Chapter 14. Centralized Authentication Service
In this chapter, we will cover the following recipes:
- Installing OpenLDAP
- Installing phpLDAPadmin
- Ubuntu server logins with LDAP
- Authenticating Ejabberd users with LDAP
Introduction
When you have a large user base using multiple services across the organization, a centralized authentication service becomes a need rather than a luxury. It becomes necessary to quickly add new user accounts across multiple services when a new user comes in, and deactivate the respective access tokens when a user leaves the organization. A centralized authentication service enables you to quickly respond by updating the user database on a single central server.
Various different services are available to set up centralized authentication. In this chapter, we will learn how to set up a centralized authentication service using a Lightweight Directory access Protocol (LDAP). A directory is a special database designed specifically for high volume lookups. LDAP directories are tree-based data structures, also known as Directory Information Trees (DIT). Each node in a tree contains a unique entry with its own set of attributes.
LDAP is specifically designed for high volume read systems with limited write activities. These directories are commonly used for storing details of users with their respective access control lists. Some examples include shared address books, shared calendar services, centralized authentication for systems such as Samba, and storage DNS systems. LDAP provides lightweight access to the directory services over the TCP/IP stack. It is similar to the X.500 OSI directory service, but with limited features and limited resource requirements. For more details on LDAP, check out the OpenLDAP admin guide at http://www.openldap.org/doc/admin24/intro.html.
Installing OpenLDAP
This recipe covers the installation and initial configuration of LDAP. The Ubuntu package repository makes the installation easy by providing the required packages for the LDAP service.
Getting ready
You will need access to a root account or an account with sudo privileges.
How to do it…
Let's start with installing the LDAP package and helper utilities:
- Update your repository using the
apt-get updatecommand and then install the OpenLDAP package,slapd:$ sudo apt-get update $ sudo apt-get install slapd ldap-utils
- You will be asked to enter the admin password and to confirm it.
- The installation process simply installs the package without any configuration. We need to start the actual configuration process with the reconfiguration of the
slapdpackage. Use the following command to start the re-configuration process:$ sudo dpkg-reconfigure slapd - This command will ask you a series of questions including the domain name, admin account, password, database type, and others. Match your answers as follows:
- Omit LDAP server configuration –
NO. - DNS Domain name – Enter your domain name. You can use any domain name. For this setup, I will be using
example.com. This domain name will determine the top structure of your directory: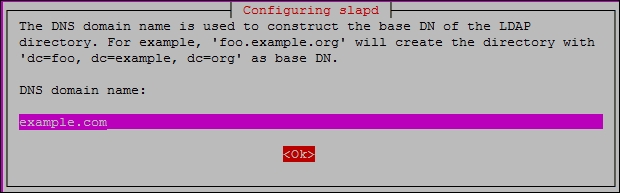
- Organization name – Enter your organization name. I am using
exampleas my organization. - Admin password – Enter a password for the admin account. It can be the same as the one entered during installation, or a totally different one. Make sure you note this password as it will be used to access the admin account.
- Database backend –
HDB
- Remove the database when
slapdis purged - this is about removing the database in case you uninstall theslapdpackage. ChooseNOas you don't want the database to be deleted: - Move old database - YES
- Allow the LDAPv2 protocol - unless you are planning to use some old tools, choose
NO:

- Omit LDAP server configuration –
- Once you have answered all the questions, the process will reconfigure the LDAP service. Now your LDAP service is installed and ready to use:

- Now you can use utility commands to query existing data. To test whether the LDAP service is installed and running properly, use the
ldapsearch -xcommand. You should see output similar to following screenshot:
- Use
ldapsearchas follows to query our newly added domain,example.com:$ ldapsearch -x -LLL -H ldap:/// -b dc=example,dc=com dn
- The following command will query the default content for
example.com:$ ldapsearch -x -LLL -b dc=example,dc=com
The ldap-utils package also provides more commands to configure the LDAP service, but it is quite a lengthy and complex task. In the next recipe, we will learn how to set up a web-based admin interface that make things a little easier.
How it works…
With the respective packages available in the Ubuntu package repository, installing OpenLDAP is quite an easy task. All we have to do is install the required binaries and then configure the LDAP system to serve our desired domain. We have installed two packages: one is slapd, the LDAP daemon, and the other is ldap-utils, which provides various commands to work with the LDAP daemon. After installation is complete, we have re-configured LDAP to match our required directory setup. We have chosen to go with LDAPv3 API and disabled LDAPv2. If you have any older systems working with LDAPv2, then you will need to enable support for old APIs.
See also
- Open LDAP admin guide at http://www.openldap.org/doc/admin24/intro.html
- Ubuntu OpenLDAP guide at https://help.ubuntu.com/lts/serverguide/openldap-server.html
- LDAP protocol RFC at http://www.rfc-editor.org/rfc/rfc2251.txt
- LDAP protocol technical details at http://www.rfc-editor.org/rfc/rfc3377.txt
- Get more help with LDAP configuration using the
man ldap.confcommand.
Getting ready
You will need access to a root account or an account with sudo privileges.
How to do it…
Let's start with installing the LDAP package and helper utilities:
- Update your repository using the
apt-get updatecommand and then install the OpenLDAP package,slapd:$ sudo apt-get update $ sudo apt-get install slapd ldap-utils
- You will be asked to enter the admin password and to confirm it.
- The installation process simply installs the package without any configuration. We need to start the actual configuration process with the reconfiguration of the
slapdpackage. Use the following command to start the re-configuration process:$ sudo dpkg-reconfigure slapd - This command will ask you a series of questions including the domain name, admin account, password, database type, and others. Match your answers as follows:
- Omit LDAP server configuration –
NO. - DNS Domain name – Enter your domain name. You can use any domain name. For this setup, I will be using
example.com. This domain name will determine the top structure of your directory:
- Organization name – Enter your organization name. I am using
exampleas my organization. - Admin password – Enter a password for the admin account. It can be the same as the one entered during installation, or a totally different one. Make sure you note this password as it will be used to access the admin account.
- Database backend –
HDB
- Remove the database when
slapdis purged - this is about removing the database in case you uninstall theslapdpackage. ChooseNOas you don't want the database to be deleted: - Move old database - YES
- Allow the LDAPv2 protocol - unless you are planning to use some old tools, choose
NO:

- Omit LDAP server configuration –
- Once you have answered all the questions, the process will reconfigure the LDAP service. Now your LDAP service is installed and ready to use:

- Now you can use utility commands to query existing data. To test whether the LDAP service is installed and running properly, use the
ldapsearch -xcommand. You should see output similar to following screenshot:
- Use
ldapsearchas follows to query our newly added domain,example.com:$ ldapsearch -x -LLL -H ldap:/// -b dc=example,dc=com dn
- The following command will query the default content for
example.com:$ ldapsearch -x -LLL -b dc=example,dc=com
The ldap-utils package also provides more commands to configure the LDAP service, but it is quite a lengthy and complex task. In the next recipe, we will learn how to set up a web-based admin interface that make things a little easier.
How it works…
With the respective packages available in the Ubuntu package repository, installing OpenLDAP is quite an easy task. All we have to do is install the required binaries and then configure the LDAP system to serve our desired domain. We have installed two packages: one is slapd, the LDAP daemon, and the other is ldap-utils, which provides various commands to work with the LDAP daemon. After installation is complete, we have re-configured LDAP to match our required directory setup. We have chosen to go with LDAPv3 API and disabled LDAPv2. If you have any older systems working with LDAPv2, then you will need to enable support for old APIs.
See also
- Open LDAP admin guide at http://www.openldap.org/doc/admin24/intro.html
- Ubuntu OpenLDAP guide at https://help.ubuntu.com/lts/serverguide/openldap-server.html
- LDAP protocol RFC at http://www.rfc-editor.org/rfc/rfc2251.txt
- LDAP protocol technical details at http://www.rfc-editor.org/rfc/rfc3377.txt
- Get more help with LDAP configuration using the
man ldap.confcommand.
How to do it…
Let's start with installing the LDAP package and helper utilities:
- Update your repository using the
apt-get updatecommand and then install the OpenLDAP package,slapd:$ sudo apt-get update $ sudo apt-get install slapd ldap-utils
- You will be asked to enter the admin password and to confirm it.
- The installation process simply installs the package without any configuration. We need to start the actual configuration process with the reconfiguration of the
slapdpackage. Use the following command to start the re-configuration process:$ sudo dpkg-reconfigure slapd - This command will ask you a series of questions including the domain name, admin account, password, database type, and others. Match your answers as follows:
- Omit LDAP server configuration –
NO. - DNS Domain name – Enter your domain name. You can use any domain name. For this setup, I will be using
example.com. This domain name will determine the top structure of your directory:
- Organization name – Enter your organization name. I am using
exampleas my organization. - Admin password – Enter a password for the admin account. It can be the same as the one entered during installation, or a totally different one. Make sure you note this password as it will be used to access the admin account.
- Database backend –
HDB
- Remove the database when
slapdis purged - this is about removing the database in case you uninstall theslapdpackage. ChooseNOas you don't want the database to be deleted: - Move old database - YES
- Allow the LDAPv2 protocol - unless you are planning to use some old tools, choose
NO:

- Omit LDAP server configuration –
- Once you have answered all the questions, the process will reconfigure the LDAP service. Now your LDAP service is installed and ready to use:

- Now you can use utility commands to query existing data. To test whether the LDAP service is installed and running properly, use the
ldapsearch -xcommand. You should see output similar to following screenshot:
- Use
ldapsearchas follows to query our newly added domain,example.com:$ ldapsearch -x -LLL -H ldap:/// -b dc=example,dc=com dn
- The following command will query the default content for
example.com:$ ldapsearch -x -LLL -b dc=example,dc=com
The ldap-utils package also provides more commands to configure the LDAP service, but it is quite a lengthy and complex task. In the next recipe, we will learn how to set up a web-based admin interface that make things a little easier.
How it works…
With the respective packages available in the Ubuntu package repository, installing OpenLDAP is quite an easy task. All we have to do is install the required binaries and then configure the LDAP system to serve our desired domain. We have installed two packages: one is slapd, the LDAP daemon, and the other is ldap-utils, which provides various commands to work with the LDAP daemon. After installation is complete, we have re-configured LDAP to match our required directory setup. We have chosen to go with LDAPv3 API and disabled LDAPv2. If you have any older systems working with LDAPv2, then you will need to enable support for old APIs.
See also
- Open LDAP admin guide at http://www.openldap.org/doc/admin24/intro.html
- Ubuntu OpenLDAP guide at https://help.ubuntu.com/lts/serverguide/openldap-server.html
- LDAP protocol RFC at http://www.rfc-editor.org/rfc/rfc2251.txt
- LDAP protocol technical details at http://www.rfc-editor.org/rfc/rfc3377.txt
- Get more help with LDAP configuration using the
man ldap.confcommand.
How it works…
With the respective packages available in the Ubuntu package repository, installing OpenLDAP is quite an easy task. All we have to do is install the required binaries and then configure the LDAP system to serve our desired domain. We have installed two packages: one is slapd, the LDAP daemon, and the other is ldap-utils, which provides various commands to work with the LDAP daemon. After installation is complete, we have re-configured LDAP to match our required directory setup. We have chosen to go with LDAPv3 API and disabled LDAPv2. If you have any older systems working with LDAPv2, then you will need to enable support for old APIs.
See also
- Open LDAP admin guide at http://www.openldap.org/doc/admin24/intro.html
- Ubuntu OpenLDAP guide at https://help.ubuntu.com/lts/serverguide/openldap-server.html
- LDAP protocol RFC at http://www.rfc-editor.org/rfc/rfc2251.txt
- LDAP protocol technical details at http://www.rfc-editor.org/rfc/rfc3377.txt
- Get more help with LDAP configuration using the
man ldap.confcommand.
See also
- Open LDAP admin guide at http://www.openldap.org/doc/admin24/intro.html
- Ubuntu OpenLDAP guide at https://help.ubuntu.com/lts/serverguide/openldap-server.html
- LDAP protocol RFC at http://www.rfc-editor.org/rfc/rfc2251.txt
- LDAP protocol technical details at http://www.rfc-editor.org/rfc/rfc3377.txt
- Get more help with LDAP configuration using the
man ldap.confcommand.
Installing phpLDAPadmin
In the previous recipe, we installed the LDAP service, but working with LDAP using the command line interface is quite a complex and lengthy task. This recipe covers the installation of a user interface, phpLDAPadmin. The phpldapadmin package provides an easy-to-use web-based user interface for the LDAP service.
Getting ready
Make sure that you have the LDAP service installed and running.
How to do it…
Follow these steps to install phpLDAPadmin:
- The Ubuntu package repository makes things easy again by providing the package for phpLDAPadmin. The web interface can be quickly installed in a single command as follows:
$ sudo apt-get install phpldapadmin - The installation process takes care of installing all dependencies including PHP and the Apache web server. It also creates necessary configurations and sets up Apache with the required settings for phpLDAPadmin. Once installation is complete, you can access the admin interface at
http://youServerIP/phpldapadmin. - Before we access the admin page, let's make some small changes in the configuration file. The file is located at
/etc/phpldapadmin/config.php. By default, phpLDAPadmin shows warning messages for unused template files. These warning messages get shown in the main interface before the actual content. To hide them, search forhide_template_warningin the configuration file and set it totrue. You will also need to uncomment the same line:$config->custom->appearance['hide_template_warning'] = true; - The other settings should have already been set by the installation process. You can cross-check the following settings:
$servers->setValue('server','host','127.0.0.1'); $servers->setValue( 'login','bind_id', 'cn=admin,dc=example, dc=com' ); $servers->setValue( 'server','base',array('dc=example,dc=com') );
- Once you are done with the configuration file changes, save and close it and then access the admin interface through your browser:

- Click on the login link on the left of the page to get the login dialogue box. The username (Login DN) field is already filled with details for the admin account. Make sure the details match the domain you have set up. Enter the password for the admin account and click the Authenticate button:

Note
You can also log in as an anonymous user. In the login box, do not enter a password, click to check the Anonymous checkbox, and then click the Authenticate button. This gives you a read-only view, which is quite useful when you just need to verify some details.
- You should have noticed the warning on the login box saying the
connection is unencrypted. This is just a reminder that you are using the admin console over a non-HTTPs connection. You can set up Apache with SSL certificates to get an encrypted, secure connection with your LDAP server. Check Chapter 3, Working with Web Servers, for more details on how to set up SSL certificates on the Apache web server. - Once you log in to phpLDAPadmin, you can see the domain listed in the left-hand side menu. Click on the domain link to view its details.
- Next, click on the small plus link (+) to expand the domain link and see its children. With the default settings, it should show only the admin account:

- Along with the link for the admin account, you will see an option to create a new entry. Clicking on this link will show you a list of templates for the new entry:

Note
While clicking on some of these templates, for example Generic: User Account, you may notice a PHP error saying Error trying to get non-existent value. The form rendering fails and you cannot see the complete form the with submit button. This is a small bug and can be fixed with a small edit.
Open /usr/share/phpldapadmin/lib/TemplateRender.php.
Search for the following line:
$default = $this->getServer() ->getValue('appearance','password_hash');
Now update the preceding command as follows:
$default = $this->getServer() ->getValue('appearance','password_hash_custom');
Now you are ready to create groups and respective user accounts on your LDAP server.
How it works…
In this recipe, we have installed a web-based administration console for the LDAP server. The ldap-utils package provides various commands to work with the LDAP server, but it is quite a complex and lengthy task. A graphical user interface gives you a better listing of all options and existing configurations, making things a little easier.
The phpLDAPadmin package is a PHP/Apache-based web application that provides a graphical interface for the LDAP server. It displays all options and configurations in an easy-to-use graphical format and passes all user actions to LDAP APIs.
There's more…
Apache directory studio is another user interface for LDAP administration. It is a desktop application based on Java. You can get more details at https://directory.apache.org/studio/.
See also
- A StackOverflow answer for the phpLDAPadmin error message at http://stackoverflow.com/a/21195761/1012809
Getting ready
Make sure that you have the LDAP service installed and running.
How to do it…
Follow these steps to install phpLDAPadmin:
- The Ubuntu package repository makes things easy again by providing the package for phpLDAPadmin. The web interface can be quickly installed in a single command as follows:
$ sudo apt-get install phpldapadmin - The installation process takes care of installing all dependencies including PHP and the Apache web server. It also creates necessary configurations and sets up Apache with the required settings for phpLDAPadmin. Once installation is complete, you can access the admin interface at
http://youServerIP/phpldapadmin. - Before we access the admin page, let's make some small changes in the configuration file. The file is located at
/etc/phpldapadmin/config.php. By default, phpLDAPadmin shows warning messages for unused template files. These warning messages get shown in the main interface before the actual content. To hide them, search forhide_template_warningin the configuration file and set it totrue. You will also need to uncomment the same line:$config->custom->appearance['hide_template_warning'] = true; - The other settings should have already been set by the installation process. You can cross-check the following settings:
$servers->setValue('server','host','127.0.0.1'); $servers->setValue( 'login','bind_id', 'cn=admin,dc=example, dc=com' ); $servers->setValue( 'server','base',array('dc=example,dc=com') );
- Once you are done with the configuration file changes, save and close it and then access the admin interface through your browser:

- Click on the login link on the left of the page to get the login dialogue box. The username (Login DN) field is already filled with details for the admin account. Make sure the details match the domain you have set up. Enter the password for the admin account and click the Authenticate button:

Note
You can also log in as an anonymous user. In the login box, do not enter a password, click to check the Anonymous checkbox, and then click the Authenticate button. This gives you a read-only view, which is quite useful when you just need to verify some details.
- You should have noticed the warning on the login box saying the
connection is unencrypted. This is just a reminder that you are using the admin console over a non-HTTPs connection. You can set up Apache with SSL certificates to get an encrypted, secure connection with your LDAP server. Check Chapter 3, Working with Web Servers, for more details on how to set up SSL certificates on the Apache web server. - Once you log in to phpLDAPadmin, you can see the domain listed in the left-hand side menu. Click on the domain link to view its details.
- Next, click on the small plus link (+) to expand the domain link and see its children. With the default settings, it should show only the admin account:

- Along with the link for the admin account, you will see an option to create a new entry. Clicking on this link will show you a list of templates for the new entry:

Note
While clicking on some of these templates, for example Generic: User Account, you may notice a PHP error saying Error trying to get non-existent value. The form rendering fails and you cannot see the complete form the with submit button. This is a small bug and can be fixed with a small edit.
Open /usr/share/phpldapadmin/lib/TemplateRender.php.
Search for the following line:
$default = $this->getServer() ->getValue('appearance','password_hash');
Now update the preceding command as follows:
$default = $this->getServer() ->getValue('appearance','password_hash_custom');
Now you are ready to create groups and respective user accounts on your LDAP server.
How it works…
In this recipe, we have installed a web-based administration console for the LDAP server. The ldap-utils package provides various commands to work with the LDAP server, but it is quite a complex and lengthy task. A graphical user interface gives you a better listing of all options and existing configurations, making things a little easier.
The phpLDAPadmin package is a PHP/Apache-based web application that provides a graphical interface for the LDAP server. It displays all options and configurations in an easy-to-use graphical format and passes all user actions to LDAP APIs.
There's more…
Apache directory studio is another user interface for LDAP administration. It is a desktop application based on Java. You can get more details at https://directory.apache.org/studio/.
See also
- A StackOverflow answer for the phpLDAPadmin error message at http://stackoverflow.com/a/21195761/1012809
How to do it…
Follow these steps to install phpLDAPadmin:
- The Ubuntu package repository makes things easy again by providing the package for phpLDAPadmin. The web interface can be quickly installed in a single command as follows:
$ sudo apt-get install phpldapadmin - The installation process takes care of installing all dependencies including PHP and the Apache web server. It also creates necessary configurations and sets up Apache with the required settings for phpLDAPadmin. Once installation is complete, you can access the admin interface at
http://youServerIP/phpldapadmin. - Before we access the admin page, let's make some small changes in the configuration file. The file is located at
/etc/phpldapadmin/config.php. By default, phpLDAPadmin shows warning messages for unused template files. These warning messages get shown in the main interface before the actual content. To hide them, search forhide_template_warningin the configuration file and set it totrue. You will also need to uncomment the same line:$config->custom->appearance['hide_template_warning'] = true; - The other settings should have already been set by the installation process. You can cross-check the following settings:
$servers->setValue('server','host','127.0.0.1'); $servers->setValue( 'login','bind_id', 'cn=admin,dc=example, dc=com' ); $servers->setValue( 'server','base',array('dc=example,dc=com') );
- Once you are done with the configuration file changes, save and close it and then access the admin interface through your browser:

- Click on the login link on the left of the page to get the login dialogue box. The username (Login DN) field is already filled with details for the admin account. Make sure the details match the domain you have set up. Enter the password for the admin account and click the Authenticate button:

Note
You can also log in as an anonymous user. In the login box, do not enter a password, click to check the Anonymous checkbox, and then click the Authenticate button. This gives you a read-only view, which is quite useful when you just need to verify some details.
- You should have noticed the warning on the login box saying the
connection is unencrypted. This is just a reminder that you are using the admin console over a non-HTTPs connection. You can set up Apache with SSL certificates to get an encrypted, secure connection with your LDAP server. Check Chapter 3, Working with Web Servers, for more details on how to set up SSL certificates on the Apache web server. - Once you log in to phpLDAPadmin, you can see the domain listed in the left-hand side menu. Click on the domain link to view its details.
- Next, click on the small plus link (+) to expand the domain link and see its children. With the default settings, it should show only the admin account:

- Along with the link for the admin account, you will see an option to create a new entry. Clicking on this link will show you a list of templates for the new entry:

Note
While clicking on some of these templates, for example Generic: User Account, you may notice a PHP error saying Error trying to get non-existent value. The form rendering fails and you cannot see the complete form the with submit button. This is a small bug and can be fixed with a small edit.
Open /usr/share/phpldapadmin/lib/TemplateRender.php.
Search for the following line:
$default = $this->getServer() ->getValue('appearance','password_hash');
Now update the preceding command as follows:
$default = $this->getServer() ->getValue('appearance','password_hash_custom');
Now you are ready to create groups and respective user accounts on your LDAP server.
How it works…
In this recipe, we have installed a web-based administration console for the LDAP server. The ldap-utils package provides various commands to work with the LDAP server, but it is quite a complex and lengthy task. A graphical user interface gives you a better listing of all options and existing configurations, making things a little easier.
The phpLDAPadmin package is a PHP/Apache-based web application that provides a graphical interface for the LDAP server. It displays all options and configurations in an easy-to-use graphical format and passes all user actions to LDAP APIs.
There's more…
Apache directory studio is another user interface for LDAP administration. It is a desktop application based on Java. You can get more details at https://directory.apache.org/studio/.
See also
- A StackOverflow answer for the phpLDAPadmin error message at http://stackoverflow.com/a/21195761/1012809
How it works…
In this recipe, we have installed a web-based administration console for the LDAP server. The ldap-utils package provides various commands to work with the LDAP server, but it is quite a complex and lengthy task. A graphical user interface gives you a better listing of all options and existing configurations, making things a little easier.
The phpLDAPadmin package is a PHP/Apache-based web application that provides a graphical interface for the LDAP server. It displays all options and configurations in an easy-to-use graphical format and passes all user actions to LDAP APIs.
There's more…
Apache directory studio is another user interface for LDAP administration. It is a desktop application based on Java. You can get more details at https://directory.apache.org/studio/.
See also
- A StackOverflow answer for the phpLDAPadmin error message at http://stackoverflow.com/a/21195761/1012809
There's more…
Apache directory studio is another user interface for LDAP administration. It is a desktop application based on Java. You can get more details at https://directory.apache.org/studio/.
See also
- A StackOverflow answer for the phpLDAPadmin error message at http://stackoverflow.com/a/21195761/1012809
See also
- A StackOverflow answer for the phpLDAPadmin error message at http://stackoverflow.com/a/21195761/1012809
Ubuntu server logins with LDAP
So, we have installed and configured our own centralized auth server with LDAP. Now is the time to use LDAP to authenticate client logins. In this recipe, we will set up a separate Ubuntu server to use our LDAP server for authenticating users.
Getting ready
You will need a new Ubuntu server to be set as an LDAP client. Also, sudo privileges are needed for the initial setup.
Make sure you have followed the previous recipes and have set up your LDAP server.
How to do it…
- We will need to install the LDAP client-side package on the client system. This package will install all the required tools to authenticate with the remote LDAP server:
$ sudo apt-get update $ sudo apt-get install ldap-auth-client nscd
- The installation process will ask you some questions regarding your LDAP server and its authentication details. Answer those questions as follows:
LDAP server URI:ldap://you-LDAP-server-IP:Make sure you change the protocol line fromldapi:///toldap://Distinguished name of search base: Match this to the domain set on the LDAP server in the formatdc=example,dc=comLDAP version to use:3Make local root database admin:YesDoes LDAP database require login:NoLDAP account for root:cn=admin,dc=example,dc=comLDAP root account password: The password for the LDAP admin account
- Next, we need to change the authentication configuration to check with the LDAP server. First, run the following command to set the name service switch file
/etc/nsswitch.conf:$ sudo auth-client-config -t nss -p lac_ldap - This will change
/etc/nsswitch.confas follows:
- Next, add the following line to
/etc/pam.d/common-session. This will create a local home directory for LDAP users. Edit thecommon-sessionfile and add the following line at the end of the file:session required pam_mkhomedir.so umask=0022 skel=/etc/skel - Now restart the
nscdservice with the following command:$ sudo /etc/init.d/nscd restartNow you should be able to log in with the user account created on your LDAP server. I have set up an Organizational Unit (OU) named users and created an admin user under it:

- Next, change the login to the newly created LDAP user account with the
su usernamecommand. You will need to enter a password that is configured on LDAP server. As this is a first-time login for this new user, our PAM settings have created a newhomedirectory for him:
This new user is a member of the admin group on the LDAP server, so he will get sudo privileges on the local server as well.
You can always use a default login prompt to log in with LDAP users, as well as local user accounts that already exist on the server.
How it works…
Here we have configured the Ubuntu server to authenticate with our centralized LDAP system. This is not limited to the Ubuntu server and you can configure the Ubuntu desktop in a similar way as well. Using a centralized authentication makes it easy to administer hundreds of user accounts from a single place. A user can still log in as a local user if he has any local credentials.
Using centralized authentication enables you to log in from any system. You will get the same access rights and permissions from any terminal. Additionally, if the LDAP configuration supports roaming profiles then all your data will be replicated to any new system you log in from. You may have noticed the home directory for the LDAP user account is located in the /home/users directory and not in /home. This separates your account from any local users.
Finally, the groups and roles configured on the LDAP server also apply on the system you are logging in from. So, if the user is assigned admin rights on the LDAP server, he will get admin rights, including sudo privileges, on the system he is logged in from. This is because Ubuntu contains a default group named admin with sudo privileges. When a user logs in with his LDAP account, the groups and roles assigned to his LDAP account are matched with local groups and roles. You can either disable such groups from any remote systems, or set the proper access rights on the LDAP server itself.
See also
- The Ubuntu community page for LDAP client authentication at https://help.ubuntu.com/community/LDAPClientAuthentication
Getting ready
You will need a new Ubuntu server to be set as an LDAP client. Also, sudo privileges are needed for the initial setup.
Make sure you have followed the previous recipes and have set up your LDAP server.
How to do it…
- We will need to install the LDAP client-side package on the client system. This package will install all the required tools to authenticate with the remote LDAP server:
$ sudo apt-get update $ sudo apt-get install ldap-auth-client nscd
- The installation process will ask you some questions regarding your LDAP server and its authentication details. Answer those questions as follows:
LDAP server URI:ldap://you-LDAP-server-IP:Make sure you change the protocol line fromldapi:///toldap://Distinguished name of search base: Match this to the domain set on the LDAP server in the formatdc=example,dc=comLDAP version to use:3Make local root database admin:YesDoes LDAP database require login:NoLDAP account for root:cn=admin,dc=example,dc=comLDAP root account password: The password for the LDAP admin account
- Next, we need to change the authentication configuration to check with the LDAP server. First, run the following command to set the name service switch file
/etc/nsswitch.conf:$ sudo auth-client-config -t nss -p lac_ldap - This will change
/etc/nsswitch.confas follows:
- Next, add the following line to
/etc/pam.d/common-session. This will create a local home directory for LDAP users. Edit thecommon-sessionfile and add the following line at the end of the file:session required pam_mkhomedir.so umask=0022 skel=/etc/skel - Now restart the
nscdservice with the following command:$ sudo /etc/init.d/nscd restartNow you should be able to log in with the user account created on your LDAP server. I have set up an Organizational Unit (OU) named users and created an admin user under it:

- Next, change the login to the newly created LDAP user account with the
su usernamecommand. You will need to enter a password that is configured on LDAP server. As this is a first-time login for this new user, our PAM settings have created a newhomedirectory for him:
This new user is a member of the admin group on the LDAP server, so he will get sudo privileges on the local server as well.
You can always use a default login prompt to log in with LDAP users, as well as local user accounts that already exist on the server.
How it works…
Here we have configured the Ubuntu server to authenticate with our centralized LDAP system. This is not limited to the Ubuntu server and you can configure the Ubuntu desktop in a similar way as well. Using a centralized authentication makes it easy to administer hundreds of user accounts from a single place. A user can still log in as a local user if he has any local credentials.
Using centralized authentication enables you to log in from any system. You will get the same access rights and permissions from any terminal. Additionally, if the LDAP configuration supports roaming profiles then all your data will be replicated to any new system you log in from. You may have noticed the home directory for the LDAP user account is located in the /home/users directory and not in /home. This separates your account from any local users.
Finally, the groups and roles configured on the LDAP server also apply on the system you are logging in from. So, if the user is assigned admin rights on the LDAP server, he will get admin rights, including sudo privileges, on the system he is logged in from. This is because Ubuntu contains a default group named admin with sudo privileges. When a user logs in with his LDAP account, the groups and roles assigned to his LDAP account are matched with local groups and roles. You can either disable such groups from any remote systems, or set the proper access rights on the LDAP server itself.
See also
- The Ubuntu community page for LDAP client authentication at https://help.ubuntu.com/community/LDAPClientAuthentication
How to do it…
- We will need to install the LDAP client-side package on the client system. This package will install all the required tools to authenticate with the remote LDAP server:
$ sudo apt-get update $ sudo apt-get install ldap-auth-client nscd
- The installation process will ask you some questions regarding your LDAP server and its authentication details. Answer those questions as follows:
LDAP server URI:ldap://you-LDAP-server-IP:Make sure you change the protocol line fromldapi:///toldap://Distinguished name of search base: Match this to the domain set on the LDAP server in the formatdc=example,dc=comLDAP version to use:3Make local root database admin:YesDoes LDAP database require login:NoLDAP account for root:cn=admin,dc=example,dc=comLDAP root account password: The password for the LDAP admin account
- Next, we need to change the authentication configuration to check with the LDAP server. First, run the following command to set the name service switch file
/etc/nsswitch.conf:$ sudo auth-client-config -t nss -p lac_ldap - This will change
/etc/nsswitch.confas follows:
- Next, add the following line to
/etc/pam.d/common-session. This will create a local home directory for LDAP users. Edit thecommon-sessionfile and add the following line at the end of the file:session required pam_mkhomedir.so umask=0022 skel=/etc/skel - Now restart the
nscdservice with the following command:$ sudo /etc/init.d/nscd restartNow you should be able to log in with the user account created on your LDAP server. I have set up an Organizational Unit (OU) named users and created an admin user under it:

- Next, change the login to the newly created LDAP user account with the
su usernamecommand. You will need to enter a password that is configured on LDAP server. As this is a first-time login for this new user, our PAM settings have created a newhomedirectory for him:
This new user is a member of the admin group on the LDAP server, so he will get sudo privileges on the local server as well.
You can always use a default login prompt to log in with LDAP users, as well as local user accounts that already exist on the server.
How it works…
Here we have configured the Ubuntu server to authenticate with our centralized LDAP system. This is not limited to the Ubuntu server and you can configure the Ubuntu desktop in a similar way as well. Using a centralized authentication makes it easy to administer hundreds of user accounts from a single place. A user can still log in as a local user if he has any local credentials.
Using centralized authentication enables you to log in from any system. You will get the same access rights and permissions from any terminal. Additionally, if the LDAP configuration supports roaming profiles then all your data will be replicated to any new system you log in from. You may have noticed the home directory for the LDAP user account is located in the /home/users directory and not in /home. This separates your account from any local users.
Finally, the groups and roles configured on the LDAP server also apply on the system you are logging in from. So, if the user is assigned admin rights on the LDAP server, he will get admin rights, including sudo privileges, on the system he is logged in from. This is because Ubuntu contains a default group named admin with sudo privileges. When a user logs in with his LDAP account, the groups and roles assigned to his LDAP account are matched with local groups and roles. You can either disable such groups from any remote systems, or set the proper access rights on the LDAP server itself.
See also
- The Ubuntu community page for LDAP client authentication at https://help.ubuntu.com/community/LDAPClientAuthentication
How it works…
Here we have configured the Ubuntu server to authenticate with our centralized LDAP system. This is not limited to the Ubuntu server and you can configure the Ubuntu desktop in a similar way as well. Using a centralized authentication makes it easy to administer hundreds of user accounts from a single place. A user can still log in as a local user if he has any local credentials.
Using centralized authentication enables you to log in from any system. You will get the same access rights and permissions from any terminal. Additionally, if the LDAP configuration supports roaming profiles then all your data will be replicated to any new system you log in from. You may have noticed the home directory for the LDAP user account is located in the /home/users directory and not in /home. This separates your account from any local users.
Finally, the groups and roles configured on the LDAP server also apply on the system you are logging in from. So, if the user is assigned admin rights on the LDAP server, he will get admin rights, including sudo privileges, on the system he is logged in from. This is because Ubuntu contains a default group named admin with sudo privileges. When a user logs in with his LDAP account, the groups and roles assigned to his LDAP account are matched with local groups and roles. You can either disable such groups from any remote systems, or set the proper access rights on the LDAP server itself.
See also
- The Ubuntu community page for LDAP client authentication at https://help.ubuntu.com/community/LDAPClientAuthentication
See also
- The Ubuntu community page for LDAP client authentication at https://help.ubuntu.com/community/LDAPClientAuthentication
Authenticating Ejabberd users with LDAP
In this recipe, we will learn to set up the Ejabberd server to authenticate the user with our LDAP server. Until now, we have set up the LDAP server and used it to log in to the Ubuntu server with a user account created on the LDAP server. This recipe covers the configuration of an external service to work with our LDAP installation.
The Ejabberd server provides built-in support for LDAP-based authentication. You can use LDAP for user authentication as well as vCard storage. As stated in the Ejabberd admin guide, Ejabberd use LDAP as a read-only data source. We cannot create new user accounts in the LDAP directory, but we can change passwords if the mod_register module is enabled.
Getting ready
You will need the Ejabberd service installed and running. Go through Chapter 10, Communication Server with XMPP, for details on the installation and configuration of the Ejabberd server.
Create a user account on the LDAP server to be used with Ejabberd.
How to do it…
As Ejabberd provides inbuilt support for LDAP-based authentication, we simply need to edit configurations and set the auth method to LDAP. If you have used a Debian package for the Ejabberd installation, your Ejabberd should be installed in /opt/ejabberd-version directory and the configuration can be found at /etc/ejabberd-version/conf. If you have installed Ejabberd from source, all configuration files are located in the /etc/ejabberd directory:
- Open
ejabberd.ymlfrom your Ejabberd configuration directory and search for Authentication. With the default settings, it should contain the following line indicating internal authentication:auth_method: internal
- Comment out that line by changing it as follows:
## auth_method: internal
- Next, find Authentication using LDAP. This section contains a few parameters and configures communication with the LDAP server. Search and update the following parameters:
ldap_servers: - "domain/IP of LDAP server" ldap_port: 389 ldap_rootdn: "cn=admin,dc=example,dc=com" ldap_password: "password" ldap_base: "ou=ejabberd,dc=example,dc=com"
I have used a default admin account to authenticate with the LDAP server itself. In a production environment, you should change it to a different account. With a default LDAP setup, you can skip the
ldap_rootdnandldap_passwordsettings to enable anonymous connection. - Next, under the
ldap_baseparameter, I have restricted users to the Organizational Unit namedEjabberd. Only the user accounts that are configured under theEjabberdunit can log in with the Ejabberd server. - Now, save the configuration file changes and close the file, and then restart the Ejabberd server with the following command:
$ sudo /opt/ejabberd-version/bin/ejabberdctl restart - If the server fails to restart, check the log files for any configuration errors. Alternatively, you can use the
reload_configoption toejabberdctlto update the in-memory configuration without restarting:$ sudo /opt/ejabberd-version/bin/ejabberdctl reload_config - Once the server has started, you can log in with your LDAP accounts. You will need a JID to log in with Ejabberd, which is a combination of a UID from the LDAP server and any host configured on Ejabberd, for instance,
uday@cookbook.com, whereudayis the UID on LDAP andcookbook.comis the host served by Ejabberd server. The domain entries on the LDAP server and Ejabberd need not match.The following is the default host entry for my Ejabberd installation:

- Now you can log in to Ejabberd with your LDAP username. Here is the account set up in my chat client with the JID
uday@ubuntu, whereudayis my LDAP user andubuntuis the Ejabberd host:
Once all things are set up, you should be able to connect to the Ejabberd server using your LDAP user account.
How it works…
Here, we have set up Ejabberd as an example of LDAP-based authentication. Similar to Ejabberd, various other systems support centralized authentication through LDAP with either built-in support or with a plug-in module. Make sure that you create a proper directory structure with organizational units, roles, and separate users in proper groups. Also use a separate user account for authenticating with the LDAP server itself. You need to set the respective LDAP credentials in the Ejabberd configuration file. If somehow your Ejabberd server gets compromised, then the LDAP server credentials are readily available to an attacker. To limit the risk, using separate and limited accounts is a good idea. Ejabberd also supports anonymous authentication with the LDAP server and mostly uses it as a read-only database. So, even if you skip the authentication details (depending on the LDAP configuration), Ejabberd should work well and authenticate your users.
Ejabberd also provides good enough debug logging, where you can see the actual communication with the LDAP server. You will need to set logging to debug mode in the Ejabberd configuration. The log files are located in the /opt/ejabberd-version/logs directory or the /var/log/ejabberd directory, depending on the source of the Ejabberd installation.
See also
- Ejabberd docs LDAP section at https://www.process-one.net/docs/ejabberd/guide_en.html#ldap
Getting ready
You will need the Ejabberd service installed and running. Go through Chapter 10, Communication Server with XMPP, for details on the installation and configuration of the Ejabberd server.
Create a user account on the LDAP server to be used with Ejabberd.
How to do it…
As Ejabberd provides inbuilt support for LDAP-based authentication, we simply need to edit configurations and set the auth method to LDAP. If you have used a Debian package for the Ejabberd installation, your Ejabberd should be installed in /opt/ejabberd-version directory and the configuration can be found at /etc/ejabberd-version/conf. If you have installed Ejabberd from source, all configuration files are located in the /etc/ejabberd directory:
- Open
ejabberd.ymlfrom your Ejabberd configuration directory and search for Authentication. With the default settings, it should contain the following line indicating internal authentication:auth_method: internal
- Comment out that line by changing it as follows:
## auth_method: internal
- Next, find Authentication using LDAP. This section contains a few parameters and configures communication with the LDAP server. Search and update the following parameters:
ldap_servers: - "domain/IP of LDAP server" ldap_port: 389 ldap_rootdn: "cn=admin,dc=example,dc=com" ldap_password: "password" ldap_base: "ou=ejabberd,dc=example,dc=com"
I have used a default admin account to authenticate with the LDAP server itself. In a production environment, you should change it to a different account. With a default LDAP setup, you can skip the
ldap_rootdnandldap_passwordsettings to enable anonymous connection. - Next, under the
ldap_baseparameter, I have restricted users to the Organizational Unit namedEjabberd. Only the user accounts that are configured under theEjabberdunit can log in with the Ejabberd server. - Now, save the configuration file changes and close the file, and then restart the Ejabberd server with the following command:
$ sudo /opt/ejabberd-version/bin/ejabberdctl restart - If the server fails to restart, check the log files for any configuration errors. Alternatively, you can use the
reload_configoption toejabberdctlto update the in-memory configuration without restarting:$ sudo /opt/ejabberd-version/bin/ejabberdctl reload_config - Once the server has started, you can log in with your LDAP accounts. You will need a JID to log in with Ejabberd, which is a combination of a UID from the LDAP server and any host configured on Ejabberd, for instance,
uday@cookbook.com, whereudayis the UID on LDAP andcookbook.comis the host served by Ejabberd server. The domain entries on the LDAP server and Ejabberd need not match.The following is the default host entry for my Ejabberd installation:

- Now you can log in to Ejabberd with your LDAP username. Here is the account set up in my chat client with the JID
uday@ubuntu, whereudayis my LDAP user andubuntuis the Ejabberd host:
Once all things are set up, you should be able to connect to the Ejabberd server using your LDAP user account.
How it works…
Here, we have set up Ejabberd as an example of LDAP-based authentication. Similar to Ejabberd, various other systems support centralized authentication through LDAP with either built-in support or with a plug-in module. Make sure that you create a proper directory structure with organizational units, roles, and separate users in proper groups. Also use a separate user account for authenticating with the LDAP server itself. You need to set the respective LDAP credentials in the Ejabberd configuration file. If somehow your Ejabberd server gets compromised, then the LDAP server credentials are readily available to an attacker. To limit the risk, using separate and limited accounts is a good idea. Ejabberd also supports anonymous authentication with the LDAP server and mostly uses it as a read-only database. So, even if you skip the authentication details (depending on the LDAP configuration), Ejabberd should work well and authenticate your users.
Ejabberd also provides good enough debug logging, where you can see the actual communication with the LDAP server. You will need to set logging to debug mode in the Ejabberd configuration. The log files are located in the /opt/ejabberd-version/logs directory or the /var/log/ejabberd directory, depending on the source of the Ejabberd installation.
See also
- Ejabberd docs LDAP section at https://www.process-one.net/docs/ejabberd/guide_en.html#ldap
How to do it…
As Ejabberd provides inbuilt support for LDAP-based authentication, we simply need to edit configurations and set the auth method to LDAP. If you have used a Debian package for the Ejabberd installation, your Ejabberd should be installed in /opt/ejabberd-version directory and the configuration can be found at /etc/ejabberd-version/conf. If you have installed Ejabberd from source, all configuration files are located in the /etc/ejabberd directory:
- Open
ejabberd.ymlfrom your Ejabberd configuration directory and search for Authentication. With the default settings, it should contain the following line indicating internal authentication:auth_method: internal
- Comment out that line by changing it as follows:
## auth_method: internal
- Next, find Authentication using LDAP. This section contains a few parameters and configures communication with the LDAP server. Search and update the following parameters:
ldap_servers: - "domain/IP of LDAP server" ldap_port: 389 ldap_rootdn: "cn=admin,dc=example,dc=com" ldap_password: "password" ldap_base: "ou=ejabberd,dc=example,dc=com"
I have used a default admin account to authenticate with the LDAP server itself. In a production environment, you should change it to a different account. With a default LDAP setup, you can skip the
ldap_rootdnandldap_passwordsettings to enable anonymous connection. - Next, under the
ldap_baseparameter, I have restricted users to the Organizational Unit namedEjabberd. Only the user accounts that are configured under theEjabberdunit can log in with the Ejabberd server. - Now, save the configuration file changes and close the file, and then restart the Ejabberd server with the following command:
$ sudo /opt/ejabberd-version/bin/ejabberdctl restart - If the server fails to restart, check the log files for any configuration errors. Alternatively, you can use the
reload_configoption toejabberdctlto update the in-memory configuration without restarting:$ sudo /opt/ejabberd-version/bin/ejabberdctl reload_config - Once the server has started, you can log in with your LDAP accounts. You will need a JID to log in with Ejabberd, which is a combination of a UID from the LDAP server and any host configured on Ejabberd, for instance,
uday@cookbook.com, whereudayis the UID on LDAP andcookbook.comis the host served by Ejabberd server. The domain entries on the LDAP server and Ejabberd need not match.The following is the default host entry for my Ejabberd installation:

- Now you can log in to Ejabberd with your LDAP username. Here is the account set up in my chat client with the JID
uday@ubuntu, whereudayis my LDAP user andubuntuis the Ejabberd host:
Once all things are set up, you should be able to connect to the Ejabberd server using your LDAP user account.
How it works…
Here, we have set up Ejabberd as an example of LDAP-based authentication. Similar to Ejabberd, various other systems support centralized authentication through LDAP with either built-in support or with a plug-in module. Make sure that you create a proper directory structure with organizational units, roles, and separate users in proper groups. Also use a separate user account for authenticating with the LDAP server itself. You need to set the respective LDAP credentials in the Ejabberd configuration file. If somehow your Ejabberd server gets compromised, then the LDAP server credentials are readily available to an attacker. To limit the risk, using separate and limited accounts is a good idea. Ejabberd also supports anonymous authentication with the LDAP server and mostly uses it as a read-only database. So, even if you skip the authentication details (depending on the LDAP configuration), Ejabberd should work well and authenticate your users.
Ejabberd also provides good enough debug logging, where you can see the actual communication with the LDAP server. You will need to set logging to debug mode in the Ejabberd configuration. The log files are located in the /opt/ejabberd-version/logs directory or the /var/log/ejabberd directory, depending on the source of the Ejabberd installation.
See also
- Ejabberd docs LDAP section at https://www.process-one.net/docs/ejabberd/guide_en.html#ldap
How it works…
Here, we have set up Ejabberd as an example of LDAP-based authentication. Similar to Ejabberd, various other systems support centralized authentication through LDAP with either built-in support or with a plug-in module. Make sure that you create a proper directory structure with organizational units, roles, and separate users in proper groups. Also use a separate user account for authenticating with the LDAP server itself. You need to set the respective LDAP credentials in the Ejabberd configuration file. If somehow your Ejabberd server gets compromised, then the LDAP server credentials are readily available to an attacker. To limit the risk, using separate and limited accounts is a good idea. Ejabberd also supports anonymous authentication with the LDAP server and mostly uses it as a read-only database. So, even if you skip the authentication details (depending on the LDAP configuration), Ejabberd should work well and authenticate your users.
Ejabberd also provides good enough debug logging, where you can see the actual communication with the LDAP server. You will need to set logging to debug mode in the Ejabberd configuration. The log files are located in the /opt/ejabberd-version/logs directory or the /var/log/ejabberd directory, depending on the source of the Ejabberd installation.
See also
- Ejabberd docs LDAP section at https://www.process-one.net/docs/ejabberd/guide_en.html#ldap
See also
- Ejabberd docs LDAP section at https://www.process-one.net/docs/ejabberd/guide_en.html#ldap
























































