Microsoft Intune
What is unified endpoint management and how does this look through the concept of Microsoft Intune? The following high-level architecture drawing (Figure 2.2) explains how everything within Microsoft Intune comes together in one unified endpoint management experience.
There is one console for your physical and cloud PCs via Windows 365 endpoints and mobile devices. This is the only place where they can be managed in a unified way. Also, the Intune company portal can deploy apps from Configuration Manager, Intune, Windows 365, Azure Virtual Desktop, and Microsoft Entra ID – one end user experience for all apps!
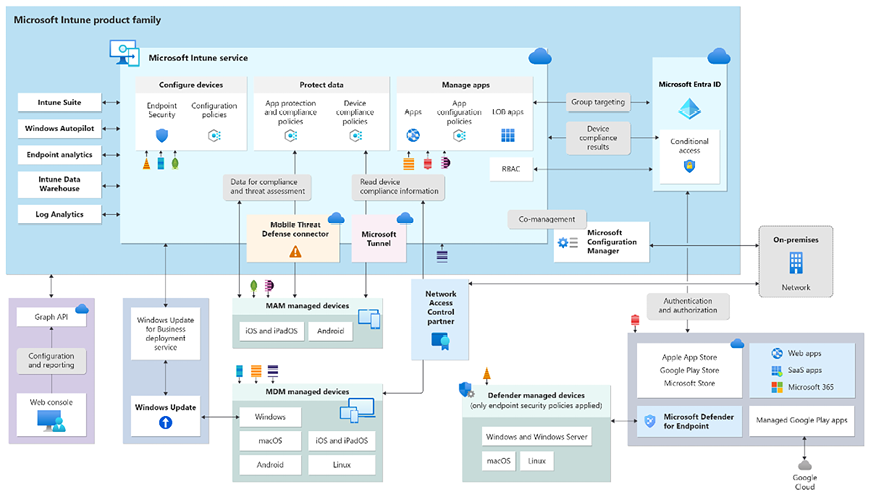
Figure 2.2: Microsoft Intune architecture diagram
The diagram of the Microsoft Intune architecture illustrates the three stages of the cloud management journey using Configuration Manager and Intune as a single, unified endpoint management solution:
- Tenant attach
- Co-management workloads
- Cloud-native management
All new Windows devices should go directly to the cloud with Microsoft Entra ID with automatic enrollment into Intune. This leverages Windows Autopilot for the best onboarding experience for IT and end users. If your organization already has a Configuration Manager environment with lots of applications that you are deploying to your on-premises managed devices, you can leverage the same application delivery method by using the built-in option Co-management settings in Intune to provide a coherent end user onboarding experiences for new devices.
We recommend waiting for a reason to go cloud native. As an example, you can move to Entra joined devices during a hardware refresh or device troubleshooting scenario when there’s a new (or reset) instance of Windows. Using this approach, you minimize user disruption and streamline the conversion process to Entra ID Join. Remember, there’s no Microsoft-supported process or path to convert an existing device from Hybrid Azure Active Directory Join (HAADJ) to Azure Active Directory Join (AADJ) without a Windows device reset. This would involve user downtime and loss of productivity.
You can proactively reset existing devices to move to Entra ID Joined. This approach can be more disruptive to end users and requires more planning and testing. But, you can use this approach if you have an end user scenario where it makes sense to reset devices or if you have a strong business case to move to Entra ID Joined.
For pre-existing devices, begin utilizing tenant-attach features that offer the most adaptable route for Configuration Manager users to start reaping the benefits of the cloud without necessarily registering their Windows clients with Intune. Link the Configuration Manager environment to the cloud and instantly gain access to a range of remote actions and endpoint analytics. If your organization is ready for the next step, you can start onboarding Windows devices into a co-management state, which means managing Windows clients using both Configuration Manager and Intune. Leverage the best of both worlds by moving one workload to the cloud at a time.
Intune admin center portal
The Microsoft Intune admin center portal serves as your comprehensive, single-point admin platform for formulating policies and managing your devices. It empowers IT administrators to incorporate other essential device management services, such as groups, security baselines and settings, Conditional Access, analytics tools, and reporting.
Microsoft Intune is a fully cloud-based MDM and MAM service for your applications and devices. It allows you to regulate features and settings on Android, Android Enterprise, iOS/iPadOS, macOS, and Windows devices. It also integrates with other services, including Entra ID, and mobile threat defense mechanisms.
