Different forms of sensitive information
Most users aren’t aware that when they access a web application or a website, it can collect some of their information. They just think that they are only accessing information from the web browser, but the reality is web applications can collect a lot more information than users think. To understand this, we can simply access https://www.deviceinfo.me (as shown in Figure 1.1). This website shows you how much information is collected from your device just by accessing a website. If you access this website with your mobile phone, it will display lots of information, including your mobile phone’s type/model, operating system, browser version, IP address, hostname, number of cores, memory, interfaces, and latitude and longitude. This shows that web applications and websites can collect almost all the information about a device.
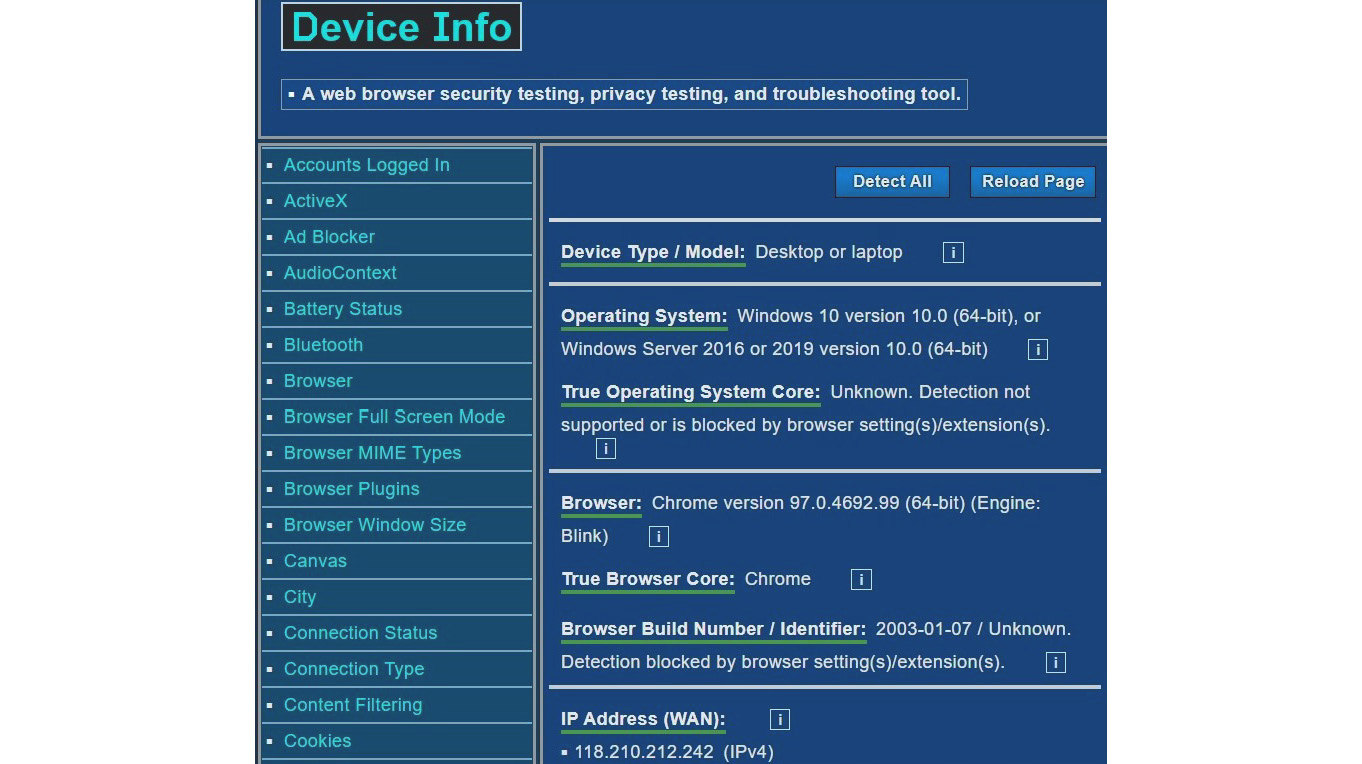
Figure 1.1 – Information derived about your device
This is a classic example of the data that a simple web application can collect, just by getting a device to access the application, without installing any agent or running a script.
When you look at the data that we have on our devices, mobile phones, or desktops, it can be sorted into a few categories. But not every case will contain PII.
Any form of information that could lead to any type of loss, such as financial, if accessed by a third party can be considered sensitive information.
Sensitive information can take different forms.
Mostly, people think that sensitive information is banking account information, including credit card numbers and social media account information. But a private picture or video clip can be even more sensitive than the preceding listed examples of sensitive information.
