Wireshark is an advanced network and protocol analyser, it lets you visualize network's activity in graphical form, and assists professionals in debugging network-level issues. Wireshark enhances the ability of network and security professionals by providing detailed insight into the network traffic. However, Wireshark is also used by malicious users to sniff network traffic in order to obtain sensitive data in the form of plain text.
Introduction to Wireshark
Why use Wireshark?
Many people, including myself, are obsessed with the simplicity of the packet-capturing features that Wireshark provides us with. Let's quickly go through a few of the reasons why most professionals prefer Wireshark to other packet sniffers:
- User friendly: The interface of Wireshark is easy to use and understand, tools & features are very well organized and represented.
- Robustness: Wireshark is capable of handling enormous volumes of network traffic with ease.
- Platform independent: Wireshark is available for different flavors of operating system, whether Windows, Linux, and Macintosh.
- Filters: There are two kinds of filtering options available in Wireshark:
- You choose what to capture (capture filters)
- You choose what to display after you've captured (display filters)
- Cost: Wireshark is a free and open source packet analyzer that is developed and maintained by a dedicated community of professionals. Wireshark also offers a few paid professional applications as well. For more details, refer to Wireshark's official website https://www.wireshark.org/.
- Support: Wireshark is being continuously developed by a group of contributors that are scattered around the globe. We can sign up to Wireshark's mailing list or we can get help from the online documentation, which can be accessed through the GUI itself. Various other online forums are also available for you to get the most effective help; go to Google Paid Wireshark Support to learn more about the available support.
The installation process
The installation of Wireshark is very simple and easy to follow. Go through the following steps to install it on your system:
- The recipes and examples in this book will be for use on a Macintosh and Windows PC; for other operating systems, the installation is the same. Some OSes, such as Kali Linux, come with a preinstalled version of Wireshark.
- Once you have located the correct version of Wireshark for your platform (Wireshark 2.6.1 Intel 64.dmg), install Wireshark by following the wizard.
- Restart the computer after completion of the installation process to commit the changes that were made.
- Double-click the Wireshark icon on your desktop to the run the application:
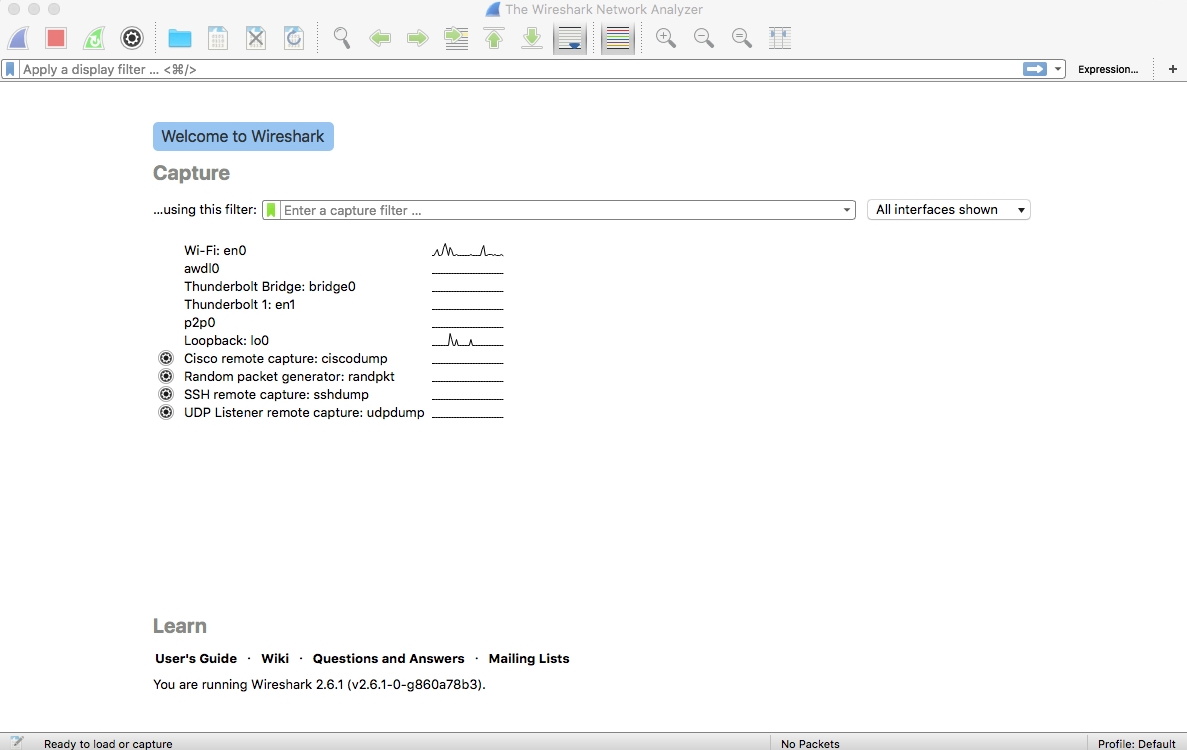
The Wireshark screen
Troubleshooting common installation errors
Go through the following simple checklist to ensure that you are able to run Wireshark successfully (make sure that all of these criterias are met):
- You have downloaded Wireshark from known and trusted source only
- You have administrative privileges to run Wireshark
- The installation of Wireshark and the Winpcap driver has been completed successfully without any exceptions
- You are connected to the network that you want to capture network traffic from
- If you are trying to sniff using a virtual machine, ensure that you have set your network adapter to bridged mode
- Restart your machine to ensure the changes have been applied after successful installation of Wireshark
- Your NIC card supports promiscuous mode sniffing (when needed)
- You can see all of the interfaces (wired, wireless, and logical) on the home screen of Wireshark
- The line graph followed by the interface name shows activity on the Homescreen
- Also, you have legal permissions to capture network traffic













































































