Working examples – listing the services
So we have covered what OpenStack is, the services that make up OpenStack, and some of the key features of OpenStack. It is only appropriate to show a working example of the OpenStack functionality and the methods available to manage/administer your OpenStack cloud.
To re-emphasize, OpenStack management, administration, and consumption of services can be accomplished via either an API, CLI, and/or web dashboard. When considering some level of automation, the last option of the web dashboard is normally not involved. So for the remainder of this book, we will solely focus on using the OpenStack APIs and CLIs.
Listing the OpenStack services
Now, let's take a look at how you can use either the OpenStack API or CLI to check for the available services active within your cloud.
Via API
The first step in using the OpenStack services is authentication against Keystone. You must always first authenticate (tell the API who you are) and then receive authorization (API ingests your username and determines what predefined task(s) you can execute) based on what your user is allowed to do. That complete process ends in providing you with an authentication token.
Tip
Keystone can provide four different types of token formats: UUID, fernet, PKI, and PKIZ. A typical UUID token looks like this 53f7f6ef0cc344b5be706bcc8b1479e1. Most do not use the PKI token as it is a much longer string and harder to work with. There are great performance benefits from using fernet tokens instead of UUID due to not requiring persistence. It is suggested to set Keystone to provide fernet tokens within your cloud.
Here is an example of making an authentication request for a secure token. Making API requests using cURL, a useful tool for interacting with RESTful APIs, is the easiest approach. Using cURL with various options, you are able to simulate actions similar to using the OpenStack CLI or the Horizon dashboard:
$ curl -d @credentials.json -X POST -H "Content-Type: application/json"
http://127.0.0.1:5000/v3/auth/tokens | python -mjson.tool
Tip
Because the credential string is fairly long and easy to incorrectly manipulate, it is suggested to use the -d @<filename> functionality part of cURL. This allows you to insert the credential string into a file and then be able to pass it into your API request by just referencing the file. This exercise is very similar to creating a client environment script (also known as OpenRC files).
Adding | python -mjson.tool to the end of your API request makes the JSON output easier to read.
An example of the credential string would look like this:
{
"auth": {
"identity": {
"methods": [
"password"
],
"password": {
"user": {
"name": "admin",
"domain": {
"id": "default"
},
"password": "passwd"
}
}
}
}
}
Tip
Downloading the example code
Detailed steps to download the code bundle are mentioned in the Preface of this book.
The code bundle for the book is also hosted on GitHub at: https://github.com/PacktPublishing/OpenStack-Administration-with-Ansible-2. We also have other code bundles from our rich catalog of books and videos available at: https://github.com/PacktPublishing/. Check them out!
When the example is executed against the Keystone API, it will respond with an authentication token. The token is actually returned within the HTTP header of the response. That token should be used for all subsequent API requests. Keep in mind that the token does expire, but traditionally, a token is configured to the last 24 hours from the creation timestamp.
As mentioned earlier, the token can be found in the HTTP header of the API response message. The HTTP header property name is X-Subject-Token:
HTTP/1.1 201 Created
Date: Tue, 20 Sep 2016 21:20:02 GMT
Server: Apache
X-Subject-Token: gAAAAABX4agC32nymQSbku39x1QPooKDpU2T9oPYapF6ZeY4QSA9EOqQZ8PcKqMT2j5m9uvOtC9c8d9szObciFr06stGo19tNueHDfvHbgRLFmjTg2k8Scu1Q4esvjbwth8aQ-qMSe4NRTWmD642i6pDfk_AIIQCNA
Vary: X-Auth-Token
x-openstack-request-id: req-8de6fa59-8256-4a07-b040-c21c4aee6064
Content-Length: 283
Content-Type: application/json
Once you have the authentication token, you can begin crafting subsequent API requests to request information about your cloud and/or execute tasks. Now we will request the list of services available to your cloud:
$ curl -X GET http://127.0.0.1:35357/v3/services -H
"Accept: application/json" -H "X-Auth-
Token: 907ca229af164a09918a661ffa224747" | python -mjson.tool
The output from this API request will be the complete list of services registered within your cloud by name, description, type, id, and whether it is active. An abstract of the output would look similar to the following code:
{
"links": {
"next": null,
"previous": null,
"self": "http://example.com/identity/v3/services"
},
"services": [
{
"description": "Nova Compute Service",
"enabled": true,
"id": "1999c3a858c7408fb586817620695098",
"links": {
"...