If you lose your credit card, the maximum damage that can occur is the credit limit of the stolen credit card is reached. But if someone accesses a private picture or video clip of yours, it can create more damage that might not be reversible.
Sometimes, we disclose sensitive information unintentionally. Let’s look at the following photo:

Figure 1.2 – Photo of a car, carrying sensitive information
This photo was taken by someone trying to sell their car. As a precaution, the seller has even masked the numberplate to reduce the information this photo discloses. Even if you inspect this photo closely, you might not find any interesting information. But although the seller has masked part of the vehicle identification number, there is still a lot of information given away with this photo without their knowledge. This information is known as metadata. Metadata can be defined as data about data.
We usually look at the content of a file, but metadata discloses even more information than we are aware of.
Let’s look at the metadata of the preceding photo. Let’s access http://metapicz.com/, upload the image, and see what we can find. This site can acquire meta information on an image. It extracts information including the camera make, model, exposure, and aperture of the device.

Figure 1.3 – Derived information from a picture
The preceding screenshot shows the make of the device that captured the photo of the car, as well as the model and exposure. Exposure refers to the amount of light that comes in while you are pressing the capture button of a camera. Aperture refers to the opening of the lens of the camera to allow light through and focal length is the distance between the lens and the image sensor. So, if someone analyzes an image, they can get a massive amount of information, even about the lighting conditions of the environment during the time of capturing this image.
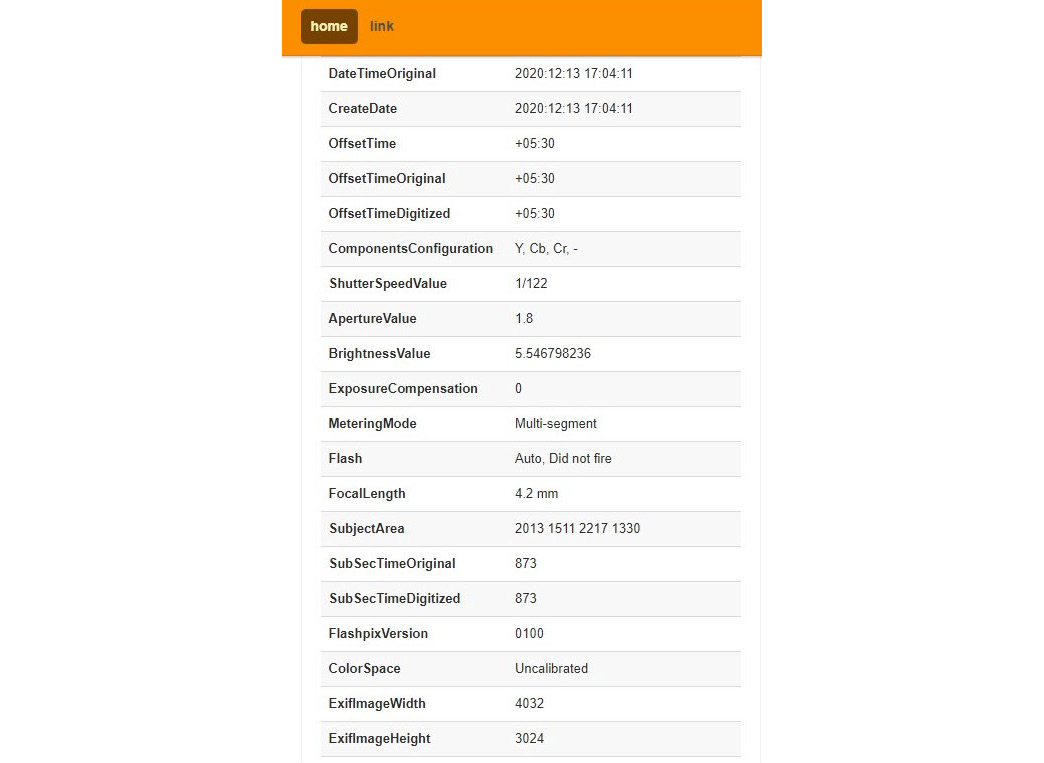
Figure 1.4 – More information from the image metadata
The preceding screenshot shows information related to the time the photo was taken, such as the created date and offset. Typically, offset refers to the time zone. According to this screenshot, the offset is +05.30, which refers to GMT +5:30, which is Asia/Colombo time, specifically, Kolkata. By analyzing this, we now know the region in which the photo was taken.
