Implementing Azure AD multi-factor authentication
We must adopt a zero-trust strategy in the perimeter-less world of cloud services and hybrid working more than ever. This means that we must assume breach and never trust, always verify.
Azure AD MFA provides an additional layer of defense; we never trust a single authentication method and must assume that the traditional password method has been compromised. Microsoft studies show that when you implement MFA, your accounts are more than 99.9% less likely to be compromised.
This recipe will teach you how to implement Azure AD MFA in your environment’s AD tenancy.
Getting ready
This recipe requires the following:
- A device with a browser, such as Edge or Chrome, to access the Azure portal: https://portal.azure.com.
- You should sign into the Azure portal with an account with the Global Administrator role.
- You will require Azure AD Premium licenses or trial licenses.
- If you have Security Defaults enabled, you will automatically have MFA enabled for all users and administrators using the free benefits of Azure AD. Using one of the paid Azure AD Premium licenses provides additional capabilities, such as the additional authentication methods of verification codes, text messages, or phone calls, as well as the following:
- Azure AD Premium P1: This license includes Azure Conditional Access for MFA
- Azure AD Premium P2: This license adds risk-based Conditional access to MFA through Information Protection
How to do it…
This recipe consists of the following task:
- Configuring MFA
Task – configuring MFA
Perform the following steps:
- From the Azure portal, go to Azure Active Directory, click Security in the Manage section from the side menu, and then click Multifactor authentication.
- From the Multifactor authentication | Getting started blade, click the Additional cloud-based multifactor authentication settings hyperlink under the Configure section heading:
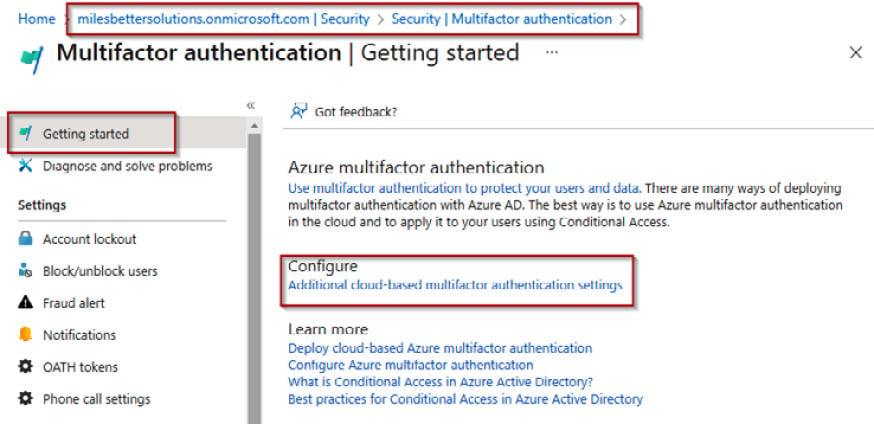
Figure 1.23 – Multifactor authentication | Getting started
- Two tabs are available from the new multi-factor authentication page that opens; select the user’s tab and then users to enable MFA:
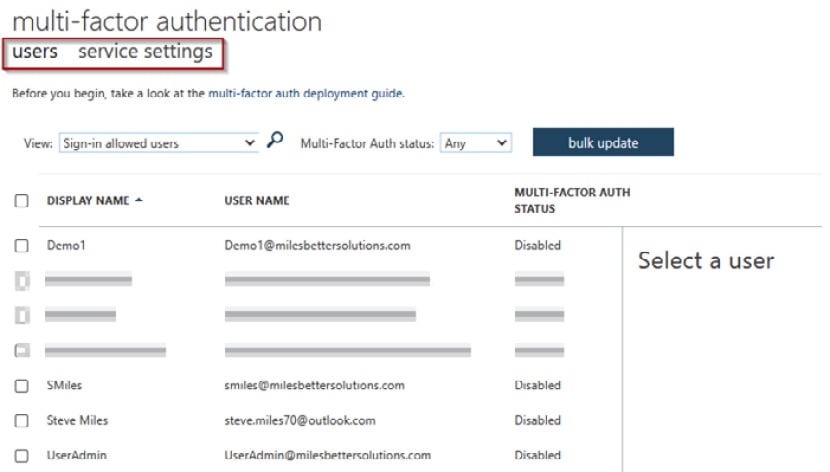
Figure 1.24 – MFA configuration screen
- From the user pane on the right, click on the Manage user settings hyperlink in the quick steps section:
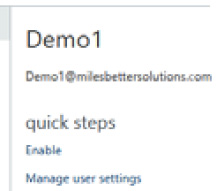
Figure 1.25 – MFA selected user pane
- On the Manage user settings pop-up screen, select any of the three options as required and then select save:
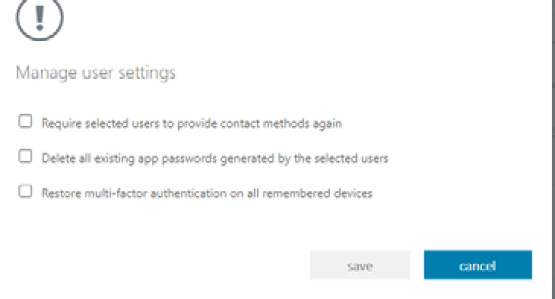
Figure 1.26 – Manage user settings pop-up screen
- Click Enable on the user pane screen from Step 4 of this recipe. From the About enabling multi-factor auth pop-up screen that appears, read the provided links, click enable multi-factor auth, and click close on the Updates successful screen.
