Within security rules, Actions form the second part (out of four, see previous section, Attribute-Based Access Control) of the ACAB and determine what type of activity the user is permitted to perform on the defined resource. While read and write are common actions very familiar to traditional access control, Qlik Sense has extended them to many more, which, on one side, makes the security rules rich and powerful; but on the other side, complicated as well. This section will cover the different types of actions in Qlik's security rules and will discuss potential use cases where relevant. Each action applies to a specified resource, which forms the basis of how it can be utilized.
Permissions on actions are applied to both the Qlik Management Console and the hub, as the following image shows:
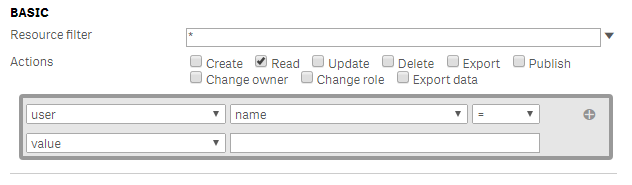
- Create: Create allows the user to create the defined type...





































































