Intrusion detection systems
As the name implies, an intrusion detection system (IDS) is responsible for detecting a potential intrusion and trigger an alert. What can be done with this alert depends on the IDS policy. When creating an IDS Policy you need to answer the following questions:
- Who should be monitoring the IDS?
- Who should have administrative access to the IDS?
- How incidents will be handled based on the alerts generated by the IDS?
- What's the IDS update policy?
- Where should we install the IDS?
These are just some examples of initial questions that should help in planning the IDS adoption. When searching for IDS, you can also consult a list of vendors at ICSA Labs Certified Products (www.icsalabs.com) for more vendor-specific information. Regardless of the brand, a typical IDS has the capabilities shown in the following diagram:
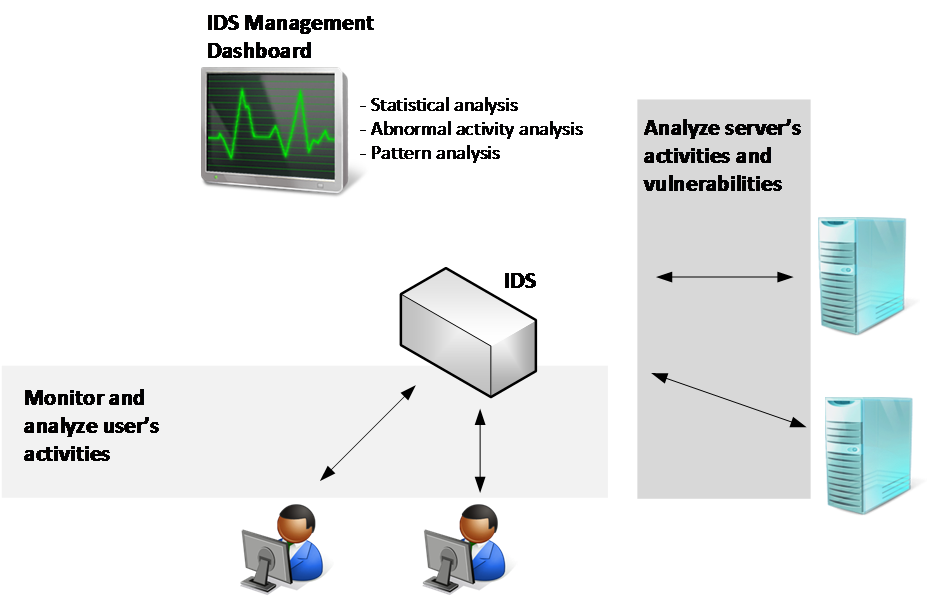
While these are some core capabilities, the amount of features will really vary according to the vendor and the method used by the IDS. The signature-based IDS...

























































