Getting started with policy design
When designing your strategy for policy management with Microsoft Intune, it is important to take the right approach.
By starting with a security baseline, we get well-tested and secure sets of policies; you can even disable or remove individual settings in the security baseline if they do not suit your organization. When you have deployed the security baseline, you can start adding other policy types that suit your security or configuration needs.
There are several policy types in Microsoft Intune. In the following list, you can see the different policy types and the order in which you should start creating policies:
- Configure the security baseline.
- Configure the policy from the Endpoint Security blade.
- Configure the policy from the Settings catalog.
- Configure the administrative template.
- Configure the device configuration.
- Leverage a custom policy as a last resort.
Just remember that there are no right and wrong approaches, but if you’re undertaking a migration from Active Directory GPOs to MDM settings management, it might be a good time to start afresh and see what you need to configure instead of taking the legacy GPO settings of your on-premises environment with you. Sometimes, organizations do not even know why they implemented a specific policy setting back when they originally created it. Perhaps the person responsible for implementing this policy setting is no longer even with the company and did not leave any documentation on why the setting was configured the way it was in the first place.
As there is no conflict handling in the MDM stack, you might inadvertently create a conflict between two settings coming from two different policies to the same user or device. These could be from the same policy type or different policy types, so it is important to spot and monitor any conflicting policies.
- In order to monitor any conflicting policies, head to the Microsoft Intune admin center, and under each device, go to Home | Configuration:
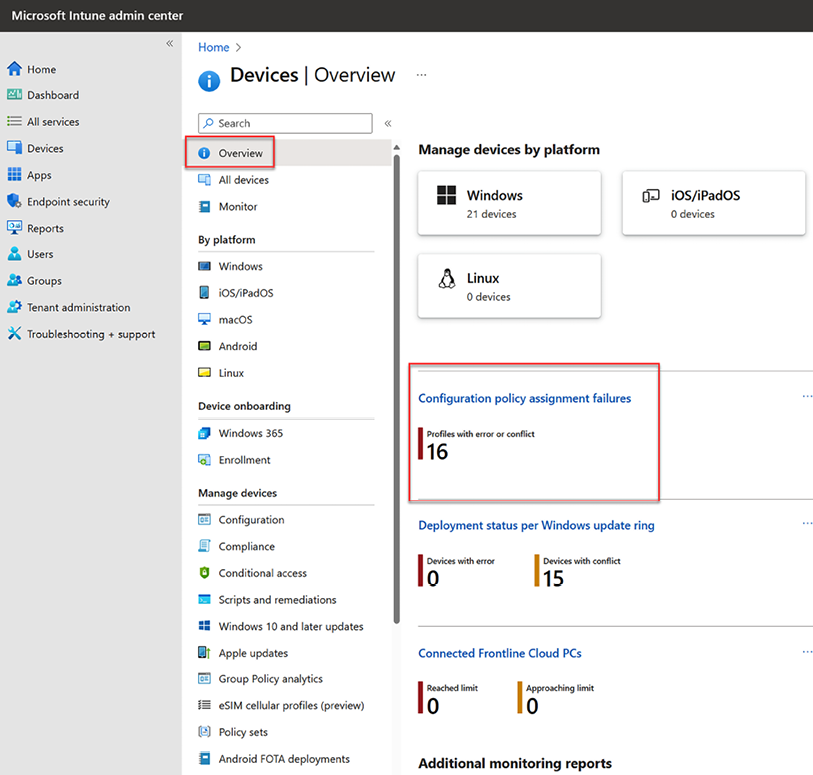
Figure 9.14: Configuration policy status
- You can see the policy that has conflicts and the work required to remediate the conflict:
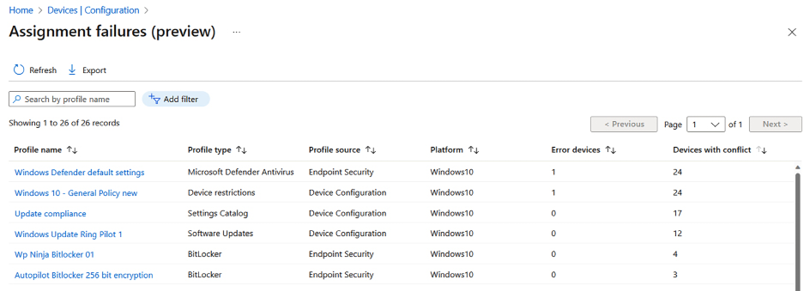
Figure 9.15: Policy conflict
- When drilling down into the policy, you can see which settings are in conflict. In this case, I see that there is a conflict between a policy in the Endpoint Security blade and the Antivirus – Windows Defender Antivirus policy type:
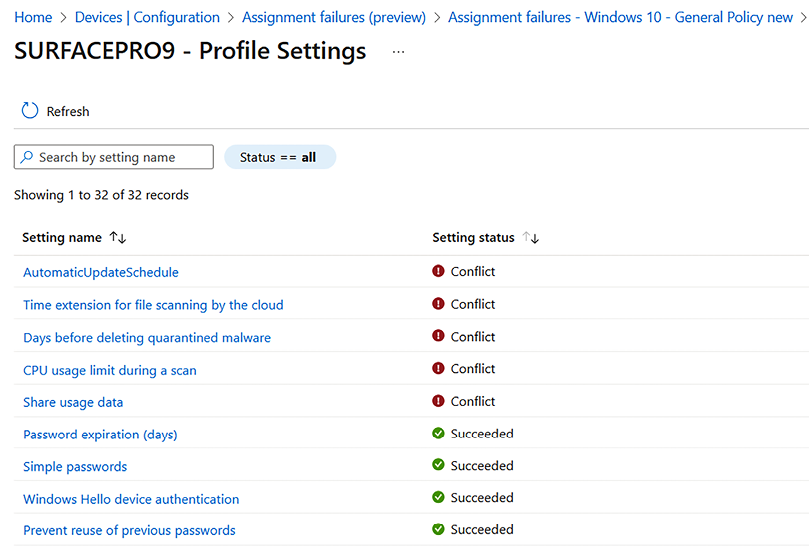
Figure 9.16: Profile settings
- Going to that policy, you can see in the Per-setting status blade that the top line, CPU usage limit per scan, has conflicts. When you find conflicts, you need to go into the policies with conflicts and change the conflicting settings so they are only configured in one policy:
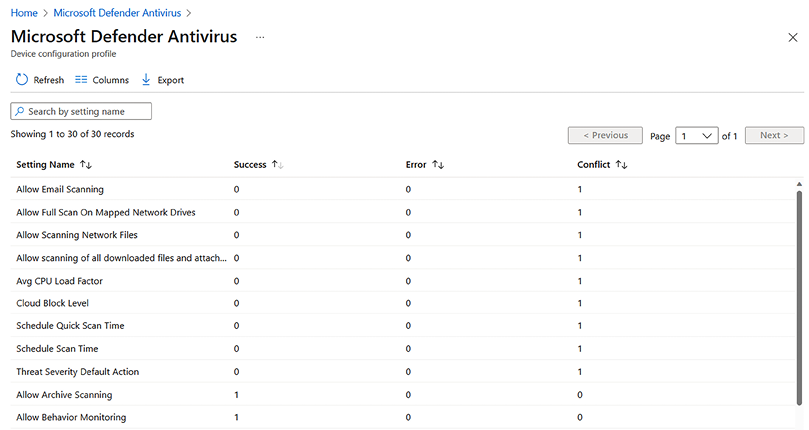
Figure 9.17: Per-setting status
Let’s now have a look at how to implement different policy types.
































