},
"name": "nova",
"type": "compute"
},
{
"description": "Cinder Volume Service V2",
"enabled": true,
"id": "39216610e75547f1883037e11976fc0f",
"links": {
"...
},
"name": "cinderv2",
"type": "volumev2"
},
...
Via CLI
All the base principles applied to using the API earlier also applies to using the CLI. The major difference is with the CLI all you need to do is create an OpenRC file with your credentials and execute defined commands. The CLI handles formatting the API calls behind the scenes, grabbing the token for subsequent requests, and formatting the output also.
Same as earlier, first you need to authenticate against Keystone to be granted a secure token. This action is accomplished by first sourcing your OpenRC file and then by executing the service-list command. The next example will demonstrate it in more detail. Now that there are two active versions of the Keystone service, version 2.0 and 3.0, you have the choice of which version you wish to have active to handle authentication/authorization.
Here is an example of an OpenRC file v2.0 named openrc:
# To use an OpenStack cloud you need to authenticate against keystone. export OS_ENDPOINT_TYPE=internalURL export OS_USERNAME=admin export OS_TENANT_NAME=admin export OS_AUTH_URL=http://127.0.0.1:5000/v2.0 # With Keystone you pass the keystone password. echo "Please enter your OpenStack Password: " read -sr OS_PASSWORD_INPUT export OS_PASSWORD=$OS_PASSWORD_INPUT
The OpenRC file v3.0 would look similar to this:
# *NOTE*: Using the 3 *Identity API* does not necessarily mean any other # OpenStack API is version 3. For example, your cloud provider may implement # Image API v1.1, Block Storage API v2, and Compute API v2.0. OS_AUTH_URL is # only for the Identity API served through keystone. export OS_AUTH_URL=http://172.29.238.2:5000/v3 # With the addition of Keystone we have standardized on the term **project** # as the entity that owns the resources. export OS_PROJECT_ID=5408dd3366e943b694cae90a04d71c88 export OS_PROJECT_NAME="admin" export OS_USER_DOMAIN_NAME="Default" if [ -z "$OS_USER_DOMAIN_NAME" ]; then unset OS_USER_DOMAIN_NAME; fi # unset v2.0 items in case set unset OS_TENANT_ID unset OS_TENANT_NAME # In addition to the owning entity (tenant), OpenStack stores the entity # performing the action as the **user**. export OS_USERNAME="admin" # With Keystone you pass the keystone password. echo "Please enter your OpenStack Password: " read -sr OS_PASSWORD_INPUT export OS_PASSWORD=$OS_PASSWORD_INPUT # If your configuration has multiple regions, we set that information here. # OS_REGION_NAME is optional and only valid in certain environments. export OS_REGION_NAME="RegionOne" # Don't leave a blank variable, unset it if it was empty if [ -z "$OS_REGION_NAME" ]; then unset OS_REGION_NAME; fiOnce you create and source the OpenRC file, you can begin using the CLI to execute commands such as requesting the list of services. Take a look at the following working example:
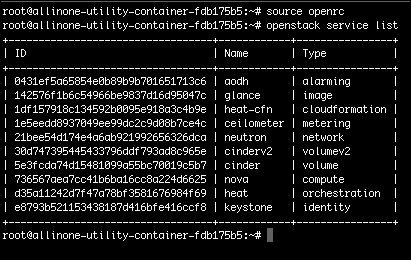
$ source openrc $ openstack service list
The output will look similar to this: