Outlining when to use packet analysis
We use packet analysis in many ways. We can troubleshoot latency issues, test IoT devices, monitor for threats, and baseline the network. Let's evaluate some of this activity, starting with troubleshooting, which is a common use of packet analysis.
Troubleshooting latency issues
Wireshark can be a valuable asset when troubleshooting issues on the network. There are many built-in tools designed to gather and report network statistics. We can analyze network problems and monitor bandwidth usage per application and process. The information gathered can help identify choke points and maintain efficient network data transmission.
Protocol analysis enables the network administrator to monitor the traffic on the network, unearthing problems that determine where performance can be fine-tuned. For example, if you suspect latency, you can obtain a capture in the area where you suspect trouble, and then run a Stevens graph, as shown in the following screenshot:
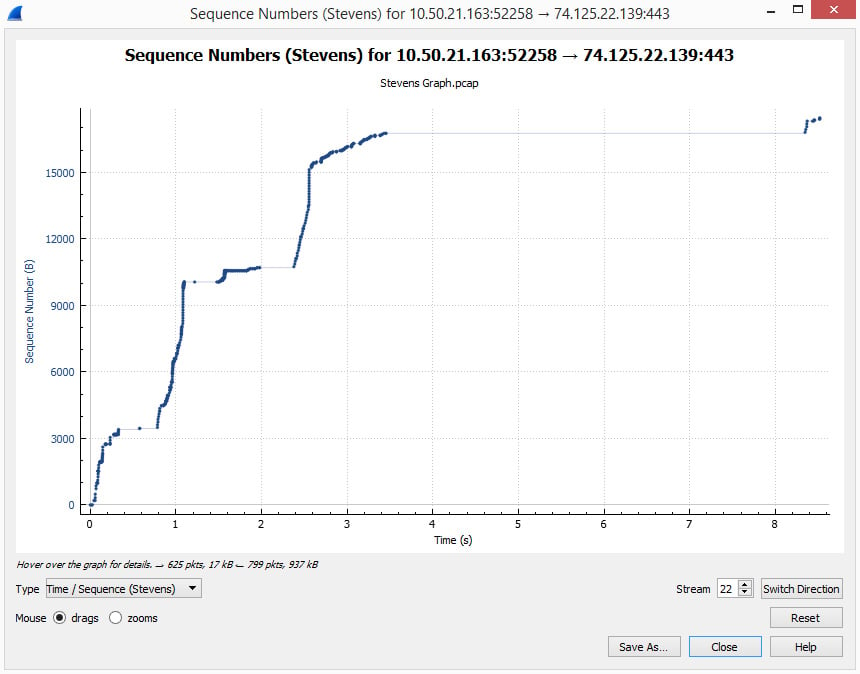
Figure 1.8 – A Stevens graph
Once the graph is complete, you can examine details that can highlight errors in the communication stream. For example, along the top of the graph, we see a straight line that continues for approximately four (4) seconds. The line represents a gap in transmission and may warrant further investigation.
In addition to troubleshooting the network, many are discovering how Wireshark can be a valuable asset in testing IoT devices prior to their implementation in an organization.
Testing IoT devices
The IoT is a ubiquitous transformation of intelligent devices embedded in everyday objects that connect to the internet, enabling them to send and receive data. The IoT has several components: people, infrastructure, things, processes, and data. IoT has become a billion-dollar industry as consumers, along with industries, are seeing the benefits.
Even with all of the benefits, prior to connecting an IoT device to the network, it's best to run some tests. Using Wireshark can help you see what happens when you plug the device into the network. The following is a list of questions that Wireshark can help determine:
- How do the devices communicate once they are active? Do they phone home without being prompted?
- What information do they communicate? Are the username and password sent in plain text?
The only way you can understand the behavior of these devices is by plugging one in, capturing the data exchange, and analyzing the packet capture. The information obtained can provide valuable insights into the vulnerabilities of IoT devices.
Along with troubleshooting and testing, Wireshark can be instrumental in proactive threat assessment.
Monitoring for threats
Monitoring for threats occurs in one of three ways:
- Proactive: Monitoring your systems and preventing threats by using a device such as an IDS.
- Active: Proactively seeking threats by conducting packet analysis and monitoring log files.
- Reactive: A system has fallen victim to an attack and the incident response team manages the attack, followed by a forensic exercise.
Wireshark can help the security analyst take an active role in monitoring for threats. While Wireshark does not provide any alerts, it can be used in conjunction with an IDS to investigate possible malicious network activity.
For example, while using snort (an open source IDS), the sensor produced the following alert, which could be an indication of malicious activity on the protected network:
DELETED WEB-MISC text/html content-type without HTML – possible malware C&C (Detection of a non-standard protocol or event) [16460]
This alert indicates that an infected host might be communicating with an external entity and sending information gathered on the network to a botmaster. The security analyst should take immediate action by running a capture in different segments of the network to identify and mitigate the threat.
Industries also see the value in using Wireshark for threat monitoring. For example, in the Cisco Certified CyberOps Associate certification prep course, students learn how to observe and monitor for unusual traffic patterns using Wireshark, as they hone their skills in preparing to work alongside cybersecurity analysts within a Security Operations Center (SOC).
In order to determine what traffic is unusual, or to properly troubleshoot the network, you must be able to determine what constitutes normal network activity. This is achieved by conducting a baseline, as outlined in the following section.
Baselining the network
A network baseline is a set of parameters that define normal activity. The baseline provides a snapshot of network traffic during a window of time using Wireshark or tshark. Key characteristics for baseline can include utilization, network protocols, effective throughput, forwarding rates, and network latency. The network team can use the baseline for forecasting and planning, along with optimization, tuning, and troubleshooting.
The baseline process goes through several stages: plan, capture, save, and analyze. Once the baseline is complete, the network analyst can review the captured data in order to assess general performance for end-to-end communications. Baselining the network helps to gain valuable information regarding the health of the network, and possibly identify current network problems. In addition to this, subsequent baselining exercises can help predict future problems.
Whenever the installation of new equipment is planned, it's best to do a baseline prior to the change. After implementation, do another capture so you can identify possible issues in the traffic flow and then fine-tune the configuration.
As you can see, there are many ways we can use packet analysis to monitor, test, baseline, and troubleshoot. However, because of the ability to obtain sensitive information or as a precursor to an attack, packet analysis should only be done in the following circumstances:
- The network is your own, or you have received explicit permission to conduct packet analysis for security scans.
- It is completed during troubleshooting network connectivity issues.
In addition, consideration should be given to maintain the privacy of the data collected, and have a proper method to obtain, analyze, and retain any packet captures.
As outlined, we now know the many reasons to use packet analysis. Let's summarize by embracing Wireshark, which is one of the most powerful packet analysis tools available today.























































