Testing NIDS with tmNIDS
tmNIDS is a GitHub project maintained by 3CoreSec. tmNIDS is a simple framework designed for testing the detection capabilities of NIDS such as Suricata and Snort. The tests inside tmNIDS are designed to align with rulesets compatible with the ET community. The ET community builds and shares Suricata rules to detect a wide range of attacks such as web-based attacks, network attacks, and DDoS attacks. In this section, we will learn to simulate attacks using tmNIDS and we will visualize them on the Wazuh dashboard. We will cover these points in the following subsections:
- Lab setup
- Installing tmNIDS on Ubuntu Server
- Testing for a malicious User-Agent
- Testing for a Tor connection
- Test everything at once
Lab setup
In this lab setup, we have two devices: Ubuntu Server running the Wazuh agent, Suricata IDS, and tmNIDS, and second, the Wazuh server installed using a VM OVA file. The lab design is in the following figure.
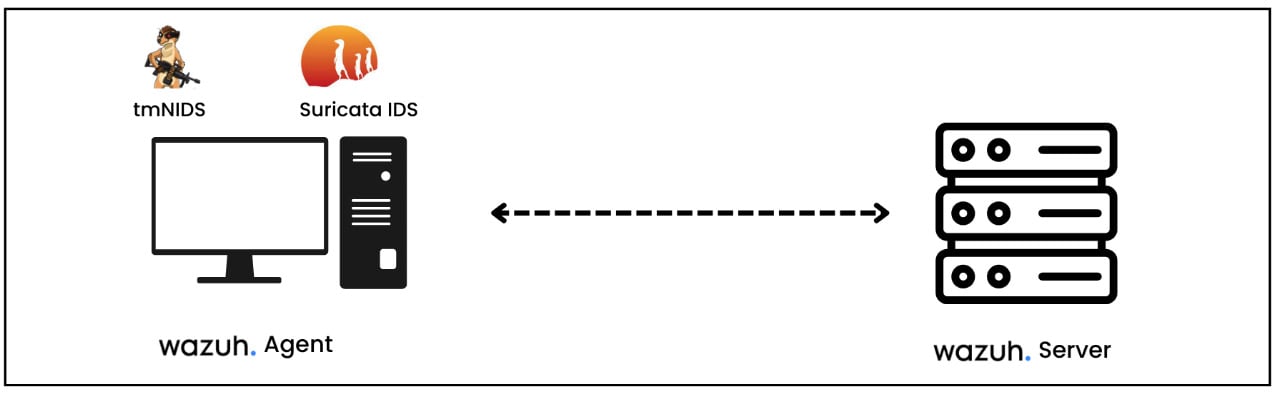
Figure 1.28 – Lab set for testing Suricata IDS rules using tmNIDS
Installing tmNIDS on Ubuntu Server
The source code of the tmNIDS project is published on GitHub (https://github.com/3CORESec/testmynids.org). To install tmNIDS, we can run a curl command to download the packages:
curl –sSL https://raw.githubusercontent.com/3CORESec/testmynids.org/master/tmNIDS> -o /tmp/tmNIDS && chmod +x /tmp/tmNIDS && /tmp/tmNIDS
Let’s break this down:
curl: This is a utility tool that initiates a request to download data from the specific URL.-sSL: Here,-sstands for showing progress without any output. TheSflag will show errors ifcurlencounters any problem during the request and theLflag represents redirection.-o /tmp/tmNIDS: This informscurlto save downloaded files as tmNIDS in the/tmpdirectory.chmod +x /tmp/tmNIDS: It changes the file permissions of the downloaded file to executable.
Once the package has been executed, you will see a list of 12 tests for Suricata IDS as in the following diagram.
