ISO 27001 — Information Security Management System (ISMS)
The following diagram shows the key objectives for an Information Security System:
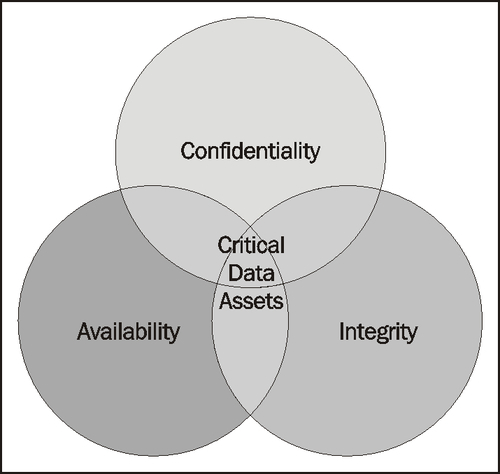
The ISMS must protect information assets from any threats to their availability, integrity, and confidentiality. The ISMS includes Organizational structures, policies, planning activities, practices, procedures, processes, and resources. It is set up to ensure that processes, technology, and user behavior all align to this goal.
ISO 27001 provides a specification against which a deployment and ISMS can be verified by an accredited certification body, such as the UK Accreditation Service. Such organizations are permitted to grant a formal certificate.
The components of an Information Security Management System
While the ISMS specification has other components, six of them are crucial.
A defined scope
An information security policy
A risk assessment
A risk treatment plan
For each risk treatment, state the control objectives and controls to be implemented...































