In the Microsoft Intune portal, you can create compliance policies and check the compliance status of targeted devices. The device compliance policy marks the device as compliant or non-compliant. If you have enabled Conditional Access in your Microsoft 365 cloud environment, you can leverage compliance status from Intune to allow or block access to corporate data.
Microsoft 365 admin center portal
In the Microsoft 365 admin center portal (https://admin.microsoft.com), you can manage and administer all your Microsoft 365 cloud services. The most common task that you perform in this portal is to purchase and assign licenses for your Microsoft services.
Here’s a full list of what you can do via the Microsoft 365 admin center:
|
Menu |
What it’s for |
|
Home |
This is the landing page in the admin center. You’ll see where to manage users, billing, service health, and reports. |
|
Users |
Create and manage users in your organization, like employees or students. You can also set their permission level or reset their passwords. |
|
Groups |
Create and manage groups in your organization, such as a Microsoft 365 group, distribution group, security group, or shared mailbox. |
|
Resources |
Create and manage resources, like a SharePoint site collection. |
|
Billing |
View, purchase, or cancel subscriptions for your organization. View past billing statements or view the number of assigned licenses to individual users. |
|
Support |
View existing service requests or create new ones. |
|
Settings |
Manage global settings for apps like email, sites, and Microsoft 365. Change your password policy and expiration date. Add and update domain names like contoso.com. Change your organization profile and release preferences. And choose whether partners can access your admin center. |
|
Setup |
Manage existing domains, turn on and manage multi-factor authentication, manage admin access, migrate user mailboxes to Microsoft 365, manage feature updates, and help users install their Microsoft 365 apps. |
|
Reports |
See at a glance how your organization is using Microsoft 365 with detailed reports on email use, Microsoft 365 activations, and more. |
Table 2.1: Microsoft 365 admin center portal
Let’s talk more about how Microsoft Intune helps OEM partners.
Intune Partner portals
In the Microsoft Intune admin center, under Devices | Partner portal, you are able to access different hardware partner portals:
- Surface Management Portal
- HP Connect
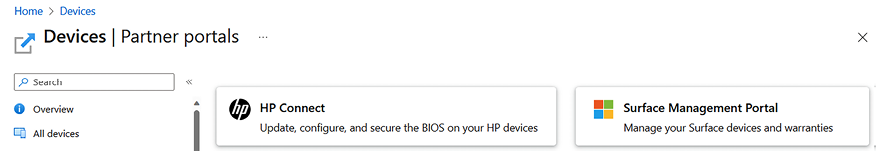
Figure 2.3: Microsoft Intune Partner portal
Surface Management Portal
The Surface Management Portal is already configured within your Intune tenant and will show your devices as soon as you have enrolled them into Intune.
If you do not have any Surface devices in your environment that are enrolled in Microsoft Intune, it will just show this:
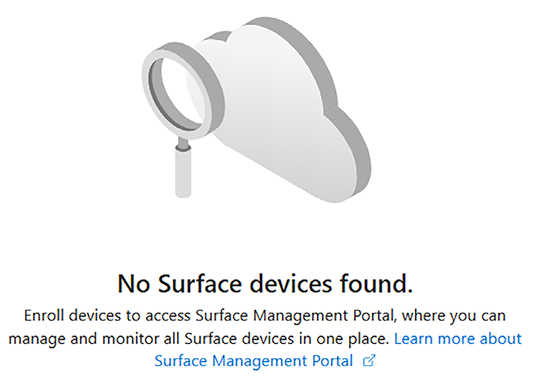
Figure 2.4: Surface Management Portal – No Surface devices found
The Surface Management Portal is a unified platform that enables IT administrators to manage and monitor all Microsoft Surface devices on a large scale within Microsoft Intune. Integrated into the Microsoft Intune admin center, it offers a comprehensive environment for complete visibility of both corporate and user-owned Surface devices.
The portal lets you quickly see any issues that need prompt attention before they hit your helpdesk. You can get insights into device compliance, support activity, and warranty coverage. Quickly see the status of each device, which ones are still in warranty or expiring soon, and the status of active support requests with your hardware providers.
