Building a verification lab
As a penetration tester, it is recommended to set up your own verification lab to test any kind of vulnerabilities and have the right proof of concept before emulating the same conditions on a live environment.
Installing defined targets
In order to practice the art of exploitation, it is always recommended to make use of well-known vulnerable software. In this section, we will be installing Metasploitable3, which has both Windows and Linux versions; Mutillidae, which is a PHP framework web application; and we will also utilize CloudGoat, an AWS deployment tool designed to deploy vulnerable AWS instances.
Lab Network
We need to ensure that we create a separate network that can be accessed only by testers—hence, we are going to create a NAT network within VirtualBox by running the following command from the Command Prompt or Terminal, respective of the directory; for Windows, it is C:\Program Files\Oracle\VirtualBox\:
VBoxManage natnetwork add --netname InsideNetwork --network "10.10.10.0/24" –-enable --dhcp on
Note that this is a single line of code.
Active Directory and Domain Controller
In the previous edition, we discussed how to set up the Active Directory on Windows 2008 R2; in this section, we will upgrade our test lab and install Active Directory on Windows Server 2016 Datacenter. Once the ISO from Microsoft (https://www.microsoft.com/en-us/evalcenter/evaluate-windows-server-2016-essentials) is downloaded and the operating system on VMware Workstation Player or VirtualBox is installed, you should be able to perform the following steps:
- Ensure the Network adapter is connected to the right network. Select the virtual machine and click Settings. Then, from the menu, click on Network, ensure that Enable network adapter is checked and that Attached to is selected as NAT network, and that the name is InsideNetwork (or the name you used to create the lab network). Additionally, click on Advanced and select Allow All under Promiscuous mode (this mode will allow all traffic between the VMs).
- Upon successfully logging into the Windows server, set a static IP to this server by running the following in the command line:
netsh interface ip set address "ethernet" static 10.10.10.100 255.255.255.0 10.10.10.1 - From Server Manager, click on Add roles and features.
- Select Role-based or Features-based installation from the Installation Type
screenand click Next. - By default, the same server will be selected from Select a server from the server pool; click Next.
- From the Server Roles page, place a checkmark in the checkbox next to Active Directory Domain Services. Additional roles, services, or features are also required to install Domain Services: click Add Features and click Next.
- Select optional features to install during the AD DS installation by placing a check in the box next to any desired features, and then click on Next.
- That should take us to the confirmation screen with all the selected features and services; click on Install and, when the installation is complete, click on Close.
- Select AD DS; it should come up with a warning stating:
Configuration required for active directory domain service. Now click on More for post-deployment configuration, which should bring us to Figure 1.31:
Figure 1.31: Promoting the server to a domain controller
- Click on Promote this server to a domain controller.
- Select Add a new Forest and enter the Fully Qualified Domain Name (FQDN). In this example, we will create a new FQDN called
mastering.kali.fourthedition. Then click Next. - On the next screen, for both Forest functional level and Domain functional level, select Windows Server 2016 and type the password for Directory Services Restore Mode (DSRM); click Next.
- Do not select the DNS delegation—directly click on Next, where it should pick up the NetBIOS domain name as MASTERING. Click Next.
- Select the locations for the database, log files, and SYSVOL for Active Directory, and finally, you should be presented with a review screen, as shown in Figure 1.32; click Next:

Figure 1.32: Final stage of installation of Active Directory server on Windows Server 2016
- All the prerequisites must be met. Ignore the warnings; after this, click on Install.
- On the Confirm installation selections screen, review the installation and then click Install. Doing so should reboot the system and a new Active Directory server with a domain controller should have been established.
To create a normal user on the domain, run the following command in the command line on the domain controller:
net user normaluser Passw0rd12 /add /domain
To create a domain administrator account, the following commands will create such a user and add it to the domain admins group:
net user admin Passw0rd123 /add /domain
net group "domain admins" admin /add /domain
To validate whether these users have been created, you can use the domain controller by simply running net user from the command line; you should be able to see all the local users on the server.
We will also be creating an additional user for the new exchange server by running the following commands on our domain controller:
net user exchangeadmin Passw0rd123 /add /domain
net group "domain admins" exchangeadmin /add /domain
net group "Schema admins" exchangeadmin /add /domain
net group "Enterprise admins" exchangeadmin /add /domain
Installing Microsoft Exchange Server 2016
In this section, we will set up a completely new Windows Server 2016 and install the Microsoft Exchange service on it. This is to explore some of the Exchange Server 2021 vulnerabilities that we will explore in later chapters.
We will utilize the same Windows 2016 ISO that we downloaded for the Active Directory installation and create a brand new server. Once the Windows Server is installed and booted up, the first step is to make sure that this server can now be communicated to the DNS service of the Domain Controller; hence, set up a static IP and DNS by running the following commands or manually by editing the Ethernet adapter settings (https://www.server-world.info/en/note?os=Windows_Server_2016&p=initial_conf&f=4):
netsh interface ip set address "ethernet" static 10.10.10.5 255.255.255.0 10.10.10.1
netsh interface ip add dns "Ethernet" 10.10.10.100
The next step is to set up Exchange Server to the domain. This can be achieved by doing the following:
- Go to System Properties. Press Windows Key + R and type
sysdm.cpl; click on Change, which should bring up the new screen of Computer Name/Domain Changes. - Change the computer name from the default to ExchangeServer and click on Domain; type
Mastering.kali.fourthedition, and if there is no problem with the network, then you should get a prompt asking you to enter your username and password. - Enter the username as previously created, called
exchangeadmin, with the password; you should now see the screen shown in Figure 1.33, showing that it was successfully attached to the domain. - The final step is to restart the computer for the change in computer name that the domain should now reflect to take place:

Figure 1.33: Successfully adding the exchange server to the Active Directory domain
The following steps will promote our normal Windows Server 2016 to an Exchange Server:
- Download the Microsoft Exchange Server 2016 image from https://www.microsoft.com/en-us/download/details.aspx?id=57827.
- Mount the ISO file to VirtualBox as a drive by navigating to Settings, Storage, and Select the Optical Drive, and add the exchange server ISO file.
- Before beginning the installation, we will install some prerequisites, which can be directly installed from PowerShell (run as administrator), as the following shows:
PS > Install-WindowsFeature NET-Framework-45-Features, RPC-over-HTTP-proxy, RSAT-Clustering, RSAT-Clustering-CmdInterface, RSAT-Clustering-Mgmt, RSAT-Clustering-PowerShell, Web-Mgmt-Console, WAS-Process-Model, Web-Asp-Net45, Web-Basic-Auth, Web-Client-Auth, Web-Digest-Auth, Web-Dir-Browsing, Web-Dyn-Compression, Web-Http-Errors, Web-Http-Logging, Web-Http-Redirect, Web-Http-Tracing, Web-ISAPI-Ext, Web-ISAPI-Filter, Web-Lgcy-Mgmt-Console, Web-Metabase, Web-Mgmt-Console, Web-Mgmt-Service, Web-Net-Ext45, Web-Request-Monitor, Web-Server, Web-Stat-Compression, Web-Static-Content, Web-Windows-Auth, Web-WMI, Windows-Identity-Foundation, RSAT-ADDS - Besides these packages, you will also need to download Unified Communications Managed API 4.0 Runtime from http://www.microsoft.com/en-us/download/details.aspx?id=34992 and install it.
- Once all the prerequisites are completed, locate the drive by typing
d:in the command line; then typesetup /PrepareSchema /IAcceptExchangeServerLicenseTerms. If no error occurs, then you should see the same screen as displayed in Figure 1.34:
Figure 1.34: Prerequisite checks to install Exchange Server
- Once all the prerequisite analysis has been completed, we can now move on to the next step by preparing our Active Directory by running the following command:
setup /Preparedomain /IAcceptExchangeServerLicenseTerms - As a final step, we will now install the
Mailboxrole on our exchange server by running the following command:setup /Mode:Install /Role:Mailbox /IAcceptExchangeServerLicenseTerms - This will lead to the successful installation of the required Exchange Server components and packages as shown in Figure 1.35:

