Gaining access to the user interface
If you are deploying your firewall on a cloud provider like Azure or AWS, take a look at Chapter 14, Cloud-Based Firewall Deployments.
When taking a new device out of the box or setting up a VM on a local hypervisor, such as VMware ESXi, Fusion, NSX, Hyper-V, KVM, and so on, one of the first things you may need to do is to connect a console cable to gain access to the Command-Line Interface (CLI).
Older models only come with an RJ45 console port, so for those you will need a standard DB9-to-RJ45 console cable, optionally patched through a serial-to-USB cable so a modern laptop is able to interface with the port. The pinout for the DB9 should be as follows:
1 - Empty - Data Carrier Detect (DCD)
2 - 3 - Receive Data (RXD)
3 - 6 - Transmit Data - (TXD)
4 - 7 - Data Terminal Ready (DTR)
5 - 4 - Ground (GND)
6 - 2 - Data Set Ready (DSR)
7 - 8 - Request To Send (RTS)
8 - 1 - Clear to Send - (CTS)
9 - Empty - Ringing Indicator (RI)
Luckily there are USB-to-RJ45 cables available as well that will save you the trouble of figuring out the correct pinouts.

Figure 2.1: RJ45-to-USB console cable
All but the very old models also come with a micro-USB port, which allows a console connection to be made using a standard USB-A-to-micro-USB cable, as in the following picture:

Figure 2.2: PA-460 RJ45 and the micro USB console ports
In all cases, you will need to find which COM or TTY port is being used on your computer’s operating system.
On a Windows machine, the first time you plug in the cable a driver may need to be installed. Once the installation has completed you need to find the virtual COM port number that has been assigned to the console cable. In most cases, you can determine this virtual COM port number by following these steps:
- Open the Device Manager.
- Click Start | Control Panel | Hardware and Sound | Device Manager (under “Devices and Printers”).
- In the Device Manager list, look in Ports and find the virtual COM port assigned to the USB port. This entry will look similar to “USB to Serial Port (COM#)” where COM# is the number to be used in the following step.
Once you’ve determined the appropriate COM#, you will need a terminal emulation client to connect to the console. You can use a free client for this, such as PuTTY from https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html.
Besides the COM port, you may need to provide more settings to be able to connect. If asked, use these settings:
Bits per second: 9600
Data Bits: 8
Parity: none
Stop bits: 1
Flow control: none
On macOS and Linux, a USB serial connection will usually create a new tty (TeleTYpewriter) entry in the /dev/ directory; a USB-to-DB9 dongle may create a Call-Up (CU) entry in the /dev/ directory.
Find the proper device by searching with either of these commands:
ls /dev/tty.*
ls /dev/cu.*
You will find /dev/cu.usbserialxxxxx or /dev/tty.usbmodemxxxxx, where xxxxx is the serial device name.
Once you determine the appropriate device, you can connect to the console port by using the screen command set to 9600 bits per second:
screen /dev/tty.usbmodemxxxxx 9600
Now, go ahead and connect the console cable or micro USB to your laptop and appliance. If you have a port free on your management network, go ahead and connect the firewall’s MGT port to the switch. If you don’t have a management connection available yet, you will need to connect your laptop directly to the MGT port for easier access once the IP is set up on the management interface. Lastly, plug in the power cable.
If the firewall is loaded in a VM or cloud entity, hit the Start button to boot up the virtual appliance.
Once you’ve logged on to the console, you will see the operating system boot up, and if the firewall is already connected to a DHCP-enabled management network, you will see something similar to the following, where the DHCP address is already listed for your convenience:
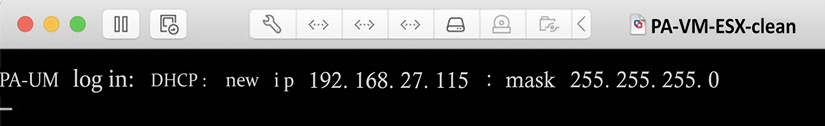
Figure 2.3: PA-VM post-boot DHCP information
If you missed this information, you can log on and use the following command to see the DHCP information:
admin@PA-220> show system info
hostname: PA-220
ip-address: 192.168.27.116
public-ip-address: unknown
netmask: 255.255.255.0
default-gateway: 192.168.27.1
ip-assignment: dhcp
If, for some reason, you have not received a DHCP address yet from your DHCP server, you can initiate a renew action from the CLI by using a > request dhcp client management-interface renew command.
Important note
The default username and password for a factory settings appliance or VM are as follows:
Username: admin
Password: admin
The first time you log on, you will be asked to change this default password.
If your network does not have a DHCP server, or you connected the firewall directly to your laptop, you will need to set an IP address manually. Copy and paste the following sheet into a text file and alter the <IP> entries with the appropriate IP for your management interface, the default gateway it will use to reach out to the internet, and the DNS servers it will use to resolve the domain names. Type the netmask in quad decimals, not in CIDR (slash notation subnet, such as /16 and /24):
configure
set deviceconfig system type static
set deviceconfig system ip-address <IP>
set deviceconfig system netmask <x.x.x.x>
set deviceconfig system default-gateway <IP>
set deviceconfig system dns-setting servers primary <IP>
set deviceconfig system dns-setting servers secondary <IP>
commit
You can chain set commands that belong in the same path and class so that you do not need to set each attribute in individual set commands; instead, you can add all the desired settings all at once. In the next example, I went into configuration mode, switched the management interface from DHCP to static configuration, and then combined all the configuration parameters for the management interface into one set command. Start by changing the default password to a new one, and then add the interface configuration:
admin@PA-220> set password
Enter old password :
Enter new password :
Confirm password :
Password changed
admin@PA-220> configure
Entering configuration mode
[edit]
admin@PA-220# set deviceconfig system type static
[edit] admin@PA-220# set deviceconfig system ip-address 192.168.27.5 netmask 255.255.255.0 default-gateway 192.168.27.1 dns-setting servers primary 1.1.1.1 secondary 1.0.0.1
[edit] admin@PA-220# commit
Commit job 2 is in progress. Use Ctrl+C to return to command prompt
...........................................55%....75%.....98%.......................100%
Configuration committed successfully
[edit]
admin@PA-220#
You may need to log back in after running the commit statement as the admin password was changed.