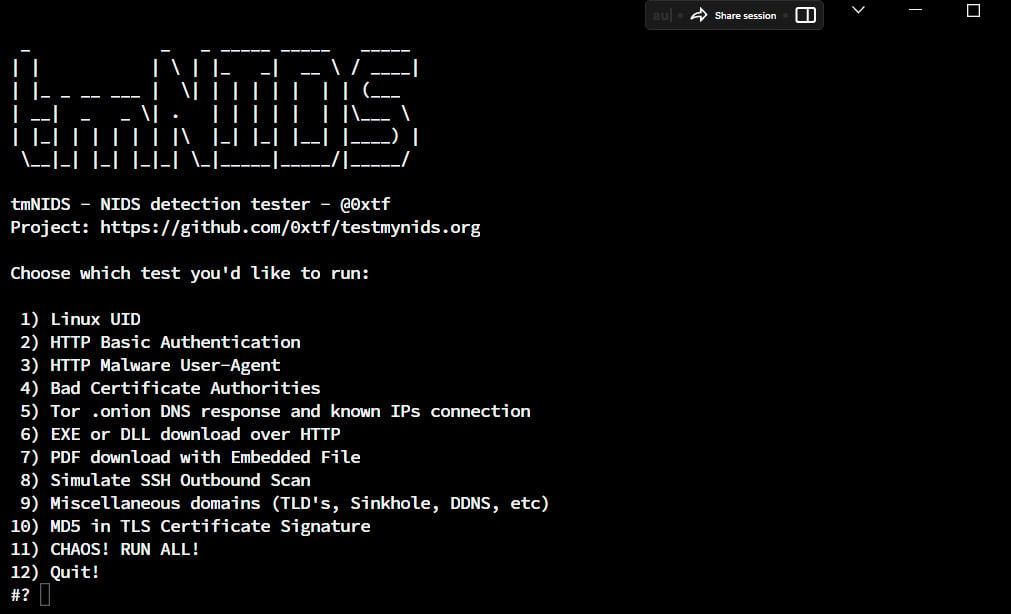
Figure 1.29 – Visualizing tmNIDS detection tester
So, now that our tmNIDS is ready, we can start testing our Ubuntu Server (running Suricata IDS) against multiple attacks as explained in the next sections.
Testing for a malicious User-Agent
In this scenario, we will execute test 3 from the tmNIDS tests, which is HTTP Malware User-Agent. For every HTTP request, there is a User-Agent header that describes the user’s browser, device, and OS. When an HTTP web browser sends a request to a web server, it inserts this header to identify itself to the server. The User-Agent string usually contains information such as the browser’s name and version, OS, device type, and sometimes extra data such as rendering engine details. If you take a closer look at the HTTP header using Google developer mode, you will find the User-Agent information:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36
This User-Agent string says that the browser is running on a Windows 10 64-bit system, using the Chrome browser (version 96.0.4664.45) with rendering engines associated with both WebKit (Safari) and Gecko (Firefox).
To test the Ubuntu Server (running Suricata IDS) against HTTP Malware User-Agent test, enter 3 on the tmNIDS prompt.
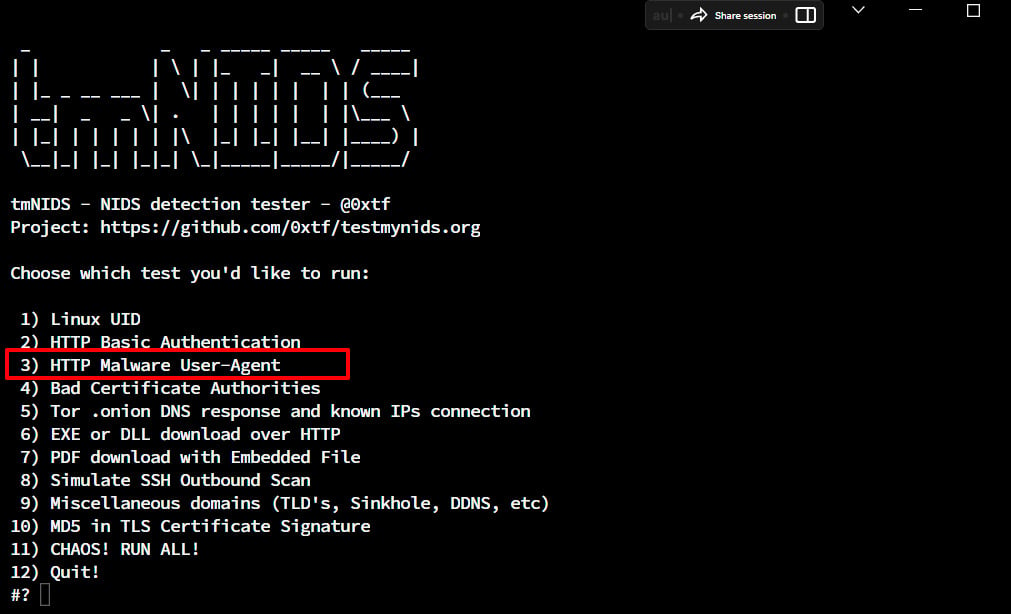
Figure 1.30 – Choosing option 3 from the tmNIDS detection tester
Now, let’s visualize the alerts on the Wazuh dashboard. You can navigate to the Security Alerts module and select the endpoint. You can find the alerts as shown in the following diagram.
