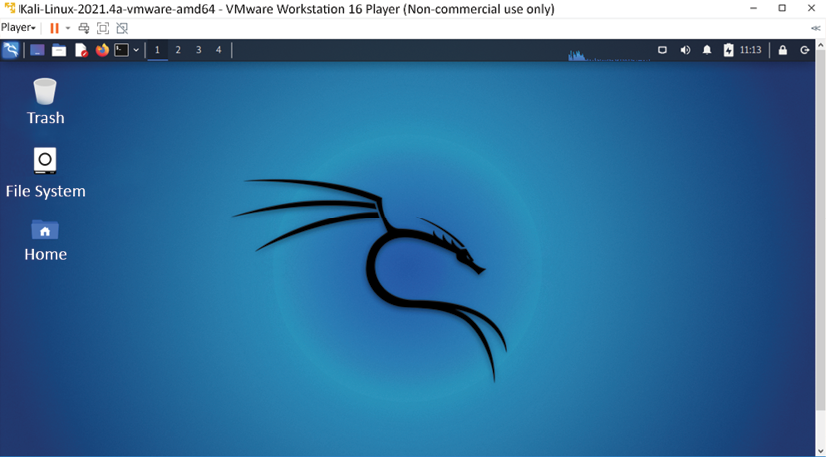
Figure 1.6: Once Kali Linux has been successfully installed on VMware, this display is shown
VirtualBox
Similar to VMware workstation player, VirtualBox is a hypervisor that is completely open-source and a free desktop application from which you can run any VM from the host operating system. This application can be downloaded from https://www.virtualbox.org/wiki/Downloads.
We will now go ahead and install Kali on VirtualBox. Similar to VMware, we will just execute the downloaded executable until we have a successful installation of Oracle VirtualBox, as shown in Figure 1.7:
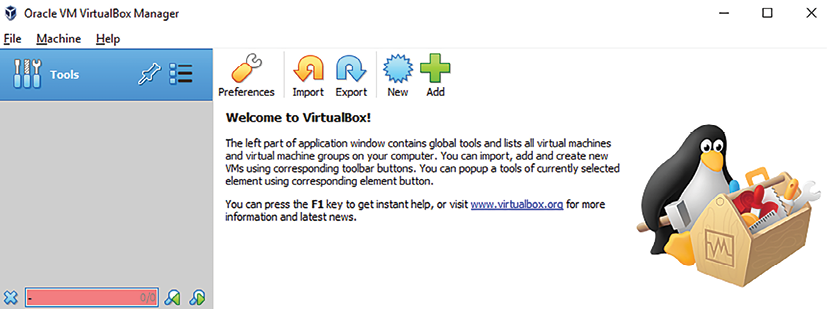
Figure 1.7: Screen displayed upon the successful installation of VM VirtualBox
During installation, it is recommended that you set the RAM to at least 1 or 2 GB, and that you create the virtual hard drive with a minimum of 15 GB so that no performance issues are encountered. After the final step, you should be able to load Kali Linux in VirtualBox, as shown in Figure 1.8:
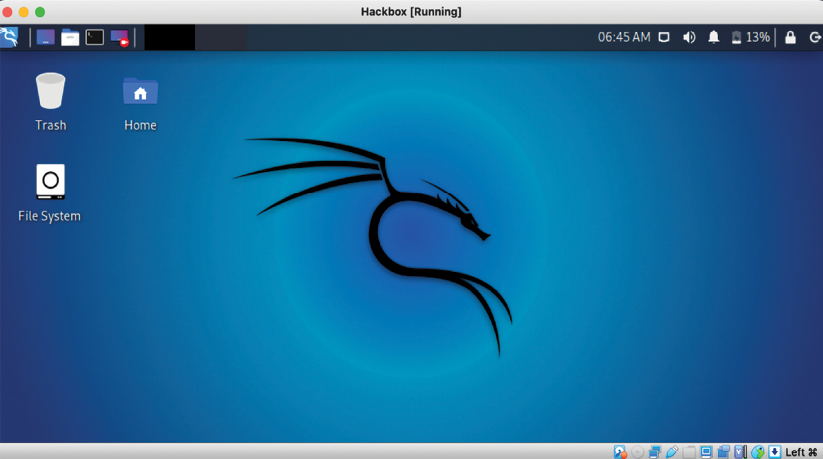
Figure 1.8: Kali Linux, as it displays in VM VirtualBox
After this has been completed, we are now ready to use Kali Linux through VirtualBox. However, we will be exploring the different network options in a further section, LAB network.