Important note
The > prompt in username@hostname> indicates that you are in operational mode and can execute runtime commands. The # prompt in username@hostname# indicates that you are in configuration mode and can add configuration parameters.
Operational commands can be run from config mode by prefixing run to a command—for example, user@host# run show clock.
Once the commit job finishes, you will be able to connect to the web interface through https://<IP> or by using an SSH client, such as PuTTY or the ssh command in Linux or macOS.
You are now able to get onto a freshly started firewall and configure it, so we can move on to the next step and gain access to the web interface.
Connecting to the web interface and CLI
Now that your device has an IP address, you can connect to its web interface via any browser using https://<IP>.
You will be met with an unfriendly error message, as in the following screenshots. This is due to the web interface using a self-signed certificate that has not been validated by any authority. For now, this can be safely ignored:
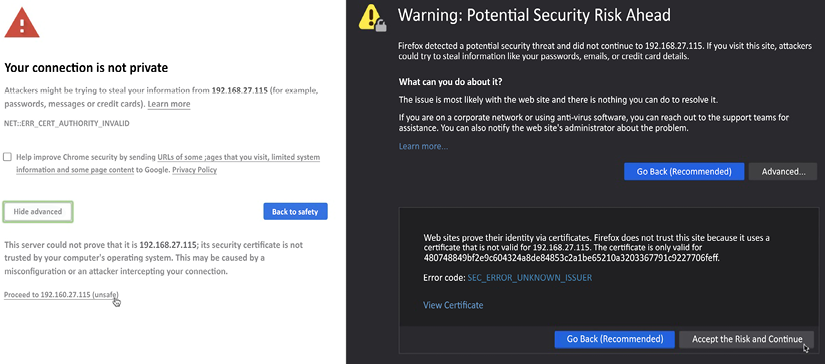
Figure 2.4: Certificate warnings in Chrome and Firefox
An SSH client will provide you with a slightly friendlier question:
tom$ ssh -l admin 192.168.27.115
The authenticity of host '192.168.27.115 (192.168.27.115)' can't be established.
RSA key fingerprint is SHA256:Qmre8VyePwwGlaDmm6JTYtjou42d1i/Ru6xZmmEk8Yc.
Are you sure you want to continue connecting (yes/no)?
The SSH connection will provide you with mostly the same user experience as the console connection, but SSH is more responsive and secure, and you can now access your device from anywhere on the management network.
The web interface provides you with a whole new user experience. When prompted for your username and password, input the default admin/admin combination or the username and password you created on the cloud provider.
Once you are logged in, the first screen you will see is the dashboard, which contains some general information about the health of your system, config changes, and which admins are logged on. The dashboard can be customized and additional widgets can be added from a list of prepared widgets, or widgets can be removed if they are not relevant.
For now, the General Information widget contains the most important information as you will need the serial number of the physical device, or the CPU ID and UUID on a virtual device, as shown in the screenshot below. The CPU ID and UUID will be needed to register and activate the VM while a physical device can be activated by its serial number:
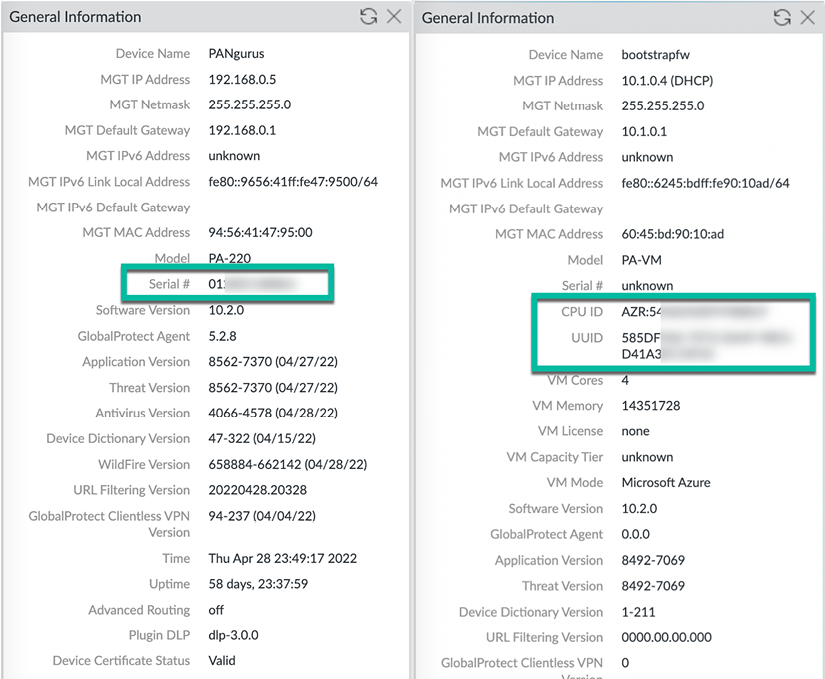
Figure 2.5: On the left is a PA-220 device, and on the right is a PA-VM device
Now that you have access to the web interface and are able to collect the system’s base information, we can go ahead and register the firewall and activate any of the feature licenses that were purchased. We will now have a look at how to perform the registration and licensing procedures.
























































