A few years ago, I was working on an Active Directory restructuring project for a world-famous pharmaceutical company. According to the company policy, I had to travel to their headquarters to perform the project tasks. So, on a rare sunny English morning, I walked into the company's reception area. After I explained who I am and why I was there, the nice lady at the reception, Linda, handed me a set of forms to fill in. They asked for my personal details, such as name, phone number, how long I will be there, and in which department. Once I filled out the forms, I handed them over to Linda, and she had to make a few calls to verify whether my visit was expected and confirm my access to different buildings with the respective department managers. Then she made a card with my details and handed it over to me. She instructed me on how to use it and which buildings I was allowed into.
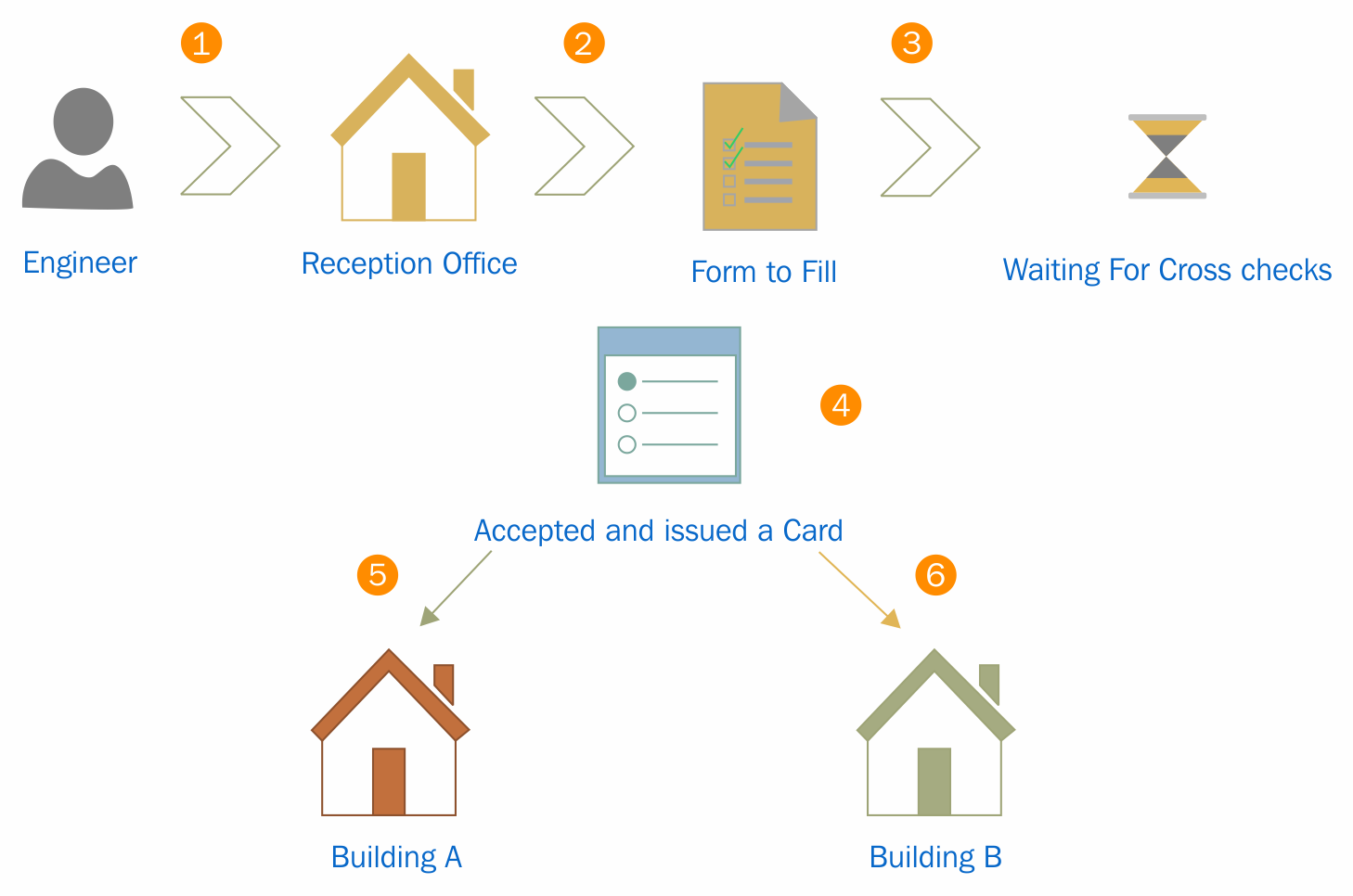
When you think about this process, you'll find that it contains the functions of a directory service:
- The forms that Linda handed over to me contained certain questions to help her understand who the person was. They were predefined questions and I had to answer them in order to register my information in their system.
- Once I submitted the forms, she didn't hand over the electronic card right away. She made calls to verify my identity and also confirm which buildings I would have access to. Then, my details were registered with the system, and it generated an electronic card that had my photo and a bar code. With that, I became a part of their system, and that particular card was my unique identity within their organization. There would be no other visitor with the same bar code and identification number at the same time.
- If I needed to get access to buildings, I needed to tap the card at the entrance. Could I use my name or any other cards to get through? No! The locking system of the building doors only recognized me if I presented the correct card. So, having a unique identity in their system was not enough; I needed to present it in the correct way to get the required access.
- I went to another building and tried to tap the card. Even when I used it correctly, the doors wouldn't open. The guard in the building asked for my card. Once I handed it over, he scanned it with a bar code reader and checked some information on his computer screen. Then he informed me that I was not allowed into that building and guided me to the correct building. This means that my information can be accessed from any building through their system to verify my identity and access permissions.
- When I used the card in the correct buildings, it allowed me to step in. In the system, it first verified my identity and then checked whether I was authorized to work in that facility. If I was authorized, the system allowed access; if not, it rejected my request to enter.
- When I entered and left the building, I did not have to record my time. But the managers in that department knew how many hours I had worked as my check-in and check-out times had been recorded in the system and they could review the information anytime.
This system acts as an authentication and authorization system. It uses different protocols and standards to manage and protect identities saved in a central database. This is the primary need of a directory service.
Every organization has its own organizational structure. The most common way is to group roles, assets, and responsibilities into different departments, such as sales, IT, production, and quality assurance. Apart from skills and knowledge, employers use company resources such as applications and hardware devices to achieve company goals. In order to use these resources efficiency, it's important to have some kind of access control in place. The resources should be available for the required users at the required time. This is very easy if all this data about users, applications, and resources is recorded in a central repository and uses authentication and authorization to manage resources. This is how the directory service was born. Different service providers have different directory services, for example, the Novell directory services, Oracle directory service, and Red Hat directory service. The Microsoft Active Directory service is the most commonly used directory service in modern enterprises.



























