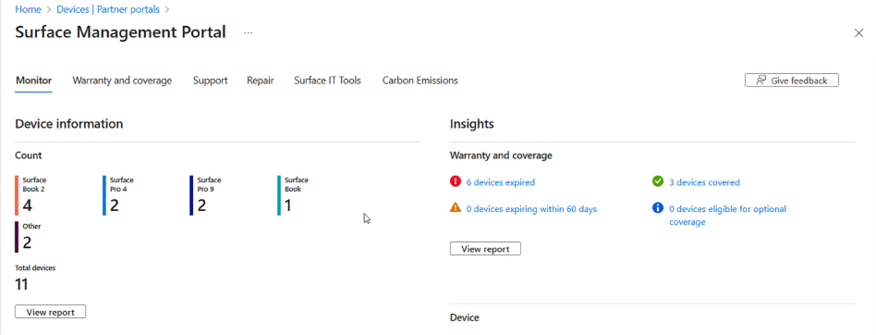
Figure 2.5: Microsoft Surface Management Portal
HP Connect
HP Connect is a cloud application designed to ease the management of UEFI BIOS on supported HP systems. HP Connect has a framework for developing BIOS management policies that are published to Microsoft Intune. HP Connect creates the policies and Intune executes them as remediation scripts. HP Connect requires a valid Microsoft Entra ID subscription and Microsoft Intune as the registered MDM. HP Connect interfaces directly with a customer’s Entra ID tenant for access to device groups and publishing BIOS policies as a cloud application.
Figure 2.6: HP Connect
You need to click Get started to start the integration process. Sign in with an admin user who has the correct role-based access in Entra ID to consent to a new Entra ID app in your organization.
Figure 2.7: HP Connect
You need to accept the terms and conditions from HP to continue the integration.
Figure 2.8: HP Connect terms and conditions
HP Connect is a cloud-based application engineered to simplify the administration of UEFI BIOS on compatible HP commercial systems. It possesses a structure for formulating BIOS management policies concerning authentication, updates, and settings, which are disseminated to Microsoft Intune device groups. While HP Connect is responsible for policy creation, Intune carries out these policies as proactive compliance rectifications.
In other words, HP Connect for Intune enables IT administrators to manage the BIOS configuration of HP commercial systems using Microsoft Intune. It simplifies the process of deploying firmware updates and managing BIOS configuration and ensures that the devices are compliant with the organization’s hardware security policies.
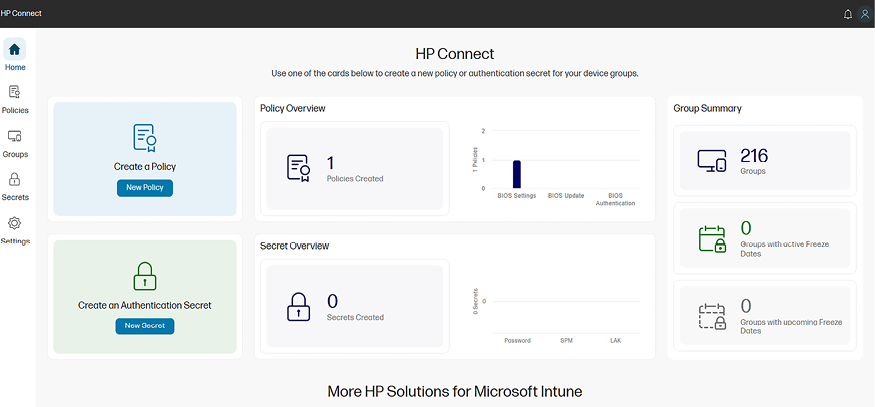
Figure 2.9: HP Connect for Microsoft Intune
You can create a policy in HP Connect that deploys a specific HP EliteBook BIOS version. Use the sample screenshot below as a pointer to get started with your HP EliteBook BIOS updates.