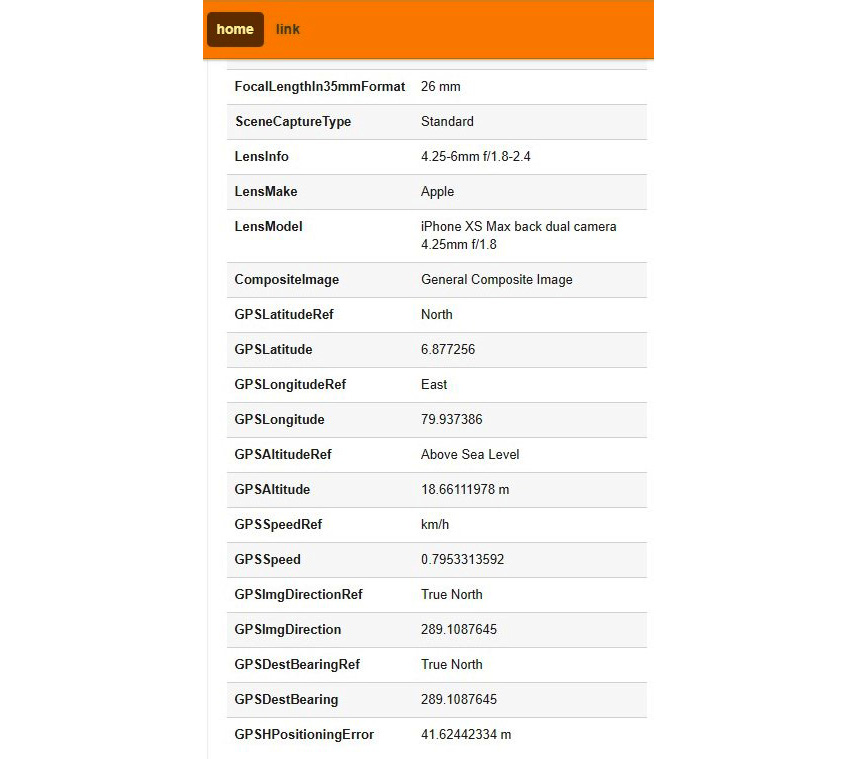
Figure 1.5 – Lens and GPS information derived from the image
Personally identifiable data or information is anything that discloses information about you, including your name, address, telephone number, or social media identity, photos with contents that identify you, and even metadata. Also, your email address or IP can be treated as PII. We should be able to control our privacy and decide when, how, and to what extent our PII is revealed.
This is also known as data privacy. There are many initiatives and acts around the globe that relate to data privacy, but data privacy can be violated at various levels. Most of the devices we use today compromise our privacy even without us being aware. We will take Android as an example. Whenever you use an Android phone, it collects a lot of information about you as we usually connect our Gmail account to get the full functionality of the Android device. Once you have connected your Gmail account to the Android device, it will start collecting your information.
If you want to see what information about you Google is collecting, access https://myactivity.google.com/ and log in using your Google account that is connected to your device. You will be amazed to see how much information Google collects, including your web and app activity, your location history, and your YouTube watch history, that is, all the videos you watch and search for on YouTube.
If you go to the location history and click the Manage Activity link, you will see how much data your device has uploaded to Google.

Figure 1.6 – Activity recorded in Google
If you select any of the dates, it will show you all your movements, including the method of commute, very accurate information about your walk, and even photos that you took taken during the journey using your device’s camera.

Figure 1.7 – Detailed information captured by Google
Even if you disable data connectivity on your Android device while traveling, the device will still collect all this information and upload it to Google whenever you connect your device to the internet later. This doesn’t just occur on the Android operating system; all devices do this – even your iPhone or Windows device.
If you want to check what information is being stored on your Windows device, press the Windows key + I to access Windows Settings | Privacy | Diagnostics & feedback | Open Diagnostic Data Viewer.