Figure 1.35: Installation of Exchange Server tools and their configuration
- It may take some time, depending on the system performance. Once everything is complete, we should now have Outlook web access enabled on the Exchange Server on port
443, as shown in Figure 1.36:
Figure 1.36: Successful installation of Exchange Server, accessed at https://localhost/owa/
Metasploitable3
Metasploitable3 is an indubitably vulnerable Virtual Machine (VM) that is intended to be tested for multiple exploits using Metasploit. It is released under a BSD-style license. We will be utilizing two VMs, one VM running an obsolete Windows 2008 server and another running a Linux server Ubuntu 14.04, to practice within our lab network. You can achieve this setup by first installing the Vagrant application.
Vagrant is an open-source tool that is predominantly used for building and managing virtual machine environments. You can download this tool from https://www.vagrantup.com/downloads for your hosting operating system. Once the application is successfully installed, install the required plugins, vagrant-reload and vagrant-vbguest, by running the following commands in the Terminal or Command Prompt:
Vagrant plugin install vagrant-reload
Vagrant plugin install vagrant-vbguest
We are now ready to download the Metasploitable3 virtual machines to our local system. We will use the vagrant box add command along with the repository to download the virtual machines; these are hosted on vagrantcloud.com:
vagrant box add rapid7/metasploitable3-win2k8
vagrant box add rapid7/metasploitable3-ub1404
Running the preceding commands should provide you with the options to download using different providers, as shown in the following Figure 1.37:
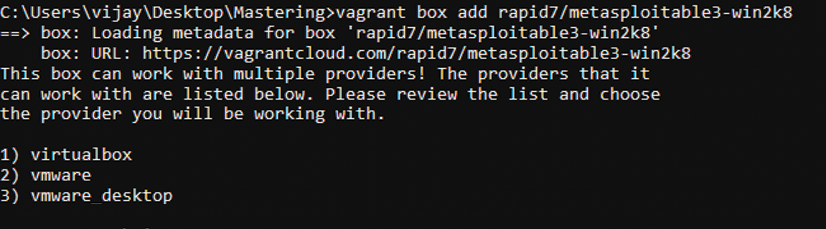
Figure 1.37: Downloading Metasploitable3 via vagrant
These virtual machines are downloaded to the /home/username/.vagrant.d/boxes/ or c:\users\username\.vagrant.d\boxes\ folder. Check these folders to verify the download:
- Change your folder to the respective location by running cd
C:\Users\user\.vagrant.d\boxes or cd /home/username/.vagrant.d/boxes/ - We can list the downloaded boxes that are installed on our device by running
vagrant box list. - To run these machines, we need to initialize them by running
vagrant init metasploitable3-win2k8. This command creates the required Vagrant configuration file namedVagrantfile, which includes all the virtual machine settings. Runvagrant init metasploitable3-ub1404from a different folder to avoid theVagrantfile already existserror message. - Finally, we will bring the virtual machine up by running
vagrant up. You should see the virtual machine up. Pentesters will receive the warningdefault: Warning: Authentication failure. Retrying, which is due to the insecure private key used for the SSH access between the VM and Vagrant. You should see the screen shown in Figure 1.38 upon successfully starting the Metasploitable3 windows server:
Figure 1.38: VirtualBox running metasploitable 3
- Validate the systems that are currently initialized by running vagrant
global-status. - The next important steps are to change the network settings of these VMs to connect them to our lab network. Select the virtual machine and click Settings. Within the General tab, change the Name of the VM to your desired name and, from the menu, click on Network. Ensure Enable network adapter is checked and Attached to is selected as NAT network and the name is InsideNetwork.
We have successfully deployed the vulnerable Metasploitable3 VMs in our VirtualBox environment, which we will be utilizing to conduct more advanced exploitations in the coming sections.
Mutillidae
Mutillidae is an open-source insecure web application designed for penetration testers to practice all of the web app-specific vulnerability exploitation. XAMPP is another such free and open-source cross-platform web server solution stack package that can be used, developed by Apache Friends.
We will now install Mutillidae on our newly installed Microsoft Windows Server 2016 (domain controller) server to host it:
- You can either download XAMPP directly from https://www.apachefriends.org/download.html or run the following command in PowerShell:
wget https://downloadsapachefriends.global.ssl.fastly.net/7.3.28/xampp-windows-x64-7.3.28-1-VC15-installer.exe?from_af=true -OutFile XAMPP-Installer.exeIn case of any SSL/TLS errors while running
wgetin PowerShell, ensure you run the following command within PowerShell:[Net.ServicePointManager]::SecurityProtocol=[Net.SecurityProtocolType]::Tls12to ensure that TLS1.2 is supported by the Windows Server. - We will utilize XAMPP for Windows version 7.1.30. Once the application installation is complete, ensure you enable Apache and MySQLas services by clicking on the tick box under Service within the XAMPP control panel, as shown in Figure 1.39:

Figure 1.39: XAMMP Control Panel showing Apache and MySQL running
- You can download the latest version of Mutillidae directly from https://github.com/webpwnized/mutillidae or by running the following command in PowerShell:
wget https://github.com/webpwnized/mutillidae/archive/refs/heads/master.zip -OutFile mutillidae.zip - Unzip the file and copy the folder to
C:\yourxampplocation\htdocs\<mutillidae>. - Open the
.htacessfile inside theMutillidaefolder and addAllow from 10.10.10.0/24under and the IP range are allowed. - Start the Apache and MySQL services by clicking on the Start button under Actions within XAMPP Control Panel. You should see the web application successfully deployed on your Windows Server, and it can be accessed by visiting
http://10.10.10.100/mutillidae/. - You will receive the database error messages relating to root access denial on MySQL. Open the XAMPP control panel, ensure that the MySQL service is up and running, and click on Shell and run the following steps to reset the root password, as depicted in Figure 1.40:
mysql –u root use mysql SET PASSWORD FOR root@localhost = PASSWORD('mutillidae') Flush privileges
Figure 1.40: Running the Shell from XAMPP and setting the MySQL password for the root user
- The final successful deployment of the vulnerable web application will lead to the screen shown in Figure 1.41:

Figure 1.41: Successfully accessing Mutillidae on Kali Linux within the same lab network
In case of error messages saying that the database is offline or something similar, you have to select Try to setup/reset the DB for Mutillidae. If you encounter any other error messages of missing files – ensure you disable Defender by running Set-MpPreference -DisableRealtimeMonitoring $true in PowerShell as administrator.
























