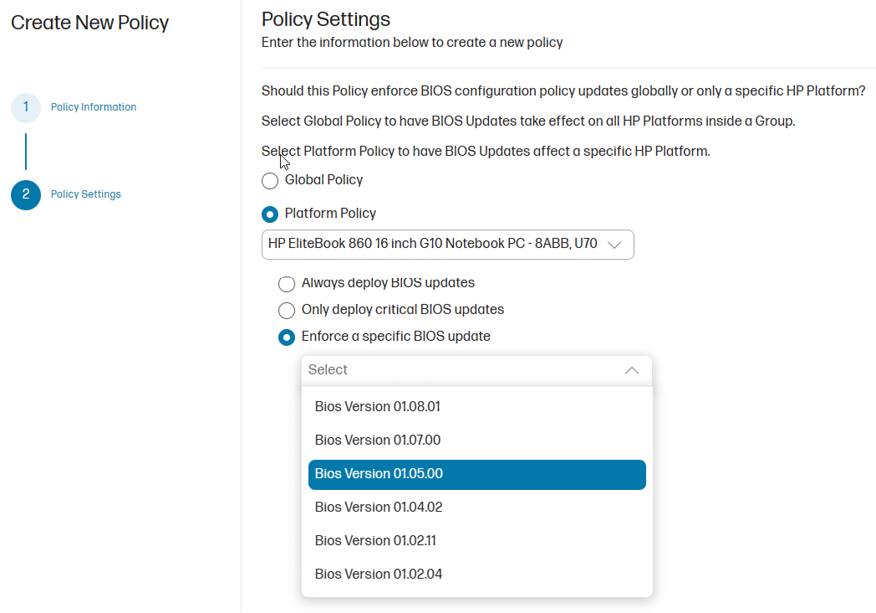
Figure 2.10: HP Connect policy for specific BIOS versions
There are three types of BIOS update policies supported by HP Connect:
- Always deploy BIOS updates: When implemented on a set of supported platforms, Intune will employ the policy as a compliance measure to track and update each device in the chosen group whenever a BIOS update is launched that corresponds to a device within the group.
- Only deploy critical BIOS updates: This policy will apply for a new BIOS release if it is marked as “Critical” by HP to every matched device in the selected group.
- Enforce a specific BIOS update: This policy will apply a BIOS update to a matching device in a device group based on a defined criteria/rule. The policy is applied to the specified platform only.
Policy settings created in HP Connect for Intune will show up as remediation scripts inside Microsoft Intune.
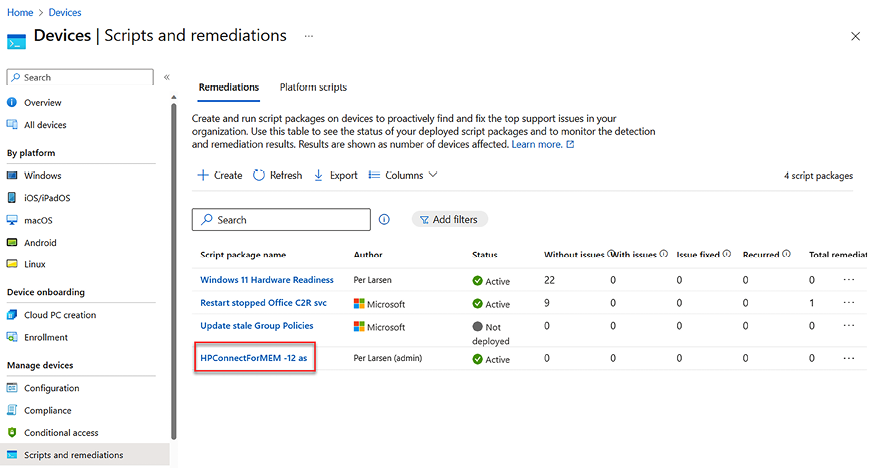
Figure 2.11: HP Connect remediation scripts
Learn more at https://connect.admin.hp.com/static/HPConnectUserGuide.pdf.
This concludes the section on the Intune Partner portal. In the next section, we will cover Windows 365.
Windows 365
Windows 365 is the ideal solution if you’re seeking a streamlined approach to operating your Windows PCs in the cloud. It reduces costs and simplifies your environment as you deploy and manage virtual endpoints in Microsoft Intune, with no need for extra Virtual Desktop Infrastructure (VDI) expertise or resources.
Windows 365 is a comprehensive SaaS service that securely provides a personalized Windows desktop, apps, settings, and content from the Microsoft cloud to any device, marking a new era in PC accessibility.
Microsoft’s unique offering, a cloud PC, coexists alongside traditional physical PCs, providing an end-to-end solution with unified management through Microsoft Intune. This means that it’s an end-to-end solution where customers can leverage the power from a computer from the cloud, with the same management tools to manage their physical and cloud PCs (Microsoft Intune admin portal).
