The world of Shodan
There is a site you probably already know about, and if you don’t, prepare to spend a few hours exploring its treasures: shodan.io. Back in my day, when you saw a device firing off frames on the wire, you knew it was a computer. Today, a surprising variety of devices are network-capable, and your refrigerator may very well be another budding leaf at the end of sprawling branches of this global tree we call the internet. The rapid proliferation of this connectedness and its penetration into our daily lives is concerning for us security nerds, but we’re not going to wax philosophical today. The point is, it occurred to some clever folks along the way that crawling the internet to see what’s open and ready to chat will be very interesting as new leaves start popping up. Enter Shodan.
The name started as an acronym from a classic 1990s video game series, System Shock. SHODAN stands for Sentient Hyper-Optimized Data Access Network. In a classic sci-fi turn of events, SHODAN was originally artificial intelligence whose purpose was to help people …but something went wrong. You get the idea. Think Skynet from the Terminator series or V.I.K.I. from I, Robot. The AI goes wonky and decides humans are mere infestuous bugs for squashing. The common thread is that the AI was granted entirely too much access to global systems in order for it to do its job. As SHODAN grabbed control over numerous disparate systems, shodan.io’s creator John Matherly figured it’s an appropriate reference.
To be clear, Shodan isn’t a website that is hell-bent on the annihilation of all humankind (but that would be an awesome movie). The “disparate systems” part is the all-too-creepy reference here, as Shodan crawls the internet, just poking around the unlocked doors tucked away in the back alleyways. If you want to find webcams, a fridge that’s running low on milk, or – more terrifyingly – SCADA systems inside massive plants, then Shodan is the place to check it out. What the hacker in you should be realizing is something like, what about an SSH server on unexpected ports, in an attempt to hide in plain sight? Excellent thinking. We want to focus on our client’s resources that were already sniffed by someone else. Suppose your client really is running SSH on port 2222 (this is surprisingly common, as Shodan will show you). We have a head start on the discovery phase of our assessment, and once again, we didn’t send any packets. A Shodan crawler sent the packets.
The general principle here is banner grabbing. Banners are nothing more than text-based messages that greet the client connecting to a particular service. They’re useful for the rightful administrators of these servers to catalog assets and troubleshoot problems. Suppose you have a large inventory of servers hosting a particular service and you want to validate the version that’s running on each host. You could type up a small script that will initiate those connections, find the version number in the banner, and put it all in a tidy list on your screen. They are also extremely useful for narrowing our focus while we are developing the attack on our target. We’ll see hands-on banner grabbing later when we’re sitting down at Kali. In the meantime, we’re going to take advantage of the fact that someone has already taken a look at what the internet looks like down to the service level, and our job is to see what our client is telling the world. You’ll be surprised again and again during assessments by how much the clients do not know about what’s floating around out there with their name on it.
Is banner grabbing a worthy finding for a pen test?
Findings are graded by their overall risk rating. Businesses consider a couple of things when it comes to risk management: how likely and how impactful a compromise would be. Is a vulnerability very unlikely to be exploited, and if it is, will it threaten the entire organization? That’s going to be considered higher risk. Banner grabbing would fall in the category of very likely (due to its simplicity), and very low impact. Remember that an important part of your job is educating your client on how these things work. Yes, it will be one of the low-risk findings. But if your banner grab narrowed your focus and saved you time, thus giving you more time after the compromise to do even more movement and loot-grabbing, it belongs in the report. It’s a part of the attack!
Shodan search filters
You can start simple, such as punching in an IP address or a service name. For example, we could try Remote Desktop Protocol (RDP) or Samba. To turn this global eye into a fine-tuned microscope, however, we need to apply search filters. The format is very simple: you merely separate the name of the filter from its query with a colon (:). A real handy way to fine-tune your results is to negate a particular query by putting a dash (-) before the filter name. Let’s take a look at the filters available to us, and then we’ll go over some examples.