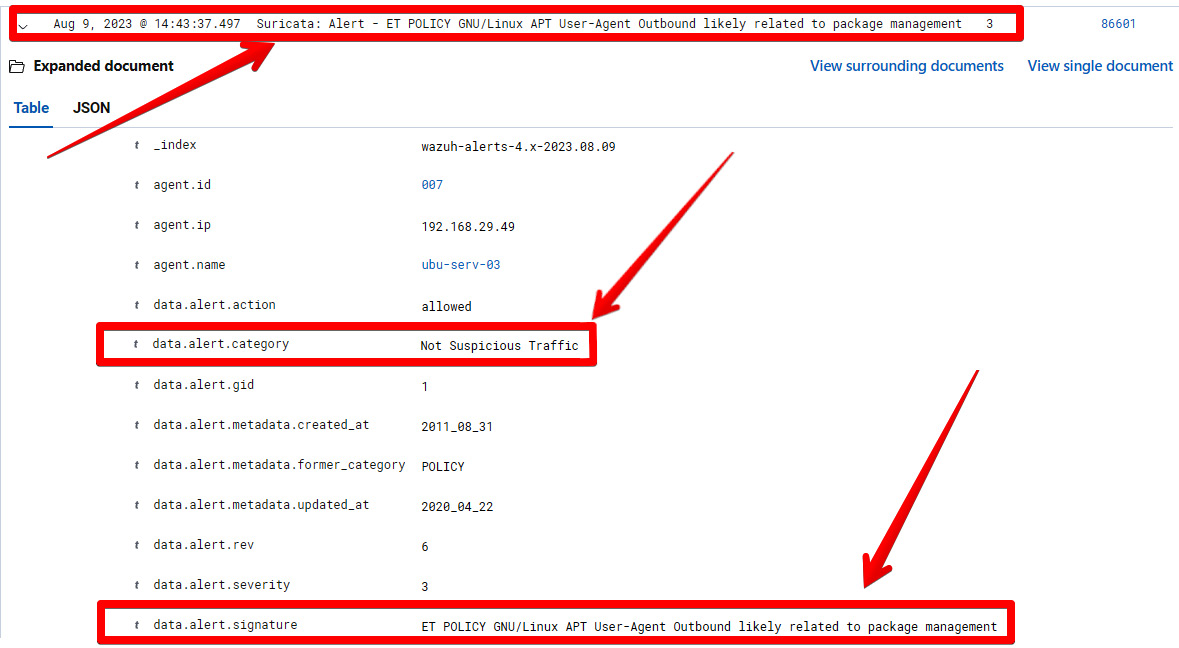
Figure 1.31 – Suricata alert against a suspicious User-Agent
Let’s break some of the following down:
Suricata: Alert – ET POLICY GNU/LINUX APT User-Agent Outbound likely to package management: This represents the Security alerts name and signaturedata.alert.category : Not Suspicious Traffic: This represents the category of the ET ruleset categorydata.alert.signature : ET POLICY GNU/Linux APT User-Agent Outbound likely related to package management: This suggests potential APT-related outbound network activity, possibly tied to package management.
After successfully testing HTTP Malicious User-Agent and visualizing alerts on the Wazuh dashboard, we will test the Tor connection in the next section.