- To disable a user for MFA, select the user from the user pane, click Disable in the quick steps section, select Yes on the pop-up screen, and click Close:
Figure 1.27 – Disabling MFA for a user
- You may bulk update enabling users for MFA by selecting the bulk update button and uploading a CSV file; a template file will be provided that you can download.
- Once the user tab configuration is complete, select the service settings tab in the multi-factor authentication browser window:
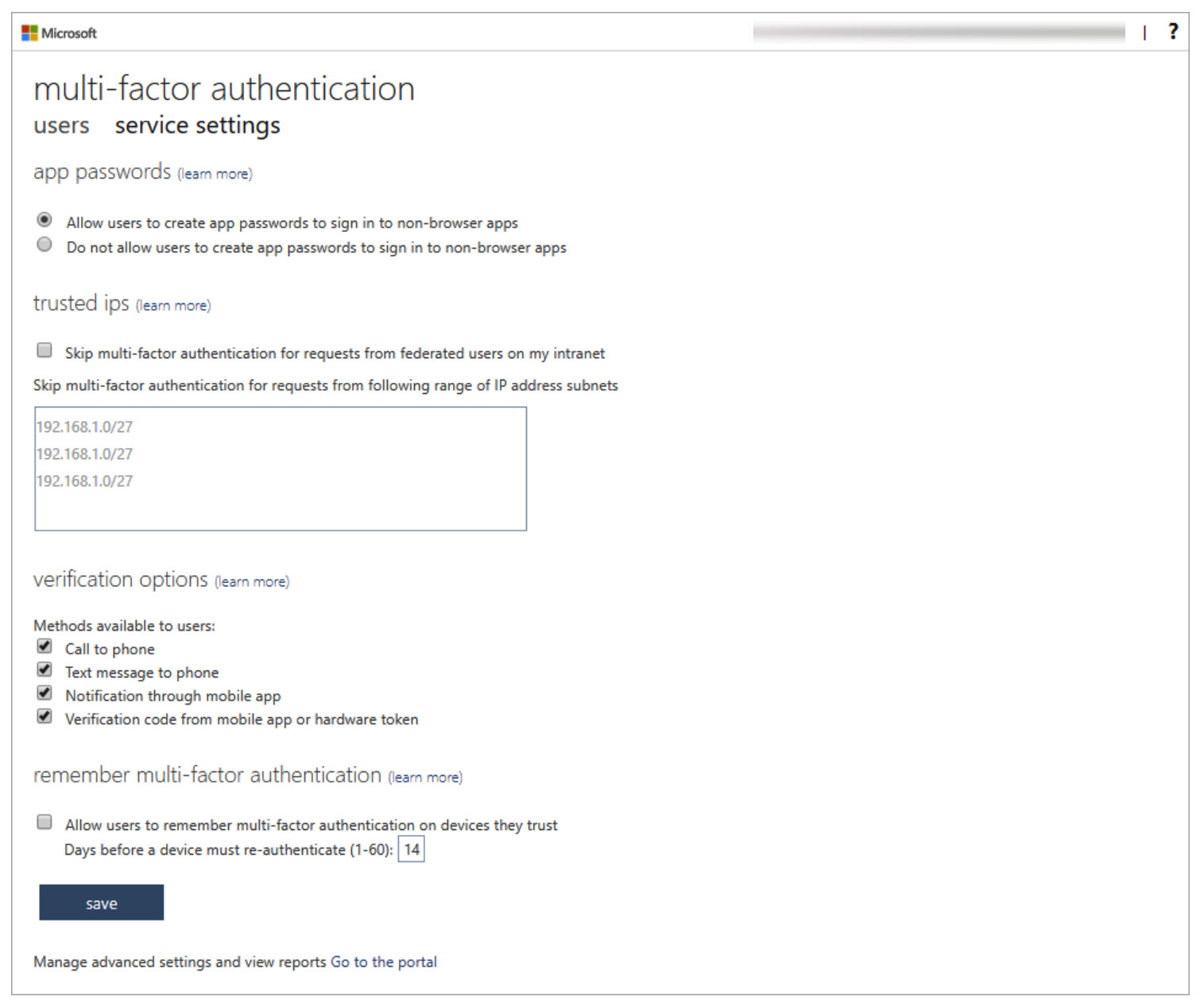
Figure 1.28 – The service settings tab’s settings
- From the service settings screen, set the required options and click save. Note the verification options section.
With that, you have configured MFA. This concludes the hands-on tasks for this recipe.
How it works…
In this recipe, we looked at how to enable Azure AD MFA in our environment’s Azure AD tenancy to provide an additional layer of security for users to sign to protect their identity from compromise.
Azure AD MFA requires us to provide one or more additional factors as a method to authenticate in addition to the password factor.
We can use the following authentication factors:
- Something we know (password)
- Something we own (device)
- Something we are (biometrics)
See also
Should you require further information, you can refer to the following Microsoft Learn articles:
- Secure Azure Active Directory users with Multi-Factor Authentication: https://learn.microsoft.com/en-us/training/modules/secure-aad-users-with-mfa/
- Features and licenses for Azure AD Multi-Factor Authentication: https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-licensing
- Azure Active Directory fundamentals documentation: https://learn.microsoft.com/en-us/azure/active-directory/fundamentals
































































