This recipe describes how to configure optional interfaces (for example, a DMZ network) to pfSense.
Configuring optional interfaces from the console
Getting ready
The optional network you will create in this network will be a DMZ, which is short for the DeMilitarized Zone. The idea of a DMZ is to have a network where some traffic is allowed to pass and some traffic is not. Typically, traffic in the DMZ is allowed to pass to and from the internet but not to other internal networks. Traffic is allowed to pass from internal networks to the DMZ. Thus, the flow of traffic looks like this:
Internet <<>> DMZ << Internal networks
Unsafe internet traffic, for example, is allowed to enter a web server in the DMZ. LAN traffic is allowed to enter the DMZ as well, for example, if someone on the LAN wants to access the web server as well. However, the key lies in the fact that no DMZ traffic is allowed to access the internal networks.
To configure a DMZ, you will need at least one spare interface, and you will have to have added it using the procedure outlined in the Identifying and assigning interfaces recipe. We will assume that you have added at least one such interface (named OPT1).
How to do it...
- Navigate to Interfaces | OPT1.
- Check the Enable Interface checkbox:
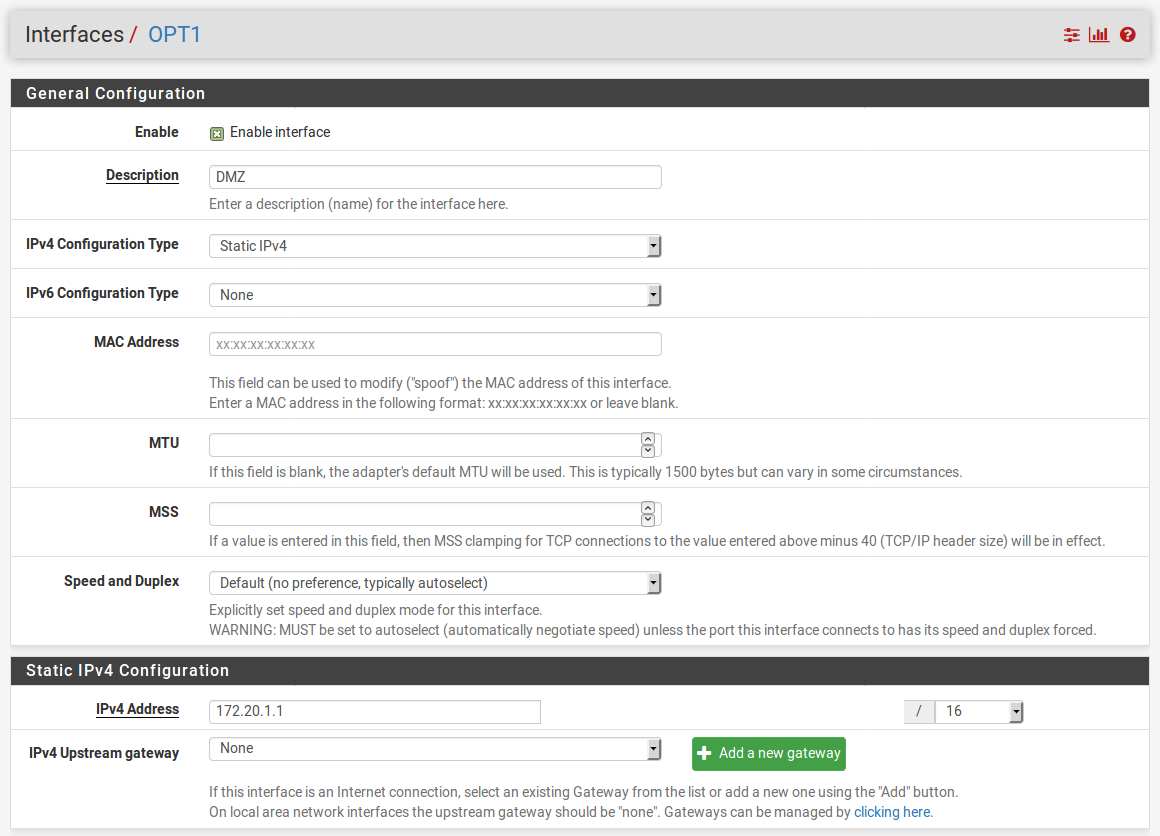
- Set Description to DMZ.
- Set IPv4 Configuration Type to Static IPv4.
- Enter an IPv4 Address and the CIDR. In our case, we will use 192.168.2.1 and select 24 from the CIDR dropdown list.
- Leave IPv4 Upstream gateway set to None.
- Leave the Block private networks and Block bogon networks checkboxes unchecked (they should be unchecked by default).
- When you are done making changes, click on the Save button. When the page reloads, click on the Apply Changes button.
How it works...
Your DMZ network will now allow external (WAN) access. Your LAN network will now be able to access the DMZ, but the DMZ will not be able to access the LAN.
There's more...
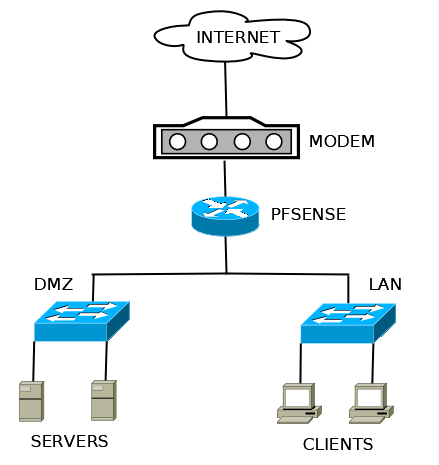
You can now attach a switch to your DMZ port to allow you to attach multiple nodes to your DMZ network. If you have been following the recipes in this chapter in order, your network will now look like this:
See also
- The Identifying and assigning interfaces recipe
- The Configuring a WAN interface recipe
- The Configuring a LAN interface recipe













































