Testing for Tor connection
In this scenario, we will execute test 5, which is Tor. Tor is a decentralized, anonymous network that users can use to browse the internet privately and safely. However, it is often used by hackers, malicious actors, and cybercriminals who access the dark web and sell stolen data and illegal goods online. Its anonymity features can keep attackers’ identities secret, making it hard for the government to track their actions and hence, it is important for every organization to block any traffic from Tor services. The most popular Tor application is Tor Browser. When anyone accesses any website through the Tor Browser, it goes through proxy nodes, making it difficult for anyone to intercept. From a cybersecurity point of view, we can build a list of IP addresses of such nodes and eventually block them, or block Tor-based applications based on their signatures.
To test this scenario, go back to the tmNIDS prompt and enter 5. The Tor attack will be executed on our Ubuntu Server running Suricata IDS.
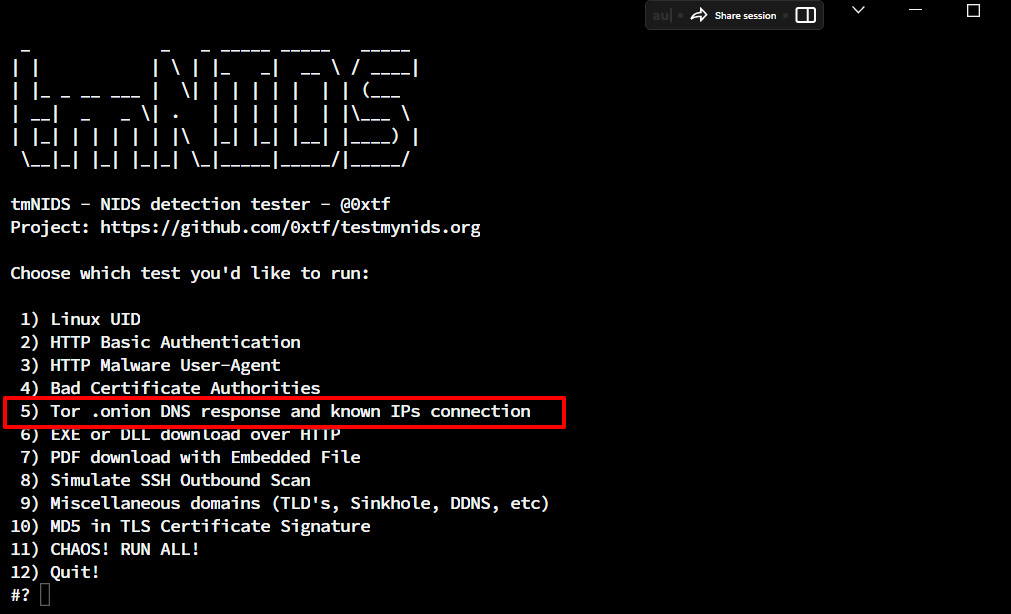
Figure 1.32 – Choosing option 5 from the tmNIDS detection tester
To visualize the alert, navigate to the Security Alerts module of Wazuh and check for the relevant alerts shown in the following diagram.
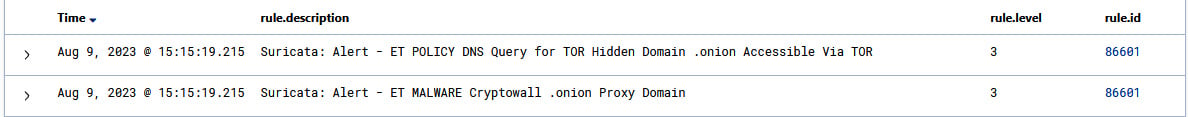
Figure 1.33 – Suricata alert against Tor hidden traffic
Both have been detected by the Suricata ET ruleset. There are two rule descriptions:
Suricata: Alert - ET POLICY DNS Query for TOR Hidden Domain .onion AccessibleVia TORSuricata: Alert - ET MALWARE Cryptowall .onionProxy Domain
We have successfully tested the Tor .onion DNS response test and visualized the alerts on the Wazuh manager. In the next section, we will run all the tests at once and visualize the alerts.
Testing everything at once
Now, this is like a non-stop rifle. You basically launch all the tests at once. To start, type 11 under the tmNIDS tests prompt and monitor the events on the Wazuh manager.