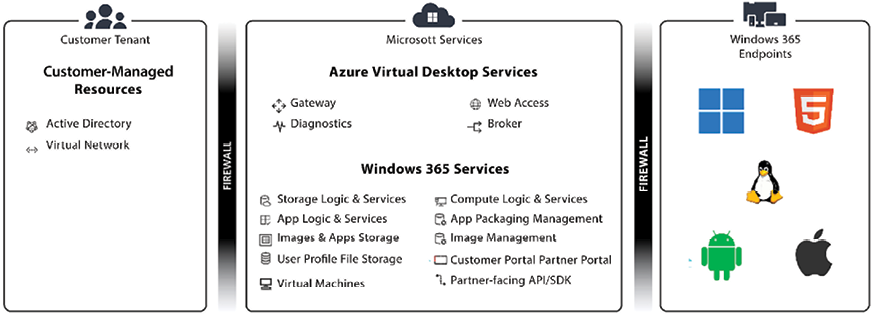
Figure 2.12: AVD and cloud PC overview
More information about Windows 365 will follow later in this book. In the next section, we will cover Microsoft Entra ID.
Microsoft Entra ID
Microsoft Entra ID serves as the identity provider and access management service for Microsoft Intune; this means that users and groups always are managed in Entra. Microsoft Intune then manages your MDM-enrolled devices and assigns apps and configurations to groups of users and/or devices, enabling advanced Conditional Access capabilities such as Multi-Factor Authentication (MFA) and compliance-based filtering. With Entra ID Premium, you can incorporate several additional features to safeguard devices, apps, and data, including dynamic groups, automatic enrollment, and Conditional Access.
Configuration Manager is an on-premises management solution for managing desktops, servers, and laptops that are either network based or internet based. It can be cloud enabled to integrate with Intune, also referred to as co-management or tenant attached, Entra ID, Microsoft Defender for Endpoint, and other cloud services. Configuration Manager can be used to deploy apps, software updates, and Operating Systems (OSs). It also allows for compliance monitoring, real-time client querying and action, and much more.
Even as an on-premises product, Configuration Manager has a biannual update cycle with a built-in semi-automatic update process tool, eliminating the need for you to search for, download, and install updates for your Configuration Manager.
This concludes the overview section of Microsoft Entra ID. In the next section, we will cover the benefits of Configuration Manager Cloud Management Gateway.
Cloud Management Gateway
Cloud Management Gateway (CMG) offers a straightforward method for managing Configuration Manager clients via the internet. You set up the CMG as a cloud service in Microsoft Azure, which allows you to manage clients that are internet-roaming or located in branch offices across the WAN, without the need for additional on-site infrastructure or exposing your on-premises infrastructure to the internet.
Co-management is a system that merges your existing on-premises Configuration Manager environment with the cloud, utilizing Intune and other Microsoft 365 cloud services. You have the option to designate either Configuration Manager or Intune as the management authority for seven distinct workload groups.
As a component of Intune, co-management leverages cloud features, including Conditional Access. Some tasks remain on-premises, while others are executed in the cloud with Intune.
Co-management supports the following workloads:
- Compliance policies
- Windows Update policies
- Resource access policies
- Endpoint protection
- Device configuration
- Office Click-to-Run apps
- Client apps
Compliance policies
Compliance policies establish the regulations and configurations that a device must adhere to in order to be deemed compliant with Conditional Access policies. Additionally, compliance policies can be used to track and rectify compliance problems with devices independently of Conditional Access, starting with the Configuration Manager assessment rule.
Windows Update policies
Windows Update for Business (WUfB) policies let you configure WUfB policies into a ring concept so you can decide when and how you service Windows 10 and later devices.
You can set up deferral policies for Windows feature updates or quality updates for Windows 10 and later devices managed directly by WUfB. In Intune, you also have the option to configure Windows feature updates. This policy allows you to specify the Windows version to which a device should be updated, preventing it from upgrading to a newer Windows feature release.
The Windows feature build specified in the Windows 10 and later feature updates policies will remain on the device until you choose to change the policy settings. While the feature build remains static, devices will continue to download and install quality and security updates available for that feature build.
Resource access policies
Resource access policies configure Virtual Private Network (VPN), Wi-Fi, email, and certificate settings on Windows 10 and later devices.
Endpoint protection
The endpoint protection workload includes the Windows Defender suite of anti-malware protection features, such as antivirus and disk encryption.
Antivirus policies help security admins manage the settings for Microsoft Defender Antivirus, Microsoft Defender exclusions, and the Windows Security experience as a policy for Intune-managed devices.
Endpoint security disk encryption profiles focus on the settings relevant to a device’s built-in encryption method, such as BitLocker, allowing IT admins to deploy and automatically encrypt end users’ Windows devices. This includes BitLocker and Personal Data Encryption (PDE).