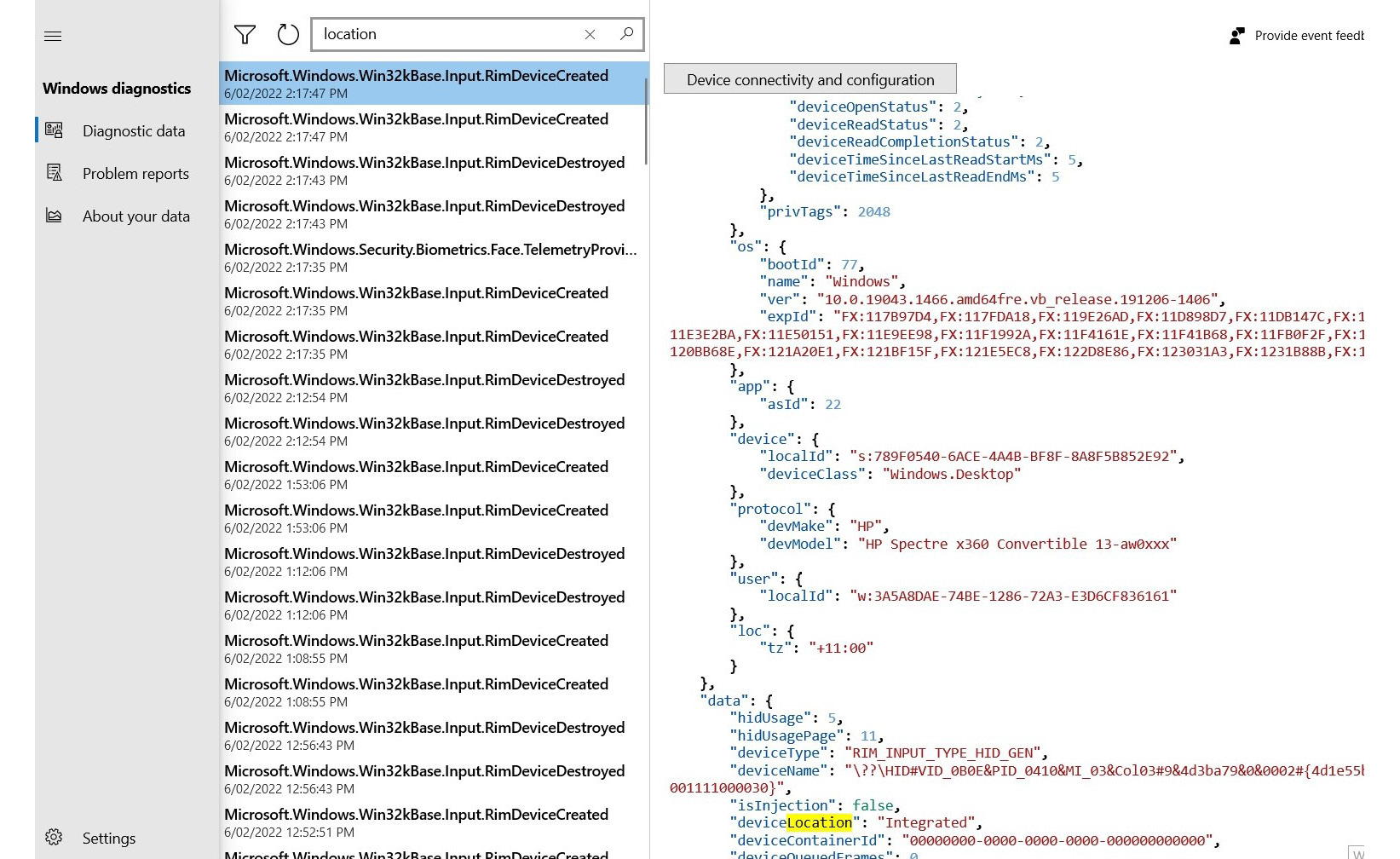
Figure 1.8 – Telemetric data shared with Microsoft by your device
This shows what your device is sharing with Microsoft. Not only operating systems but also applications collect our information. You may have noticed that many applications that you install on your device request access to your location, photos, and other sources of information, even if the app doesn’t need to use this information. As an example, if you install a flashlight app and it requests access to your location, that is suspicious.
The reality is most operating systems, applications, devices, and even manual systems collect this information. Sometimes, disclosing personal information can be dangerous. There was an incident reported in India recently related to this. A Business Process Outsourced (BPO) company that provides services to overseas companies from India was advertising a vacancy. Many people came for the interview. At the security post, there was an open register on which each candidate had to fill in information, including their name, address, telephone number, and email address. (This is common in many Asian countries.) There was a woman who attended the interview that got a call for a second interview at a different location in the evening. It was a bit suspicious, but the BPO company operates 24x7, so this wasn’t too odd of a scenario as during the first interview, they informed candidates that the job would be on a shift basis. The woman went for the second interview but never came back. Later investigations found that the call for the second interview was fake; her information was collected by someone who came to the same interview and as everyone was filling in an open registry, they were able to access all previous records. This shows how dangerous disclosing personal information can be. But still, I have seen many locations where retail stores do it especially during the 2020 pandemic, as they wanted to trace positive cases of COVID-19 and inform people who had come into contact with those infected people.

























