Installing to a Docker appliance
Docker is an open-source project that is designed to automate the deployment of software containers and applications instantly. Docker also provides the additional abstraction and automation layer of operating system-level virtualization on Linux or Windows.
Docker is available for Windows, Mac, Linux, and AWS. For Windows, Docker can be downloaded from https://www.docker.com/get-started.
After the Docker installation, it should be fairly simple to run Kali Linux using the following commands:
sudo docker pull kalilinux/kali-rolling
sudo docker run -t -i kalilinux/kali-linux-docker /bin/bash
These can be executed in the Command Prompt (Windows) or Terminal (Linux or Mac) to confirm that the installation has been successful.
We should be able to run Kali Linux directly from Docker, as shown in Figure 1.9. Also note that Docker utilizes container-based technology, which runs its own processes that are isolated from the rest of the operating system, and it shares the host OS kernel. While the VirtualBox environment is not container-based technology, it virtualizes the hardware and shares the hardware resource from the physical host:
Once the Kali Linux Docker image download is complete, you can run the Docker image by running docker run --tty --interactive kalilinux/kali-rolling /bin/bash in Command Prompt or Terminal. You should be able to see the same as what is shown in Figure 1.10:
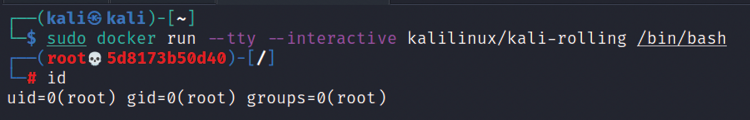
Figure 1.10: Successful running of Kali Linux from Docker
If Windows 10 is your base operating system, ensure that VT-X is enabled on your system BIOS, along with Hyper-V. Note that enabling Hyper-V will disable VirtualBox, as shown in Figure 1.11:
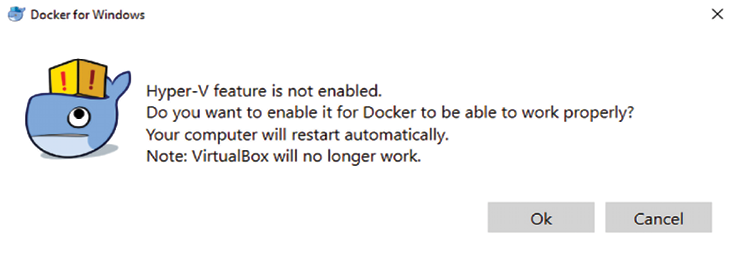
Figure 1.11: An alert that will be shown when installing Docker
Readers should be aware that the following sections involve the usage of commercial services, such as AWS and Google Cloud Platform, that might incur charges while utilizing the services. It is always recommended that readers completely delete or terminate the instances having finished their testing.
Kali on AWS Cloud
Amazon Web Services (AWS) provides Kali Linux as part of Amazon Machine Interface (AMI) and SaaS. Nowadays, the majority of the security testing companies utilize AWS to conduct penetration testing and more efficient phishing attacks. In this section, we will go through the steps to bring up Kali Linux on AWS.
First, you will need to have a valid AWS account. You can sign up by visiting the following URL: https://console.aws.amazon.com/console/home
When logging in to the AWS account, we should be able to see all of the AWS services. Search for Kali Linux, and the following should be displayed, as shown in Figure 1.12.
The page can also be accessed using the following link: https://aws.amazon.com/marketplace/pp/prodview-fznsw3f7mq7to:
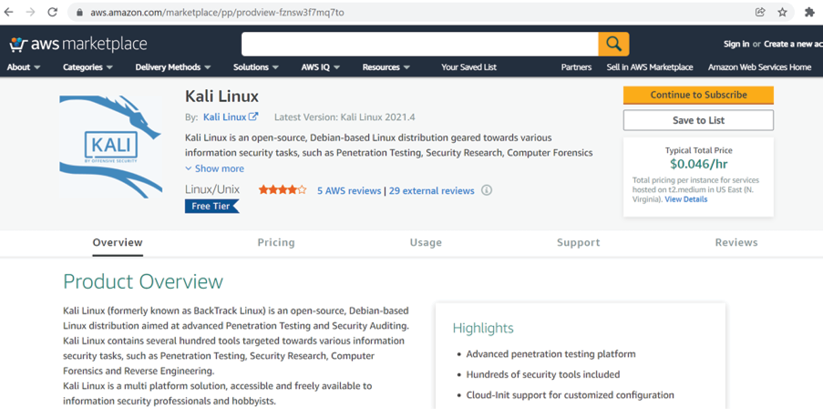
Figure 1.12: Pre-configured Kali Linux in the AWS Marketplace
The open-source community has made it very simple to directly launch a pre-configured Kali Linux 2021.4 instance from the AWS Marketplace. The following will take us to a direct launch of Kali Linux within a few minutes: https://aws.amazon.com/marketplace/pp/prodview-fznsw3f7mq7to.
