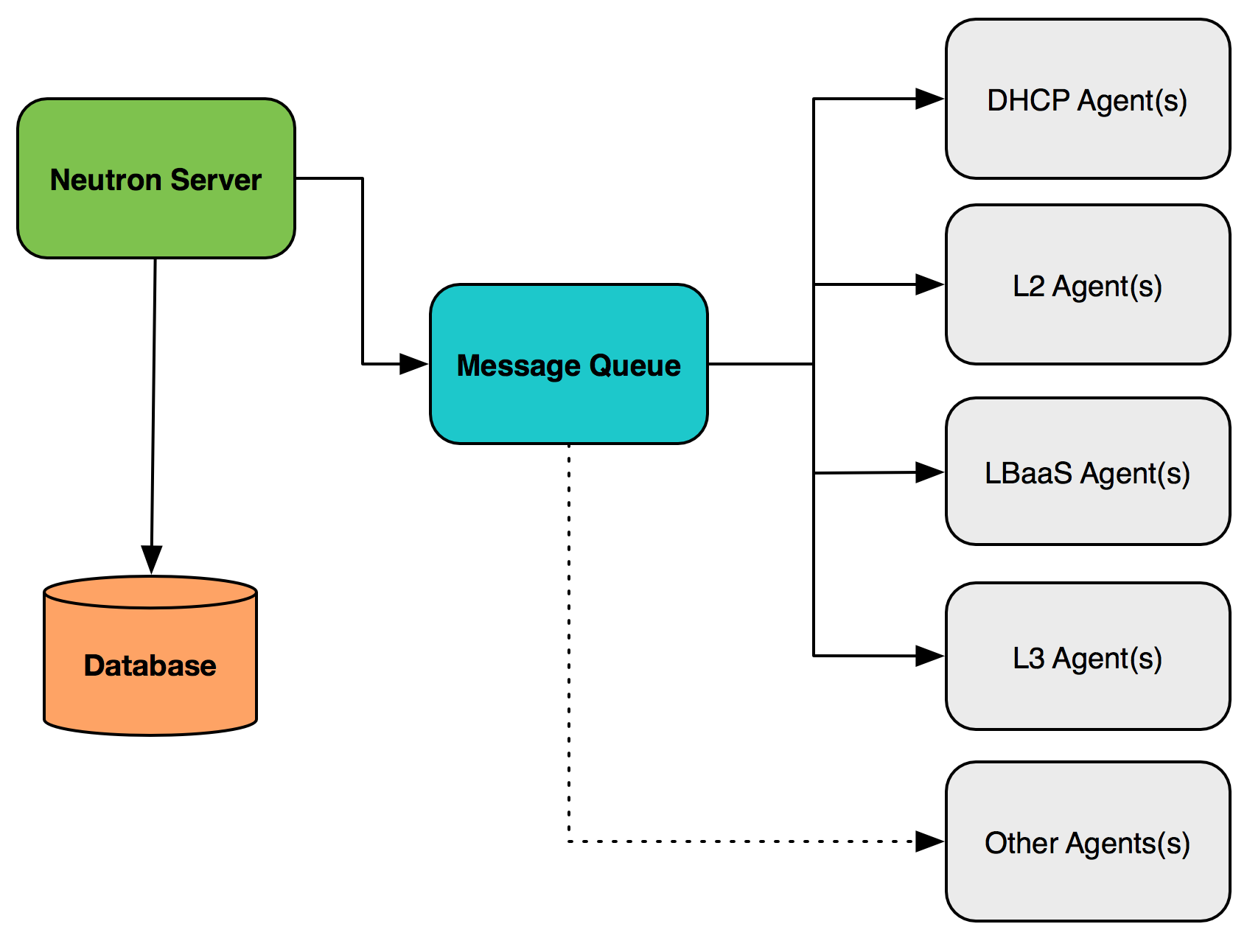
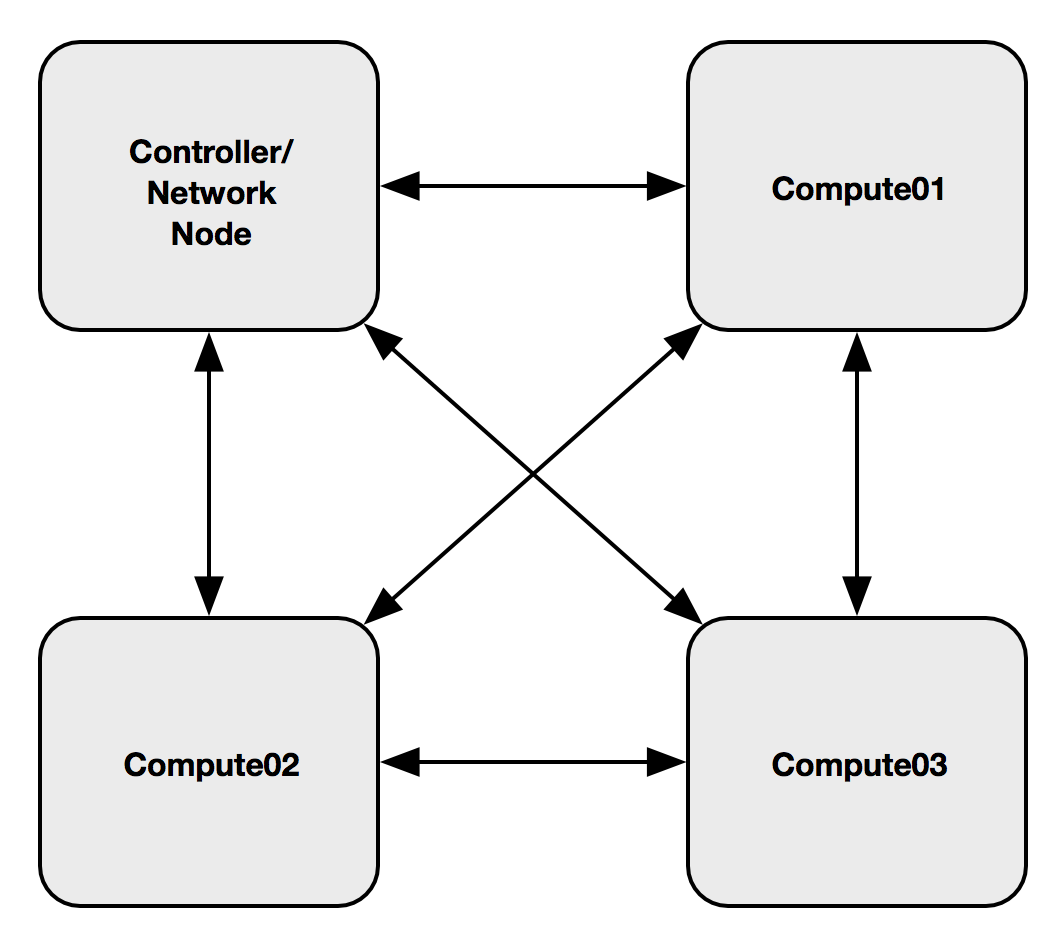
OpenStack gives users the ability to create and configure networks and subnets and instruct other services, such as Compute, to attach virtual devices to ports on these networks. The Identity service gives cloud operators the ability to segregate users into projects. OpenStack Networking supports project-owned resources, including each project having multiple private networks and routers. Projects can be left to choose their own IP addressing scheme, even if those addresses overlap with other project networks, or administrators can place limits on the size of subnets and addresses available for allocation.
There are two types of networks that can be expressed in OpenStack:
- Project/tenant network: A virtual network created by a project or administrator on behalf of a project. The physical details of the network are not exposed to the project.
- Provider network: A virtual network created to map to a physical network. Provider networks are typically created to enable access to physical network resources outside of the cloud, such as network gateways and other services, and usually map to VLANs. Projects can be given access to provider networks.
The terms project and tenant are used interchangeably within the OpenStack community, with the former being the newer and preferred nomenclature.
A project network provides connectivity to resources in a project. Users can create, modify, and delete project networks. Each project network is isolated from other project networks by a boundary such as a VLAN or other segmentation ID. A provider network, on the other hand, provides connectivity to networks outside of the cloud and is typically created and managed by a cloud administrator.
