Implementing Azure AD Password Protection
Users often make poor choices when creating passwords, making them easy targets and victims of dictionary-based attacks.
This recipe will teach you how to implement Azure AD password protection in your environment’s AD tenancy. We will take you through customizing your smart lockout threshold and creating a global and custom banned password list.
Getting ready
This recipe requires the following:
- A device with a browser, such as Edge or Chrome, to access the Azure portal: https://portal.azure.com
- You should sign in with an account that has the Global Administrator role
- We will use Azure AD Premium licenses for this and future recipes
How to do it…
This recipe consists of the following task:
- Configuring password protection
Task – configuring password protection
Perform the following steps:
- From the Azure portal, go to Azure Active Directory and then click Security under the Manage section from the side menu.
- Select Authentication Methods under the Manage section from the side menu.
- Select Password protection under the Manage section from the side menu.
- From the Custom smart lockout section, set the Lockout threshold and Lockout duration in seconds properties as required; review the information in the tooltips by clicking on the i symbol:
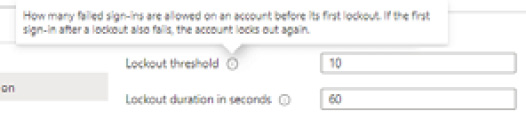
Figure 1.17 – Azure AD Premium P2 free trial activation
- From the Custom banned password section, select Yes, enter strings that are to be banned, and click Save; review the information in the tooltips by clicking on the i symbol. It can take several hours to apply the band password list:
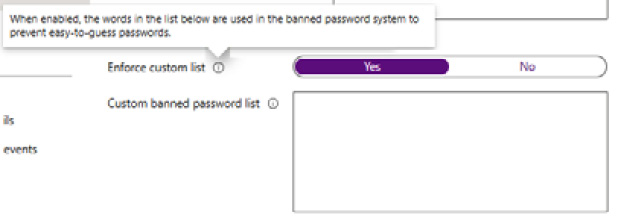
Figure 1.18 – Azure AD Premium P2 free trial activation
With that, you have configured password protection. This concludes the hands-on tasks for this recipe.
How it works…
You only need to add key terms such as password or contoso and the algorithm will automatically consider and block all variants of common character substitutions, such as Pa$sw0rd1! or C@ntos0!.
The banned password list may have a maximum of 1,000 key terms. The minimum length of a term string is 4 characters, where 16 characters is the maximum and are case-sensitive.
This recipe looked at customizing your smart lockout threshold to protect against brute-force attack methods. We also looked at creating a global and custom banned password list to protect against dictionary and password spray attacks and enforce the use of strong passwords.
Both of these measures, when implemented, can offer significant protection for your environment’s Azure AD tenancy.
See also
Should you require further information, you can refer to the following Microsoft Learn articles:
- Eliminate bad passwords using Azure Active Directory Password Protection: https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad
- Azure Active Directory fundamentals documentation: https://learn.microsoft.com/en-us/azure/active-directory/fundamentals

































