Follow the instructions; you should then be able to launch the Kali instance by selecting Continue to Subscribe. This should take you to the login page of AWS if not logged in. Click on Continue to Configuration, continue to click on Continue to Launch, and you should arrive at the screen shown in Figure 1.13. From Choose Action, select the option Launch through EC2, also shown in Figure 1.13; finally, click Launch:
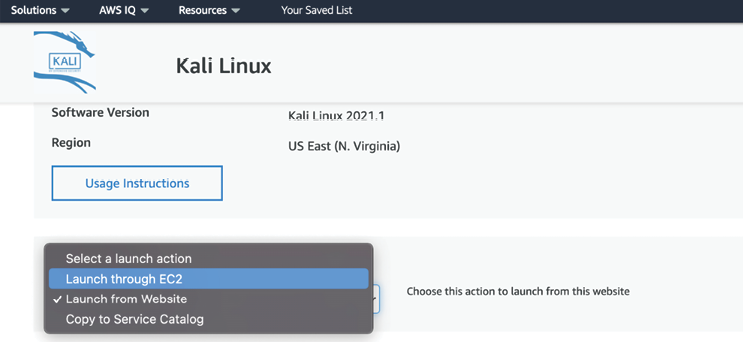
Figure 1.13: Selecting a method to launch Kali Linux through EC2
The next screen will allow you to choose the Instance type; select t2.micro (Free tier eligible) and click on Review and Launch . Finally, you should arrive at Review Instance Launch; click on Launch. This should take us to a screen where a new key pair can be created, as shown in Figure 1.14:
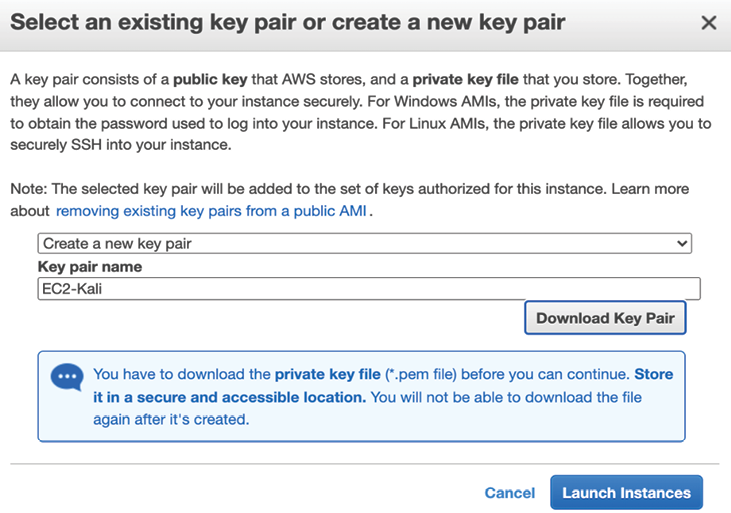
Figure 1.14: Creating a new key pair to connect to AWS instances
As usual, to use any AWS VM, you must create your own key pair in order to ensure the security of the environment. You should then be able to log in by entering the following command from your command shell. In order to use the private key to log in without the password, Amazon enforces the file permission to be tunneled. We will use the following commands to connect to the Kali Linux instance from Terminal:
chmod 400 privatekey.pem
ssh -i privatekey.pem kali@PublicIPofAWS
All Windows users can utilize Windows PowerShell to connect to the instance by running:
ssh -i privatekey.pem kali@PublicIPofAWS
Figure 1.15 depicts the successful usage of Kali on AWS:
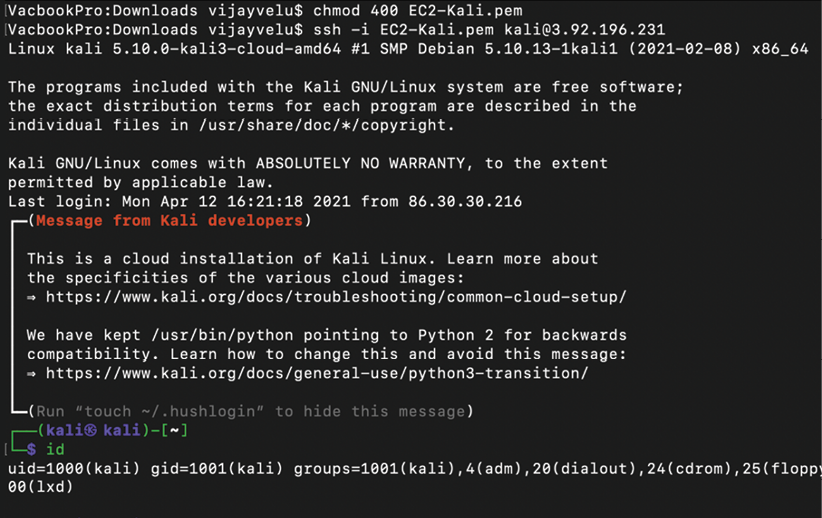
Figure 1.15: Successful connection to a Kali Linux instance in AWS
All of the terms and conditions must be met in order to utilize AWS to perform penetration testing. Legal terms and conditions must be met before launching any attacks from the cloud host.
