The first step after understanding the problem and deciding to use Wireshark is the decision on where to locate it. For this purpose, we need to have a precise network illustration (at least the part of the network that is relevant to our test) and locate Wireshark.
The principle is basically to locate the device that you want to monitor, connect your laptop to the same switch that it is connected to, and configure a port mirror or in Cisco it is called a port monitor or Switched Port Analyzer (SPAN to the monitored device. This operation enables you to see all traffic coming in and out of the monitored device. This is the simplest case.
You can monitor a LAN port, WAN port, server or router port, or any other device connected to the network.
In the example presented in this diagram, the Wireshark software is installed on the laptop on the left and a server S2 that we want to monitor:
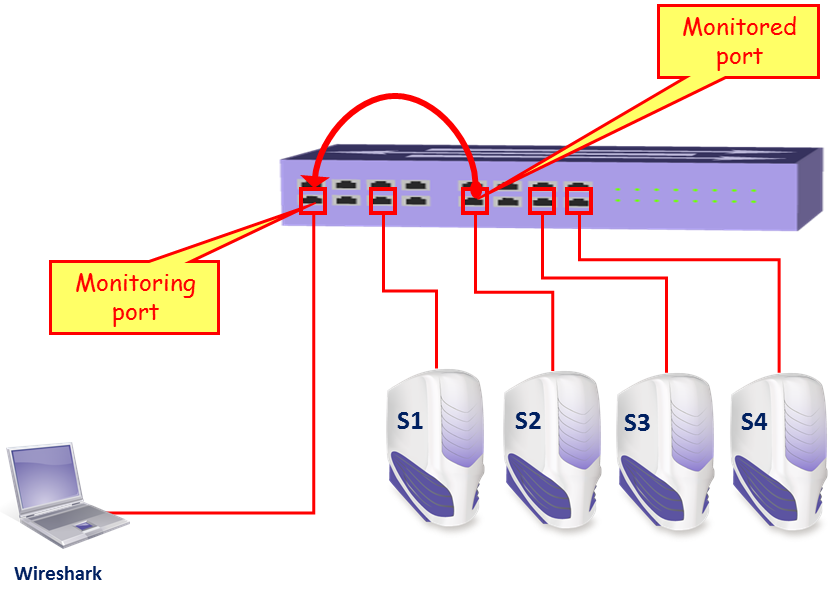
In the simplest case, we configure the port mirror in the direction as in the diagram; that will monitor all traffic coming in and out of server S2. Of course, we can also install Wireshark directly on the server itself, and by doing so we will be able to watch the traffic directly on the server.
Some LAN switch vendors also enable other features, such as:
- Monitoring a whole VLAN: We can monitor a server's VLAN, telephony VLAN, and so on. In this case, you will see all traffic on a specific VLAN.
- Monitoring several ports to a single analyzer: We can monitor traffic on servers S1 and S2 together.
- Filtering: Filtering consists of configuring whether to monitor incoming traffic, outgoing traffic, or both.



































