The primary differences between project and provider networks can be seen during the network provisioning process. Provider networks are created by administrators on behalf of projects and can be dedicated to a particular project, shared by a subset of projects, or shared by all projects. Project networks are created by projects for use by their instances and cannot be shared with all projects, though sharing with certain projects may be accomplished using role-based access control (RBAC) policies. When a provider network is created, the administrator can provide specific details that aren't available to ordinary users, including the network type, the physical network interface, and the network segmentation identifier, such as a VLAN ID or VXLAN VNI. Project networks have these same attributes, but users cannot specify them. Instead, they are automatically determined by Neutron.
There are other foundational network resources that will be covered in further detail later in this book, but are summarized in the following table for your convenience:
|
Resource
|
Description
|
|
Subnet
|
A block of IP addresses used to allocate ports created on the network.
|
|
Port
|
A connection point for attaching a single device, such as the virtual network interface card (vNIC) of a virtual instance, to a virtual network. Port attributes include the MAC address and the fixed IP address on the subnet.
|
|
Router
|
A virtual device that provides routing between self-service networks and provider networks.
|
|
Security group
|
A set of virtual firewall rules that control ingress and egress traffic at the port level.
|
|
DHCP
|
An agent that manages IP addresses for instances on provider and self-service networks.
|
|
Metadata
|
A service that provides data to instances during boot.
|