asn: Search by autonomous system number. An autonomous system (AS) is a group of IP prefixes operated by one or more entities for maintaining one clear routing policy, allowing these entities to exchange routes with other ISPs. This search is useful when you are looking for hosts under the control of one or more such entities as defined by their assigned ASN.city: Search by the city where the host is located.country: Search by country with alpha-2 codes as per the ISO 3166 standard.geo: Allows you to specify geographical coordinates. Linking a specific host to its geographical coordinates is notoriously iffy, so it’s best to establish a range with this filter. Draw a box over the area you want to search and grab the lat/lon pairs for the top-left corner of the box and the lower-right corner of the box. For example, searchinggeo:12.63,-70.10,12.38,-69.82will return results anywhere on the island of Aruba.has_ipv6: Searches for IPv6 support; expectstrue(or1) orfalse(or0).has_screenshot: Returns results where a screenshot was captured. This is useful for things such as RDP and VNC. Expects the Booleantrue/false(1/0).has_ssl: Shows services with SSL support. Expectstrue(or1) orfalse(or0).hash: Each page that’s grabbed by Shodan is hashed. This could be handy for looking for pages with the exact same text on them, but you’ll probably use this with the negation dash (-) and a zero to skip results where the banners are blank, like this:-hash:0.hostname: Specify the hostname or just a part of it.ip: The same asnet, this lets you specify an IP range in CIDR format.isp: Take a look at a specific ISP’s networks.net: The same asip– this lets you specify an IP range in CIDR format.org: This is where you specify the organization’s name.os: Very handy indeed – specify the operating system.port: Check specific ports. Negating this filter is especially useful for finding services that are operating on non-standard ports. For example,ssh -port:22will find all instances of SSH on anything other than the standard SSH port.product: A crucial option for narrowing down a specific product running the service. For example,product:Apache -port:80,443will find any Apache server on non-standard ports.version: Useful for targeting specific product version numbers.Note
We’re covering the filters that are available to basic users. There are more sophisticated filters available to small business and enterprise accounts if such a thing is within your budget.
Let’s take a look at how we can whittle away at our results and home in on what we need. First, let’s say our target is in Mexico City:
city:"Mexico City"
On second thought, I want to make sure I cover the region around and including Mexico City. So, I’ll try this instead:
geo:19.58,-99.37,19.21,-98.79
Now, I want to look for SSH on any non-standard port:
geo:19.58,-99.37,19.21,-98.79 ssh -port:22
And I only want Debian hosts:
geo:19.58,-99.37,19.21,-98.79 ssh -port:22 os:Debian
Finally, suppose I know the subnet for my target is 187.248.0.0/17:
geo:19.58,-99.37,19.21,-98.79 ssh -port:22 os:Debian net:187.248.0.0/17
With that, I hit Enter and see what Shodan has in store for me:
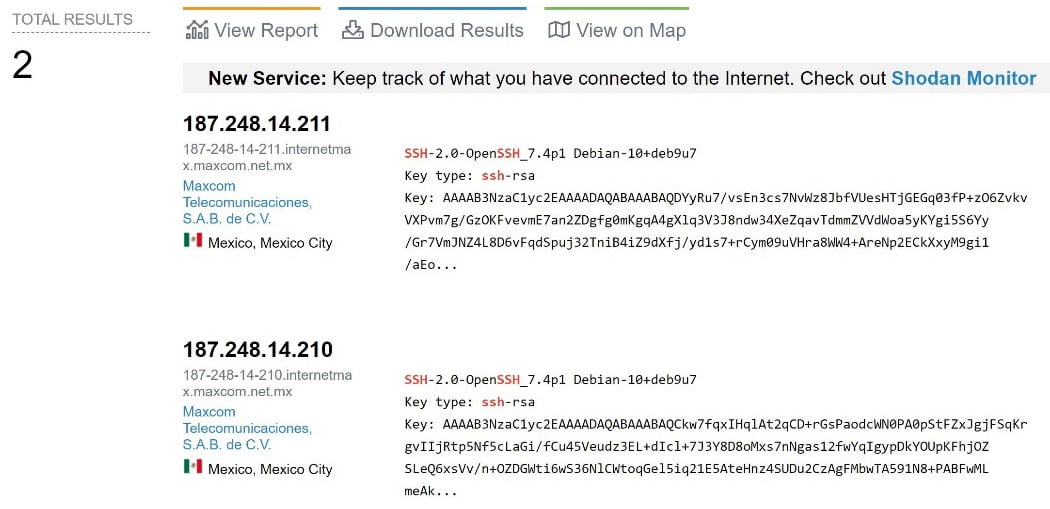
Figure 1.10 – Homing in on my targets
When I started looking at the Mexico City region, I had 1.5 million results to sift through. My fine-tuning reduced that list to only two servers. This is a fully random example for demonstration purposes – when you’re researching for a specific client, you’ll be trying the org filter, perhaps the asn filter, and whatever else you have to go on.

























