PDE is a data protection feature that encrypts select folders and their contents on PDE-deployed devices. PDE utilizes Windows Hello for Business to link data encryption keys with user credentials. This feature can minimize the number of credentials the user has to remember to gain access to content. Users will only be able to access their PDE-protected content once they’ve signed into Windows using Windows Hello for Business.
BitLocker drive encryption is a data protection feature that integrates with the OS and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers. Did you know that you can view the encryption status of all managed devices in the encryption report (Devices | Monitor | Encryption Report). This includes the status of encryption on the device and encryption readiness and it shows if any prerequisites are missing or if there are errors related to encryption on devices.
When integrating Microsoft Defender for Endpoint with Intune, you can use endpoint security policies for Endpoint Detection and Response (EDR) to manage EDR settings and onboard devices for Microsoft Defender for Endpoint:
- Firewall: You can use the endpoint security firewall policy in Intune to configure the built-in firewall on devices running Windows 10. Firewall policies are divided into two parts: the firewall policy itself and a firewall rule policy.
- Endpoint detection and response: When integrating Microsoft Defender for Endpoint with Intune, you can use endpoint security policies for EDR to manage EDR settings and onboard devices for Microsoft Defender for Endpoint.
- App Control for Business: This is a security practice that restricts unauthorized applications from executing in ways that put data at risk. It is a crucial aspect of endpoint security that helps businesses to only permit trusted applications to be installed and launched on their computer systems and networks.
- Attack surface reduction: If Defender Antivirus is in use on your Windows 11 or Windows 10 devices, use Intune endpoint security policies for attack surface reduction to manage those settings for your devices.
The attack surface reduction policy is divided into different policies:
- App and browser isolation
- Device control rules
- Device control
- Exploit protection
- Web protection for Microsoft Edge Legacy
- Application control
- Attack surface reduction rules
- Account protection: Account protection policies help to protect the identity and accounts of your users:
- Windows Local Administrator Password Solution (Windows LAPS)
- Local user group membership
- Account protection
Windows LAPS is a Windows feature that automatically manages and backs up the password of a local administrator account on your Entra ID joined or Windows Server Active Directory (AD) joined devices.
Local user group membership policies help to add, remove, or replace members of local groups on Windows devices.
Account protection policies help protect user credentials by using technology such as Windows Hello for Business and Credential Guard.
If you switch the endpoint protection workload, the Configuration Manager policies remain on the device until they are overwritten by Intune policies or are removed by an IT admin. This ensures that the device remains protected during the transition. The same behavior applies when switching the device configuration workload, which includes policies for the Windows Information Protection feature, not included in the endpoint protection workload.
It is important to note that the Microsoft Defender Antivirus settings, which are part of the device restrictions profile type for Intune device configuration, are not included in the scope of the endpoint protection slider. To manage Microsoft Defender Antivirus for co-managed devices with the endpoint protection slider enabled, use the new antivirus policies in the Microsoft Intune admin center under Endpoint security | Antivirus. This new policy type offers new and improved options and supports all the same settings available in the device restrictions profile.
The Windows encryption feature includes BitLocker management. We will talk more about BitLocker in Chapter 10, Advanced Policy Management, and Chapter 13, Identity and Security Management.
Device configuration
The device configuration workload encompasses the settings that are managed for devices within your organization. When this workload is switched, it also transfers the resource access and endpoint protection workloads.
You can still deploy settings from Configuration Manager to co-managed devices even though Intune is the device configuration authority. This exception might be used to configure settings that your organization requires but aren’t yet available in Intune. Specify this exception on a Configuration Manager configuration baseline. Enable the option to always apply this baseline even for co-managed clients when creating the baseline. You can change it later in the General tab of the properties of an existing baseline.
Office Click-to-Run apps
This workload manages Microsoft 365 apps on co-managed devices. Remember that when moving Microsoft 365 apps from Microsoft Intune for devices already managed by Configuration Manager, adjustments are made. These changes ensure that the Windows client is aware of deploying any Microsoft 365 Enterprise app assigned through Microsoft Intune. By shifting the workload, you do not automatically change the Microsoft 365 app update behavior on the client, but the client will not receive Office updates from Configuration Manager anymore. So, to keep your Microsoft 365 apps updated you need to shift to cloud updates from a Content Delivery Network (CDN). Updates can be managed using the settings catalog in Microsoft Intune, Windows Autopatch, or cloud update in the Microsoft 365 Apps admin center.
Office updates may take around 24 hours to show up for clients unless the devices are restarted.