Kali on Google Cloud Platform (GCP)
There is no version of Kali Linux already available within the Google Cloud Marketplace, unlike AWS. Hence, we will take a different approach to launching Kali Linux on the GCP. Following the same instructions that we used to install Kali in VirtualBox, also use in this instance 12 GB of hard disk space along with 2 GB of RAM. We will utilize our local image to upload to a Google bucket and Compute Engine to run this instance. Before that, we must ensure that once our installation is complete and we log into Kali Linux and start the SSH service to make it persistent, the following commands are run in the Kali Linux VM terminal:
sudo systemctl start ssh
sudo update-rc.d -f ssh enable 2 3 4 5
sudo reboot
For some reason, GCP does not deploy VirtualBox images with the floppy disk enabled, hence we are going to remove the floppy disk by selecting Kali and navigating to Settings, then System, and unselecting Floppy from Boot Order, as shown in Figure 1.16:
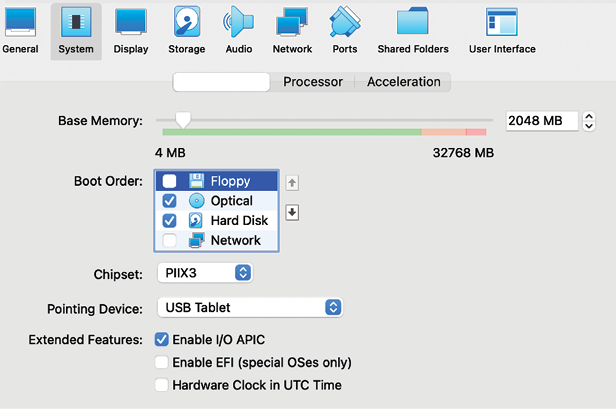
Figure 1.16: With the floppy disk enabled under the Boot Order option, GCP does not deploy VirtualBox images
The next important step involves ensuring that our image is picking up GCP’s network in gathering the DHCP, and getting a public IP address; it is important that we change the network settings by selecting Kali and navigating to Settings, then Network, and clicking on Advanced to change the Adapter Type to Paravirtualized Network, as shown in Figure 1.17:
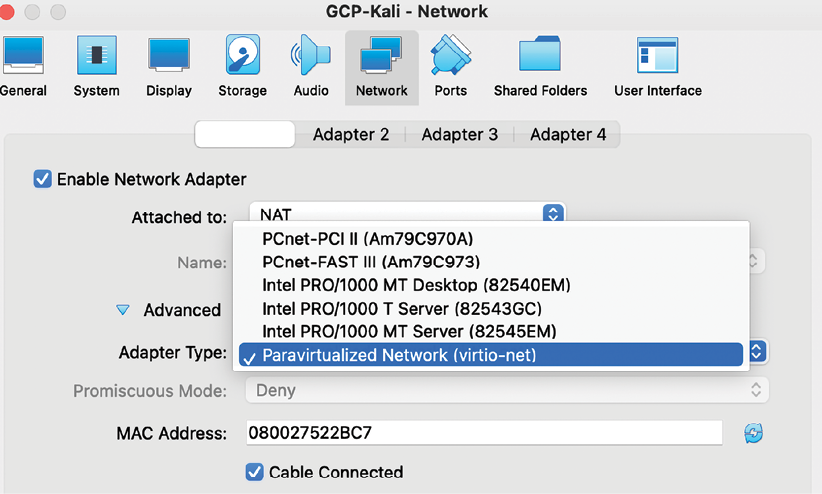
Figure 1.17: Selecting the Paravirtualized Network in VirtualBox
It is also recommended to remove the audio feature to avoid any compatibility issues; select Kali and navigate to Settings, Audio, and uncheck Enable Audio, as shown in Figure 1.18:
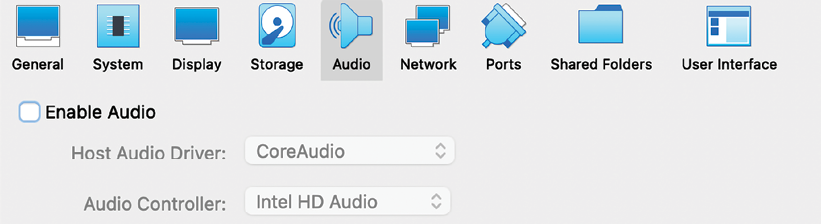
Figure 1.18: With the Enable Audio option selected under the Audio section, GCP may not work properly
Now we must convert the Virtual Disk Image (VDI) into RAW format and apply the naming convention of disk.raw that can then be utilized by Google’s imaging automation software.
