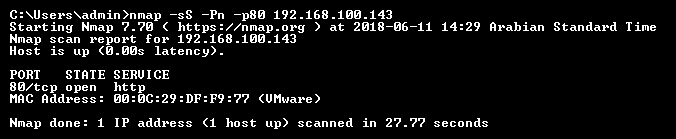
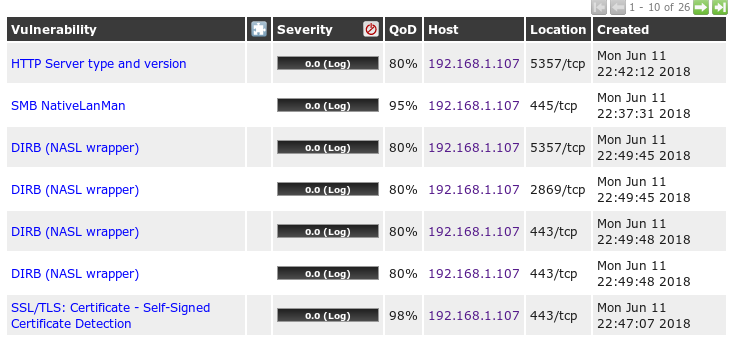
A vulnerability is a weakness present in a system or device that is exposed to a possibility of being attacked. Network Vulnerability Scanning is a process of looking into identifying and detecting vulnerabilities in the network components such as clients, servers, network devices, and endpoints, using various automated or manual tools and techniques. It can be broadly classified into two types: internal network vulnerability scan and external network vulnerability scan.
The internal and external vulnerability scans share a similar process, but differ in the network placement of the scan appliance or the system. An external vulnerability scan has a scope to identify loopholes with a perspective of the attacker being over the internet and targeting the network through public IP addresses of the network, whereas an internal vulnerability scan operates considering the attacker to be an insider with access to the internal network and targeting the network through private IP addresses. Identifying both internal and external threats is very important for any computer network, to create a real-time picture of how secure the network is, based on the number of vulnerabilities identified.
The vulnerability scans have their own side effects on the networks, such as an increase in network latency caused by the increase in traffic, unresponsive network resources, and rebooting of devices and servers. Thus, all internal network scans within the organization should be performed with the utmost care and proper approvals. In general, there are two types of scanning techniques that can be used, authenticated and unauthenticated. We will see the recipes for these scan types in Chapter 4, Vulnerability Scanning, and Chapter 5, Configuration Audit.
Beginners always confuse the Vulnerability Scan with the penetration test. The Vulnerability Scan is a preliminary step to identify the hosts on which you can perform a penetration test. For example, as a part of a vulnerability scan you identify that port 80 is open on a server and is susceptible to Remote Code Execution (RCE) attacks. For a penetration test, this information will be input as you already know that the server is vulnerable to RCE and will try to perform the attack and compromise the server.
Before performing a Network Vulnerability Scan, it is always recommended to inform the stakeholders and obtain downtime if required based on how critical the servers and the data hosted on the servers are. It is a good practice to write an email before beginning the scan and after completion of the scan as this would help the respective teams to check the continuity of the service.
We will have a look at many recipes in further chapters of this cookbook to understand the various best practices to be followed during a Network Vulnerability Scan.