Creating the distributed key management container in Active Directory
Some of the data stored by VMM needs to be held securely, so it cannot be compromised. For example, when you store user credentials in VMM for Run As accounts, the passwords for these are encrypted. When you install VMM, you are given the choice of where to store the encryption keys, as shown in the following screenshot:
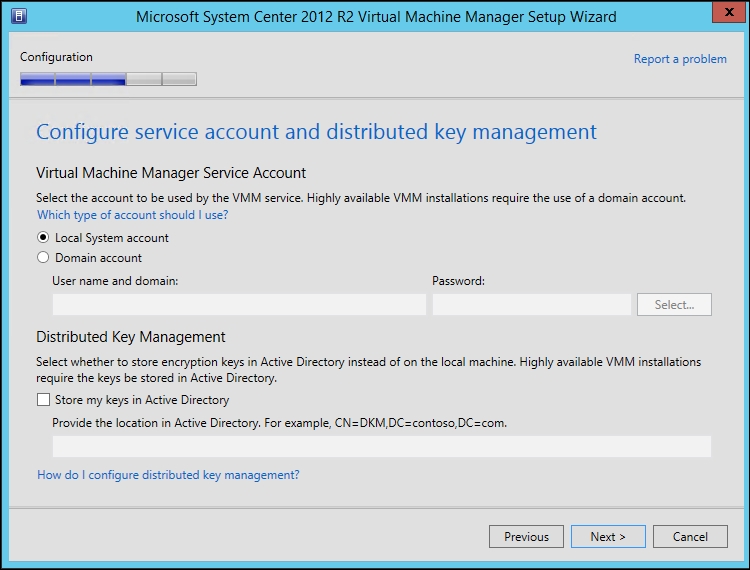
It is required to always store your encryption keys in Active Directory if you are going to deploy a highly available (clustered) installation of VMM.
The account used to install VMM must have full control over the container in Active Directory for the duration of the installation. During the installation, the installer program reconfigures the security of the container to ensure that only the correct security principles have access.
For a small scale installation, a single container in the root of Active Directory could be created to store the encryption keys. For a large-scale implementation where several different installations of VMM may be required due to the number of hosts and/or virtual machines, it is advisable to create a parent container in Active Directory and then have containers within the parent for each installation of VMM.
Getting ready
You will need to have sufficient access to Active Directory to create Container objects.
How to do it…
The following diagram shows you the high-level steps involved in this recipe and the tasks required to complete this recipe:

There are two possible methods of creating a container in Active Directory: one is using ADSI Edit and the other is via PowerShell. The method discussed here will be PowerShell-based:
- On a Domain Controller, or a machine where the Active Directory PowerShell Module is installed, open an elevated PowerShell console.
- The following PowerShell line will create a container called
DKMVMMin the root of Active Directory:New-ADObject –Name DKMVMM –Type container –Path "DC=ad,DC=demo,DC=com"
- Once the container has been created, the user who will be installing VMM needs to have full control of the container and that permission must apply to the container and all descendant objects. The following PowerShell will perform this function:
Set-PSDrive AD: $VMMInstallAccount = Get-ADUser -Identity Install_VMM $SID = New-Object System.Security.Principal.SecurityIdentifier $VMMInstallAccount.SID $DKMVMMacl = Get-Acl -Path "CN=DKMVMM,DC=ad,DC=demo,DC=com" $ObjectGuid = New-Object Guid 00000000-0000-0000-0000-000000000000 $newACL = New-Object System.DirectoryServices.ActiveDirectoryAccessRule $SID,"GenericAll","Allow",$objectguid,"All" $DKMVMMacl.AddAccessRule($newACL) Set-Acl -AclObject $DKMVMMacl -Path "CN=DKMVMM,DC=ad,DC=demo,DC=com"
This recipe is complete and the Distributed Key Management container is now ready to be used by DEMO\Install_VMM during installation.
How it works…
When VMM is installed, it uses the Distributed Key Management container to store its encryption keys and using the privileges granted to it previously, it will lock down the container to ensure that only the account running the VMM Management Service, the VMM Installation Account, and Domain Administrators have access to the container.























