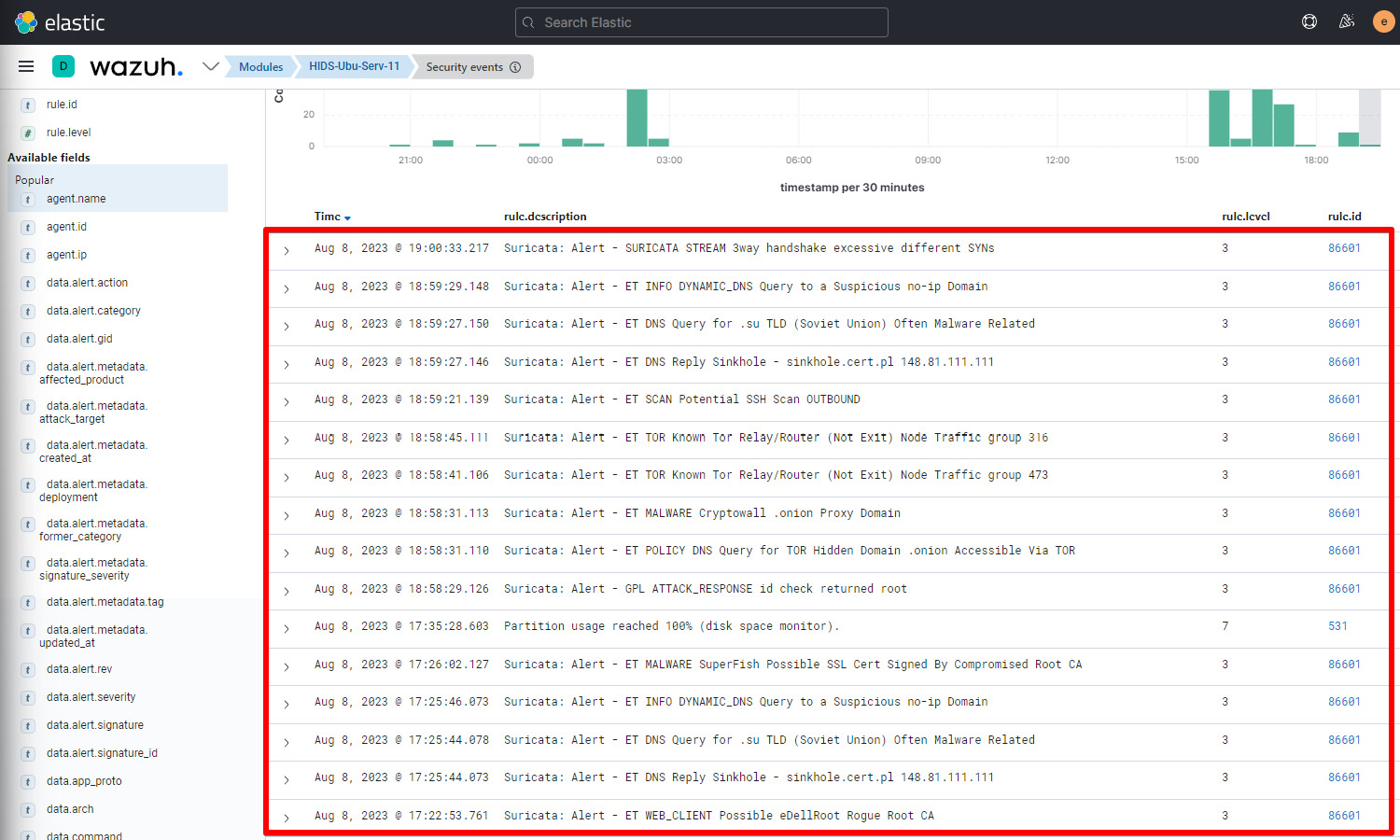
Figure 1.34 – Suricata alerts against all the tmNIDS tests
As you can see, we have received alerts against all the tests listed in the tmNIDS detection tester. This shows that our Suricata IDS along with the ET ruleset are effective against attacks launched by the tmNIDS project.

































































