Reinstalling WordPress
Even if you have found and solved your trials and tribulations, it is often best to bite the bullet and reinstall the platform. This can help to remove any outstanding backdoors.
For those wanting to diagnose problems offsite and at length or to spend more time delving into server troubles then this, too, helps to minimize downtime in the meantime.
Some provisos
Before reinstalling, here are some important provisional questions to consider.
Might any privileged user passwords be in the wrong hands?
The answer is yes. Before again accessing the server and uploading files, now is a good time to change some passwords for you and other users:
Server control panel
MySQL database
WordPress (Super) Administrators and Editors
Can I rely on the security of my web connection?
There is no good reason to risk using FTP, so set up the SFTP alternative or use an SSH connection instead. If you really, really must use FTP, change the password. If you're wondering why these protocols are better, you need to read Chapter 5. Have fun!
Has the core WordPress platform been adapted, perhaps by a web developer?
Sometimes, for example, non-theme functionalities are customized, perhaps to work with other applications. Carefully screen, copy and paste any such chunks of code or, better yet, hopefully there is a nice clean master copy of the bespoke platform to reinstall from.
Upload WordPress and plugins
Create a new directory alongside your existing WordPress root folder, calling it something like wordpress_NEW and upload the latest version into there. Now upload fresh copies of all your required plugins into the new wp-content/plugins directory.
Next is your theme, noting that the use of these files from the old compromised site is undesirable. Ideally use instead a reliable backup or an original source, perhaps appending that with any heavily scrutinized adapted files, such as your functions.php.
Finally, add whatever other files and media your site relies on:
htaccess files
robots file
sitemap file
Favicon image
Uploaded media
Custom files
In the case of htaccess files, you can reuse old ones, but scour them as has just been explained.
For files in the uploads, cgi-bin and FTP folders, backdate these with assuredly clean originals and, for any given file, zip or whatever, if you don't absolutely need it, weed it!
Importing a database backup
As with your web files, the only way to ensure that the database is clean is to create a new one, importing a recent uninfected backup into it.
For busy sites, this can be a hard pill to swallow. You'll have to weigh up the cost of losing (and perhaps, later, manually adding back) data, against the risk that your database has been infiltrated. In those cases, you may consider gambling with the existing database and, if problems reoccur, backdating to a clean copy.
Editing wp-config-sample.php
Edit the wp-config-sample.php file in the new root WordPress folder, providing your database credentials, allowing for changes such as to the table prefix and copying any other bespoke settings such as for SSL access from your old wp-config.php file (which lives in the original WordPress root directory).
Do use secret keys but don't recycle your old ones, which may return Dashboard access to a hacker. Generate afresh at https://api.wordpress.org/secret-key/1.1/salt as explained in Chapter 6.
Finally, rename wp-config-sample.php to wp-config.php.
Setting least privileges
As a general default, ensure permissions are set to 644 for files and 755 for folders.
Sending the clean platform live
To do this, simply rename the original WordPress directory to something like wordpress_INFECTED and then wordpress_NEW to wordpress (or to whatever name the original root directory was called).
Browse to the site and test the basic functionality, checking against the problem you had. Go to the Dashboard's Updates page to upgrade old code and then activate your plugins. When you're happy everything's hunky-dory, delete the
wordpress_INFECTED folder.
Changing your passwords
Yes, do this again but, this time, for all users. If you have lots of users, this could take some time. Cue a superb time-saving plugin (which needs a little TLC but it's worth it).
Ruben Woudsma's Bulk Password Reset (BPR) can force a password reset for any user group.
Note
Strictly speaking, BPR supports WordPress only up to 2.9.2 and an error may be produced on the Options page. There's a simple workaround that tests true at http://wordpress.org/support/topic/bulk-password-reset-error.
Once used, to be safe, delete the sucker due to the lack of maintenance.
When activated, set your options by clicking through the new Bulk Password Reset tab under the Users menu on the Dashboard. (Guess you knew that!) Here's a look-see (edited to save space):
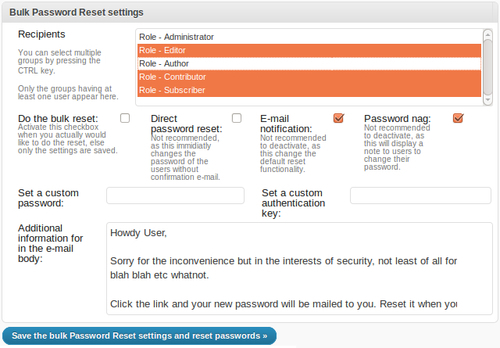
Each user is sent a unique scrambled key that they can later change if they want to:
Checking your search engine results pages
Have a flick around the major search engines to check for your site. If your site has been dropped from results pages, perhaps because you were too slow to cut out spam links, make a request for reconsideration. Google has a special grovel form, for example, included with their valuable Webmaster Tools:
Google Pretty-Please – https://www.google.com/webmasters/tools/reconsideration
Revisiting WordPress security
Now would be a good idea to have another thumb through this book, being as thorough as you can, but starting with the WordPress hardening tips in Chapters 6 and 7.
Finally, and for some of us most importantly, pop on the kettle and have a nice cup of tea. Then again, make that a brandy and maybe a double. You've earned it.































