We will utilize the generic and open-source machine emulator and virtualizer (QEMU) as the tool to convert either VDI or VMDK files to RAW. In the following steps, we covert the VDI format (similar steps apply for VMDK files):
- Navigate to the VirtualBox location where you have saved the disk images.
- Ensure qemu-img is installed on the native system:
- This can be installed in Windows by downloading the application from https://www.qemu.org/download/#windows
- This can be installed in Linux or macOS systems by running the commands
sudo apt install qemu-imgorbrew install qemu-img
- To convert the image, the following command can be run from the respective Terminal or Command Prompt:
qemu-img convert –f vdi –O raw nameofthevm.vdi disk.raw - Once the
disk.rawfile is created, to reduce the upload size, we will compress the raw disk into thetar.gzformat. However, it is better to usegtarsince Google relies heavily on this utility. For Windows users, these are not natively installed, but the utility can be directly downloaded from http://gnuwin32.sourceforge.net/packages/gtar.htm.You can create the final GCP-compliant image by running the command
gtar –cSzf kali.tar.gz disk.rawon Linux and macOS systems ortar –zcvf kali.tar.gz disk.rawon Windows.
We now have our own image ready to be uploaded to GCP. Create a GCP account or use an existing one to log in to the service. Similar to Microsoft, GCP also provides a free credit option for the user to experience their cloud computing services. The following steps are involved in launching Kali Linux on GCP:
- Log in to https://console.cloud.google.com/.
- Navigate to Cloud Storage and select Brower, and click Create a Bucket.
- Choose a name for the bucket in compliance with GCP’s policy (no capital letters allowed); in our case, we created the bucket name
mastering-kali-linux-edition4. - Click on Upload Files and select our compressed
kali.tar.gzimage that we just created. Once the upload is complete, you should be able to see the same screen displayed in Figure 1.19:
Figure 1.19: After uploading the compressed image to GCP, this screen will be displayed
- Go back to the Home page and select Compute Engine; select Images under the storage and then click on Create Image and enter a name for the image, in this case, we entered
gcp-kali. - Once the name has been entered, for the source, select cloud storage file, click on Bucket, and then select our compressed gz image (
kali.tar.gz). - You can select any region that you want to run in; we selected the default for demonstration purposes. Click Create, which should bring you to the screen displayed in Figure 1.20; if you do not see this, then click on REFRESH on the same screen:

Figure 1.20: The newly created gcp-kali image displaying in the GCP images
- Once the image is created, click on Actions and Create instance, as shown in Figure 1.21:

Figure 1.21: Successful creation of our gcp-kali image that is ready to run as an instance
- This should take us to the VM instance screen to feed the Kali Linux instance information, as shown in Figure 1.22:

Figure 1.22: Entering our gcp-kali instance details and selecting the required resources to run it
- We can now select the CPU (Core Processing Unit) platform and GPU (Graphics Processing Unit); we will select
E2 medium, which will provide two virtual cores of vCPU and 4 GB RAM. Our image includes the storage that we selected during the VM creation (12 GB). - Finally, ensure that the boot disk remains as it is—no changes are required—and finally click Create. This should bring us to the final screen with both the internal and public IP addresses, as shown in Figure 1.23:

Figure 1.23: Successful installation of Kali Linux as an instance in GCP, with an internal and external IP
- We now have successfully created and run an instance of Kali Linux on the GCP, and we can now log in to the public IP with the username and password that we created during the initial creation, as shown in Figure 1.24:

Figure 1.24: Successfully connecting to the Kali Linux instance in GCP externally
























































