Some of the key areas that impact security are show in this diagram:
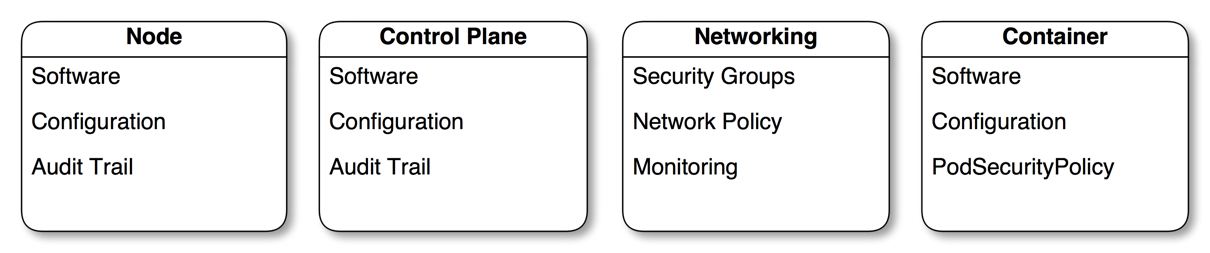
Securing the configuration and software that forms the infrastructure of your cluster is of vital importance, especially if you plan to expose the services you run on it to the internet.
You should consider that if you expose services to the public internet that have well known software vulnerabilities or configuration errors, it may only be a matter of hours before your services are detected by automated tools being used to scan for vulnerable systems.
It is important that you treat the security of your cluster as a moving target. This means that you, or a tool that you use, need to be aware of new software vulnerabilities and configuration vulnerabilities.
Vulnerabilities with the Kubernetes software, and with the underlying operating system software of your hosts, will be updated and patched by the...











































