Microsoft 365 Enterprise applications are managed by Intune. This condition in Intune is added by default as a requirement for new Microsoft 365 applications. When you transition this workload, co-managed clients don’t meet the requirements of the application, and then they don’t install Microsoft 365 deployed via Configuration Manager.
After moving the workload, Microsoft 365 apps assigned from Microsoft Intune show up in the company portal on the device.
Client apps
Use Intune to manage client apps on co-managed Windows devices. After you transition this workload, any available apps deployed from Intune are available in the company portal. Apps that you deploy from Configuration Manager are available in the software center and company portal. The company portal can show both SCCM and Intune available apps as one end user software portal.
Windows Autopilot sets up and preconfigure new devices, getting them ready for use. It is designed to simplify the life cycle of Windows devices, for both IT and end users, from initial deployment through to end of life.
As a part of Intune, you can use Autopilot to preconfigure devices and automatically enroll devices in Intune. You can also integrate Autopilot with Configuration Manager and co-management for more complex device configurations (in preview).
It is highly recommended to use Windows Autopilot in Entra ID-only environments to take advantage of the entire suite of Windows Autopilot features, such as Autopilot reset and co-management in Autopilot.
Entra ID is a service used by Intune to identify devices, users, groups, and MFA. Entra ID Premium, which is included in the Microsoft 365 license, offers additional features to help protect devices, apps, and data. These features include dynamic groups, automatic enrollment, and Conditional Access. Entra ID Premium is also required for Windows Autopilot, as automatic enrollment is a prerequisite.
Intune admin center is a centralized website for creating policies and managing your devices. It integrates with other key device management services, including groups, security, Conditional Access, and reporting. Microsoft Intune is a comprehensive solution for managing all of your devices, bringing together Configuration Manager and Intune into a single console known as the Microsoft Intune admin center.
Starting in Configuration Manager version 2002, you can upload your Configuration Manager devices to the cloud service and take action from the Devices blade in the admin center:
- Client details: This feature gives the IT admin or helpdesk a fast overview of properties and the state of devices.
- Install applications: This feature gives the IT admin or helpdesk the option to deploy an application to the end users’ devices.
- Device timeline: Devices send events once a day to the admin center. Only events collected after the client receives the Enable Endpoint analytics data collection policy are visible in the admin center. Generate test events easily by installing an application or an update from Configuration Manager or restarting the device. Events are kept for 30 days. Use the chart to view events that are collected.
- Resource Explorer: From the Microsoft Endpoint Management admin center, you can view the hardware inventory for uploaded Configuration Manager devices by using Resource Explorer.
- Run scripts: This option allows additional IT admins or the helpdesk to run PowerShell scripts from the cloud against an individual Configuration Manager-managed device in real time. This provides all the traditional benefits of PowerShell scripts that have already been defined and approved by the Configuration Manager admin in the on-premises environment.
Enabling tenant attach has no end user impact without the IT admin creation policies and deploying them to their devices.
Microsoft Intune – from on-premises to the cloud
The unified endpoint management journey is different for each customer. Some customers will already be using some components of Microsoft Intune, so the migration is relatively easy:
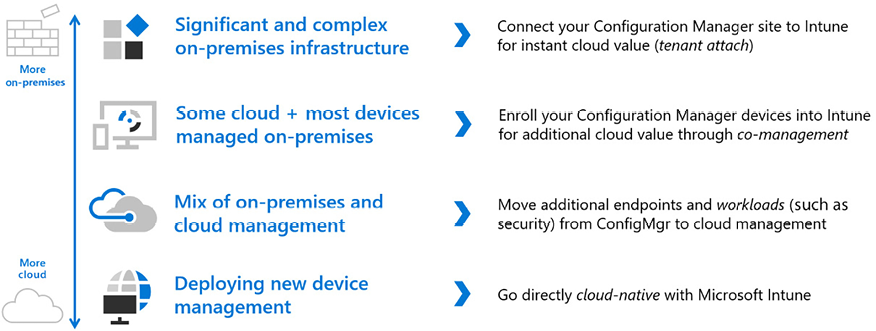
Figure 2.13: Microsoft Intune – on-premises-to-cloud flow
If you are still using complex on-premises infrastructures, the work to move to the cloud could be a bit more intense. That workload is fully dependent on the complexity of your current environment.
























































